
Hey there, let’s dive deep into the world of password sniffing and understand how hackers operate to steal sensitive information like login credentials. Cybersecurity is more critical than ever, with hackers constantly finding new ways to exploit vulnerabilities and gain unauthorized access. In this guide, we’ll cover everything from what password sniffing is to the tools hackers use and how you can protect yourself against such attacks.
Table of Contents
What is Password Sniffing?
So, what exactly is password sniffing? It’s a sneaky technique used by hackers to intercept and capture passwords as they travel across a network in plain text. “Password sniffing” is a term used to describe the unauthorized capturing of passwords or other sensitive information as it travels over the network. Imagine someone eavesdropping on your conversations, but in the digital world. Hackers exploit weaknesses in network protocols or devices to snatch up your login credentials without you even realizing it.
This is a security concern because if someone successfully “sniffs” the passwords, they can gain unauthorized access to accounts or systems. To protect against password sniffing, it’s important to use a secure connection like HTTPS, avoid using public Wi-Fi for sensitive activities, and use strong, unique passwords.
Types of Password Sniffing Attacks
Now, let’s talk about the different types of password sniffing attacks hackers use to get their hands on your credentials.
1. Active Sniffing
Active sniffing refers to instances where the attacker interacts directly with the network or its components to capture data.
1. LAN Sniffing
LAN (Local Area Network) sniffing involves monitoring network traffic within a local network. Attackers can use tools like Wireshark or tcpdump to capture packets, including passwords and authentication credentials, as they travel between devices within the LAN.
2. Protocol Sniffing
Protocol sniffing focuses on capturing and analyzing specific network protocols, such as FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), or SNMP (Simple Network Management Protocol). Attackers target these protocols to intercept sensitive information, including login credentials transmitted in plaintext.
3. ARP (Address Resolution Protocol) Spoofing
ARP spoofing, also known as ARP poisoning, is a technique where the attacker sends falsified ARP messages to associate their MAC address with the IP address of a legitimate device on the network. This allows them to intercept and modify data packets, including passwords, exchanged between the targeted device and other network nodes.
4. TCP Session Hijacking
TCP (Transmission Control Protocol) session hijacking involves taking control of an established TCP connection between two devices. Attackers exploit vulnerabilities in TCP/IP protocols or use tools like TCPStealer to intercept and manipulate data packets containing login credentials, bypassing authentication mechanisms.
2. Passive Sniffing
Passive sniffing involves monitoring network traffic without directly interacting with network components, making it harder to detect.
1. Application-Level Sniffing
Application-level sniffing targets specific applications or services running on a network. Attackers use tools like Ettercap or Cain & Abel to capture data exchanged between applications and extract passwords or sensitive information, especially if the applications communicate using unencrypted protocols.
2. Web Password Sniffing
Web password sniffing focuses on capturing passwords and authentication tokens transmitted over HTTP or HTTPS protocols. Attackers can deploy malicious scripts or tools like sslstrip to intercept unencrypted HTTP traffic or bypass HTTPS encryption to capture login credentials from web forms.
How Do Hackers Perform These Attacks?
Let’s see how hackers pull off these password sniffing attacks.
1. Network Monitoring
Hackers use specialized software to keep an eagle eye on network traffic. They look for weak spots where they can sneak in and intercept plaintext passwords. These are some tools for Network Monitoring:
- Wireshark: This tool is like a detective, capturing and analyzing data packets to uncover sensitive information.
- Tcpdump: Think of it as a silent observer, quietly capturing network traffic for analysis.
2. Exploiting Protocol Weaknesses
Those network protocols we mentioned earlier? They have weaknesses that hackers exploit to capture your passwords. Below are some common protocol vulnerabilities exploited:
- HTTP: Basic Authentication: Your credentials are encoded but not encrypted, making them easy pickings for hackers.
- FTP: Clear Text Authentication: It’s like sending your passwords on a postcard for anyone to read.
- SMTP: Unencrypted Email Transmission: Your email credentials are out in the open, ripe for the taking.
3. Compromising Devices
Hackers don’t stop at protocols; they target devices too. By gaining unauthorized access to routers or switches, they can install sniffing tools or tweak network settings for their nefarious purposes. These are some device exploitation techniques:
- Router Compromise: Hackers manipulate router settings to redirect traffic through their own devices, capturing sensitive data along the way.
- Switch Manipulation: By exploiting vulnerabilities in switches, hackers can mirror ports to capture all network traffic, including passwords.
Tools Used by Hackers
Now that you know how hackers operate, let’s talk about the tools of their trade.
1. Wireshark: The Swiss Army Knife of Password Sniffing
Wireshark is like a supercharged magnifying glass for hackers. It lets them capture, analyze, and decode data packets to reveal plaintext passwords and authentication credentials. Features of Wireshark:
- Packet Capture: Snatching up data packets flying through the network.
- Protocol Decoding: Unraveling complex protocols to uncover sensitive information.
- Traffic Filtering: Zeroing in on specific keywords or protocols related to authentication.
2. Cain and Abel
Cain and Abel is another potent tool in a hacker’s arsenal. It’s not just about sniffing passwords; it can crack them too. Features of Wireshark:
- ARP Poisoning: Redirecting network traffic for interception.
- Packet Sniffing: Capturing and analyzing data packets for plaintext passwords.
Hacking activity: Capturing Passwords In Insecure Web Apps Using Wireshark
Wireshark is a tool that can capture all kinds of information as it moves across a network. This includes things like usernames, passwords, emails, and other personal details. Think of it like taking snapshots of what’s happening on your network.
When we’re talking about “sniffing,” we mean capturing data as it travels through the network. This data can include passwords for different types of services like websites (HTTP), file transfers (FTP), or remote access (Telnet).
Now, let’s talk about how we use Wireshark to capture passwords. In this tutorial, I am using the Ethernet interface (eth0), while you can use the Wi-Fi interface (wlan0) as well.
Step 1: Open Wireshark and start capturing network traffic. It’s like turning on a camera to record everything that’s happening on your network.
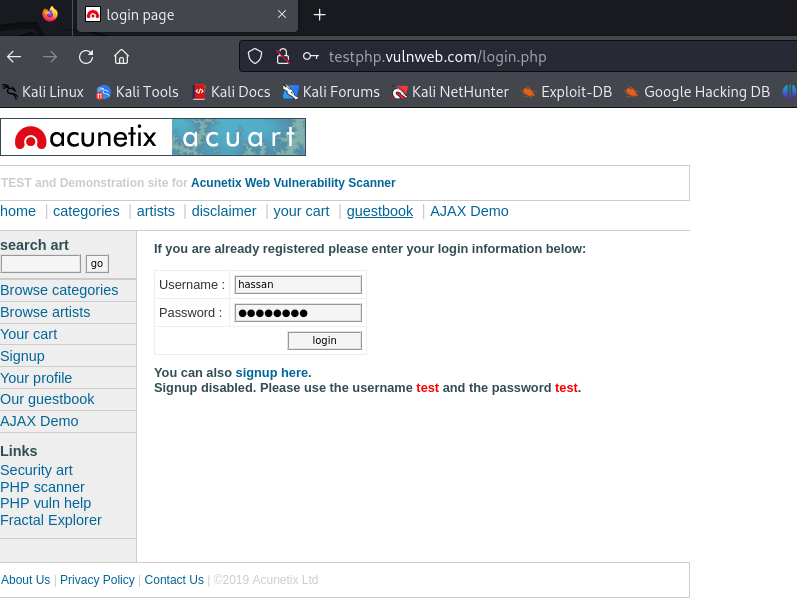
Step 2: While Wireshark is running, visit any website and log in with your username and password. I am using a vulnerable website for this i.e., vulnweb.com
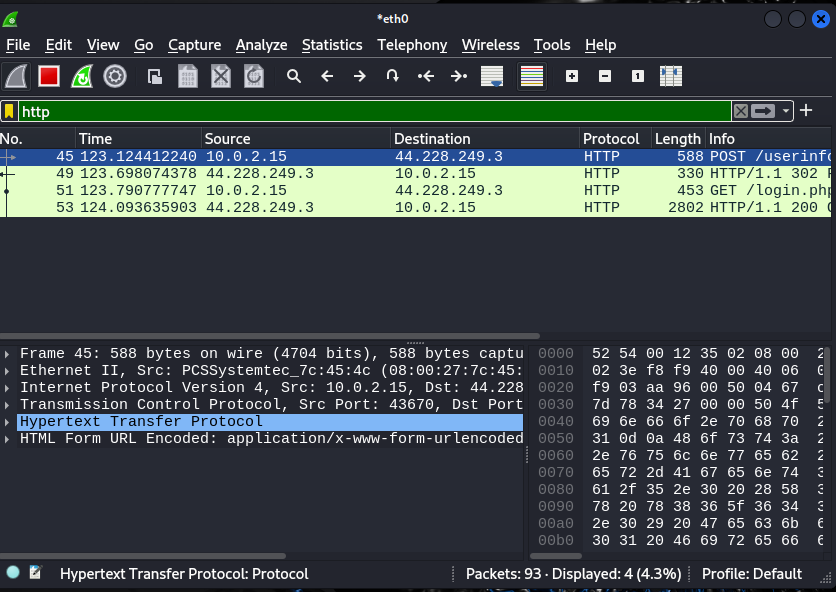
Step 3: After logging in, Use filters in Wireshark to focus on the data packets that contain login information.
Step 4: Then, specifically look for HTTP packets, which are used for web communication. These packets might contain login details.
Step 5: Within the HTTP packets, search for form data that users submit on websites. This form data includes things like usernames and passwords.
Step 6: Wireshark lets us filter packets based on how the form data was sent. There are two main methods: GET and POST. We first check the GET method to see if it contains the login info.
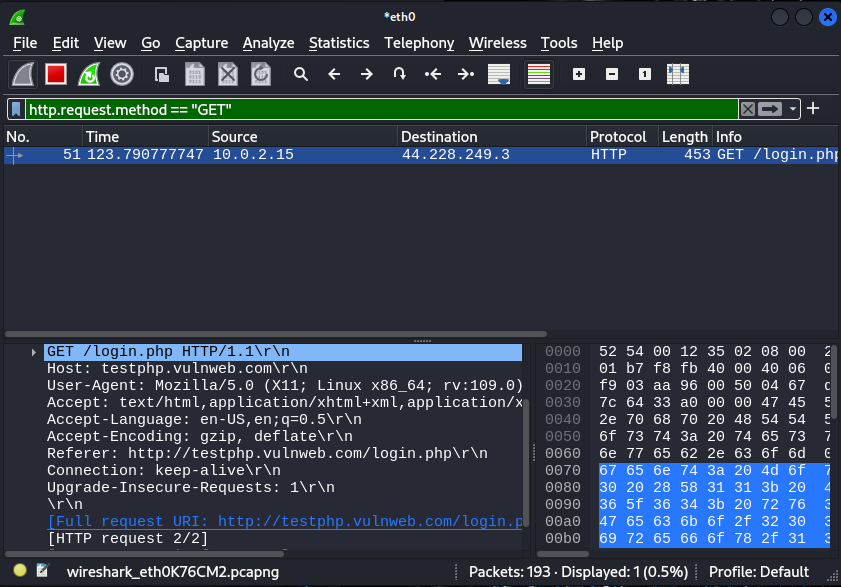
Step 7: If we don’t find the login data with GET, we switch to the POST method filter. This method often carries form submissions, including passwords.
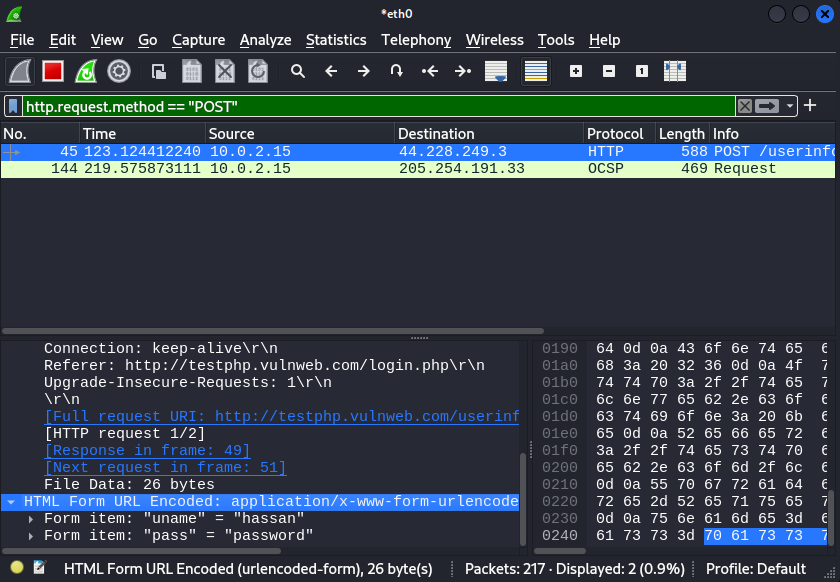
By applying these filters in Wireshark, we can locate packets that contain the login credentials you used on the website. These packets show us the username (“hassan“) and password (“password“) I entered during the login process.
Prevention Measures: Protecting Yourself Against Sniffing Attacks
Now that you’ve seen how hackers operate, let’s talk about how you can defend against password sniffing.
1. Encryption: Locking Your Data
Encrypting your data is like putting it in a safe with multiple locks. It scrambles your passwords and sensitive information, making them unreadable to prying eyes. Some Best Practices for encryption are:
- SSL/TLS Certificates: Secure your connections with valid certificates to encrypt data in transit.
- VPN Tunnels: Tunnel your traffic through encrypted channels for added security.
2. Network Segmentation: Building Walls
Segmenting your network creates barriers that limit the impact of sniffing attacks. It’s like having different rooms in a house; if one room is compromised, the rest stay safe. You can follow these Network Segmentation Strategies:
- Firewall Rules: Set up rules to control traffic flow and block unauthorized access.
- Virtual LANs (VLANs): Create virtual networks within your physical network to isolate sensitive data.
3. Strong Authentication Practices: Fortifying Your Defenses
Using strong, unique passwords and implementing multifactor authentication (MFA) adds extra layers of protection against unauthorized access. Some of the best practices for Strong Authentication.
- Password Complexity: Mix it up with uppercase, lowercase, numbers, and symbols for stronger passwords.
- Multifactor Authentication (MFA): Combine passwords with secondary verification methods for enhanced security.
Conclusion: Stay Vigilant, Stay Secure
We’ve covered a lot about password sniffing and how hackers can exploit vulnerabilities to steal your credentials. The key takeaway is to stay vigilant and implement robust security measures to protect yourself and your data. By understanding how these attacks work and taking proactive steps, you can safeguard against potential threats.
Remember, cybersecurity is an ongoing battle, and staying informed is your best defense. Stay safe out there!
FAQs
- What is password sniffing and how does it work?
Password sniffing is a technique used by hackers to intercept and capture passwords as they travel across a network. Hackers use specialized tools to capture data packets containing plaintext passwords, exploiting vulnerabilities in network protocols or devices. - How do hackers sniff passwords on networks?
Hackers sniff passwords on networks by using tools like Wireshark to capture data packets containing login credentials. They exploit weaknesses in network protocols or devices to intercept plaintext passwords as they traverse the network. - Which tools do hackers use for password sniffing?
Hackers use tools like Wireshark, Cain and Abel, ARP spoofing tools, and DNS spoofing tools for password sniffing. These tools allow them to capture, analyze, and exploit network traffic to intercept sensitive information. - How to detect a password sniffing attack?
Detecting a password sniffing attack involves monitoring network traffic for unusual patterns or unauthorized access attempts. Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and network monitoring tools can help detect and alert users to suspicious activities indicative of a sniffing attack. - What are encryption protocols to prevent password sniffing?
Encryption protocols such as HTTPS, SSL/TLS, and VPNs can prevent password sniffing by encrypting data transmitted between clients and servers. This ensures that even if packets are intercepted, the data remains unreadable to unauthorized parties. - How does network segmentation protect against password sniffing?
Network segmentation divides a network into secure zones using firewalls or Virtual LANs (VLANs), limiting the impact of potential sniffing attacks. It restricts unauthorized access to sensitive network segments, reducing the exposure of sensitive information. - What are IDS and IPS in relation to password sniffing?
IDS (Intrusion Detection Systems) and IPS (Intrusion Prevention Systems) are security mechanisms that monitor network traffic for suspicious activities or potential threats, including password sniffing attacks. IDS detects and alerts, while IPS can take proactive measures to block or mitigate detected threats
Wiretap System Breach Exposes Risks of Government-Installed Backdoors in U.S. Telecoms [2024]
Introduction In recent news, the wiretap system breach by China-backed hackers has raised significant alarm…
Password Cracking with Hydra: Step-by-Step Ethical Hacking Guide [Part 11 of Ethical Hacking Series]
Introduction to Password Cracking Password cracking is a method used in cybersecurity to recover passwords…
Step-by-Step Guide to Crack WiFi Passwords with Aircrack-ng [Part 10 of Ethical Hacking Series]
Introduction to Wireless Network Haking Welcome to Part 10 of our Ethical Hacking series, where…
Web Attacks: 7 Tools for OWASP Top 10 Testing [Part 9 of Ethical Hacking Series]
Introduction Welcome to Part 9 of our Ethical Hacking series, where we dive into the…
Post-Exploitation Mastery: Maintaining Access Techniques Explained [Part 8 of Ethical Hacking Series]
Introduction Welcome to Part 8 of our Ethical Hacking series: Post-Exploitation Techniques: Maintaining Access. In…
Stay Safe from Rising Quishing Attack EV at Charging Stations
Electric vehicle (EV) owners need to be cautious as a new cyber threat known as…



![Step-by-Step Guide to Crack WiFi Passwords with Aircrack-ng (Wireless Password Hacking) [Part 10 of Ethical hacking series]](https://hackproofhacks.com/wp-content/uploads/2024/09/Grey-Minimalist-Tips-Blog-Banner-8-1024x576.png)
![Web Attacks: 7 Tools for OWASP Top 10 Testing [part 9 of Ethical Hacking Series]](https://hackproofhacks.com/wp-content/uploads/2024/09/Grey-Minimalist-Tips-Blog-Banner-7-1024x576.png)






Pingback: How to become an ethical hacker in 2024 [FREE RESOURCES INCLUDED] - HackProofHacks