![Web Attacks: 7 Tools for OWASP Top 10 Testing [part 9 of Ethical Hacking Series]](https://hackproofhacks.com/wp-content/uploads/2024/09/Grey-Minimalist-Tips-Blog-Banner-7-1024x576.png)
Introduction
Welcome to Part 9 of our Ethical Hacking series, where we dive into the world of web attacks. Web applications are everywhere today, from the social media platforms we use to the online stores we shop at. However, with the rise of web applications comes an increase in web attacks. Hackers often target these apps to exploit vulnerabilities and gain unauthorized access.
A web attack happens when a hacker finds weaknesses in a web application’s code, configuration, or user interaction points. These attacks can lead to data breaches, financial losses, and even complete system compromise. In this tutorial, we’ll explore the types of web attacks and how they fit into the OWASP Top 10 vulnerabilities—a critical list for anyone involved in web security.
Whether you’re a beginner or experienced in ethical hacking, understanding web attacks is essential for protecting websites and web apps. Attackers commonly exploit weak input validation, insecure sessions, and poor authentication mechanisms. The most dangerous attacks target user data, injecting harmful code or hijacking sessions to control sensitive information.
By studying web attacks, you can better understand how to defend against them. In this article, we will also introduce the OWASP Top 10, which highlights the most critical risks to web applications.
- Introduction
- Common Types of Web Attacks
- What is OWASP?
- OWASP Top 10 Vulnerabilities
- 1. A01:2021-Broken Access Control
- 2. A02:2021-Cryptographic Failures
- 3. A03:2021-Injection
- 4. A04:2021-Insecure Design
- 5. A05:2021-Security Misconfiguration
- 6. A06:2021-Vulnerable and Outdated Components
- 7. A07:2021-Identification and Authentication Failures
- 8. A08:2021-Software and Data Integrity Failures
- 9. A09:2021-Security Logging and Monitoring Failures
- 10. A10:2021-Server-Side Request Forgery (SSRF)
- Relationship Between Web Attacks and OWASP Top 10
- Tools for Testing Web Attacks Based on OWASP Top 10
- Conclusion
Common Types of Web Attacks
In this section, we’ll explore some of the common types of web attacks that hackers use to exploit vulnerabilities in web applications. These attacks target different layers of a web application, from the server to the client-side code. Understanding these web attacks is crucial for ethical hackers and developers alike.
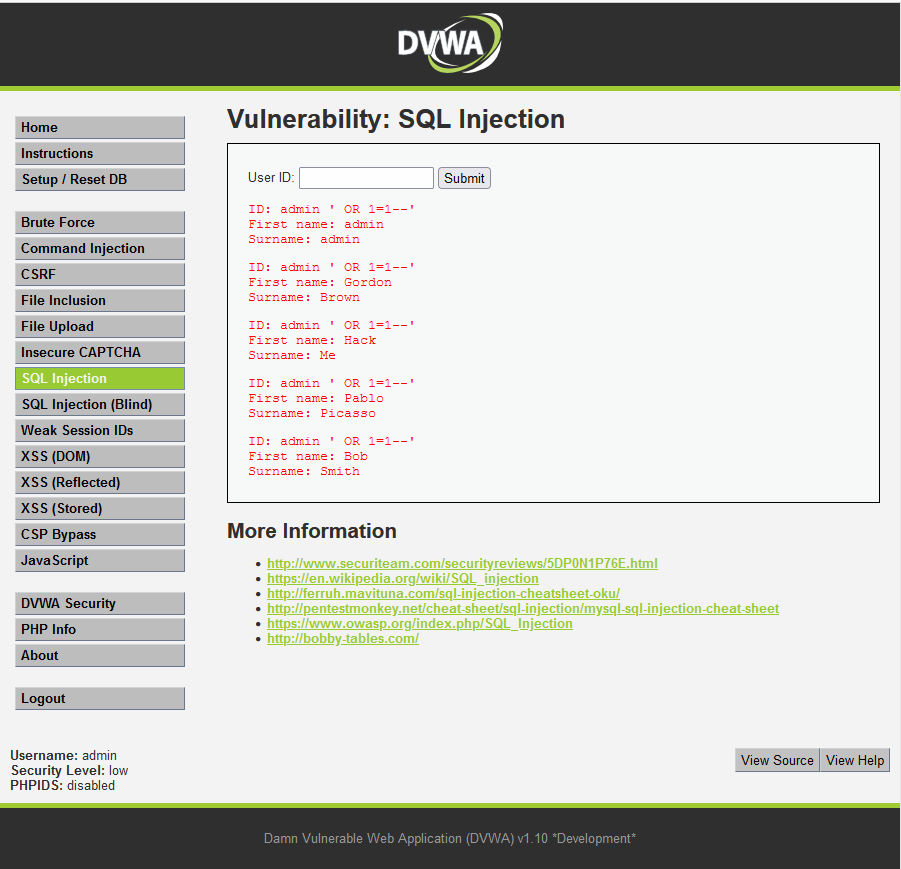
1. SQL Injection (SQLi)
SQL Injection is one of the most well-known web attacks. In this attack, hackers inject malicious SQL code into input fields like login forms or search bars. This allows them to access, modify, or delete data from a website’s database.
For example, by inserting special characters or commands into an input field, an attacker could bypass login authentication or extract sensitive information such as usernames and passwords.
2. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is another common web attack. It happens when attackers inject malicious scripts into web pages that are viewed by other users. The malicious code runs in the user’s browser, allowing the attacker to steal data, hijack sessions, or redirect users to malicious websites.
XSS vulnerabilities usually occur when a web application does not properly sanitize user input. There are three types of XSS: Stored, Reflected, and DOM-based. Each type has a unique method of exploiting user input.
3. Cross-Site Request Forgery (CSRF)
In a Cross-Site Request Forgery (CSRF) attack, hackers trick users into performing unwanted actions on a web application where they are authenticated. For example, an attacker might send a user a malicious link that, when clicked, executes unwanted actions like transferring funds or changing account details.
CSRF exploits the trust that a website has in a user’s browser, making it one of the more subtle yet dangerous web attacks.
4. Broken Authentication and Session Management
Broken authentication occurs when a web application does not properly protect its authentication mechanisms. Hackers can exploit weak password policies, insecure session tokens, or flaws in the login system. This web attack allows attackers to impersonate other users, gaining unauthorized access to accounts and sensitive data.
Weak session management, such as reusing session IDs or failing to log users out after a period of inactivity, also falls under this category.
5. File Inclusion Attacks
File inclusion vulnerabilities occur when a web application allows users to upload or include files without proper security checks. An attacker can exploit this vulnerability to upload malicious files or gain access to sensitive server-side files.
There are two types of file inclusion attacks:
- Local File Inclusion (LFI): The attacker includes a file from the web server.
- Remote File Inclusion (RFI): The attacker includes a file from an external source.
6. Directory Traversal
Directory Traversal is a web attack that allows attackers to access files and directories that are stored outside the web root folder. This vulnerability happens when the web server fails to properly validate user input, allowing attackers to manipulate file paths and gain access to sensitive files.
By understanding these common types of web attacks, ethical hackers can better protect web applications from exploitation. As we progress in this series, we will delve deeper into how to identify and mitigate each of these attacks based on the OWASP Top 10 framework.
What is OWASP?
OWASP, or the Open Web Application Security Project, is a crucial organization in the field of web security. As a non-profit, OWASP focuses on improving the security of software through freely accessible resources and tools. Its mission is to help organizations protect their web applications from various web attacks.
One of OWASP’s most significant contributions is the OWASP Top 10 list. This list identifies the most critical security risks to web applications. It is a key resource for understanding and defending against common web attacks. The OWASP Top 10 is updated every few years to reflect the evolving landscape of web security threats. The latest release, OWASP Top 10 2021, highlights the most pressing vulnerabilities affecting web applications today.
The OWASP Top 10 provides detailed information about each vulnerability and offers guidance on how to mitigate these risks. This list includes categories like injection flaws, broken authentication, and sensitive data exposure. By focusing on these areas, OWASP helps organizations understand where their web applications are most vulnerable and how to address these weaknesses.
In addition to the OWASP Top 10, OWASP offers other valuable resources:
- OWASP Cheat Sheets: These are quick guides that provide practical advice on secure coding practices.
- OWASP ZAP: This open-source tool is designed to find security vulnerabilities in web applications.
- OWASP Dependency-Check: This tool helps identify known vulnerabilities in project dependencies.
Understanding OWASP and its resources is essential for anyone involved in web security. By following OWASP’s guidelines and using its tools, developers and ethical hackers can effectively defend against web attacks and enhance overall application security.
OWASP Top 10 Vulnerabilities
In this tutorial, we will delve into the OWASP Top 10 2021 vulnerabilities. These are the most critical risks to web applications, and understanding them is crucial for protecting against web attacks. We will define each vulnerability, provide examples, and explain how they can be exploited.
1. A01:2021-Broken Access Control
Broken Access Control happens when users gain access to data or functionalities that they are not authorized to access. This often occurs because access restrictions are not properly implemented or enforced. Attackers can exploit this flaw to gain unauthorized access, alter data, or perform administrative actions, potentially compromising the entire system.
Example Scenario: Imagine a web application that allows users to access their profiles at example.com/profile?user_id=123. If the application does not verify that the logged-in user is authorized to view the profile of user_id=123, an attacker might change the user_id parameter to admin and access administrative functions.
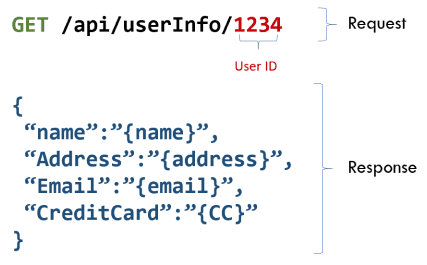
Protection Tips:
- Enforce Role-Based Access Control (RBAC): Define user roles and permissions clearly, and ensure these are checked for every request.
- Conduct Regular Access Reviews: Periodically review access controls to ensure that they are functioning correctly and that no unauthorized access is possible.
2. A02:2021-Cryptographic Failures
Cryptographic Failures occur when sensitive data is not protected properly. This includes weak encryption algorithms, improper key management, or the use of outdated cryptographic methods. Attackers can exploit weak cryptographic protections to gain access to sensitive data, such as passwords or encryption keys.
Example Scenario: A web application stores user passwords using the MD5 algorithm. MD5 is known to be vulnerable to collision attacks, where attackers can generate the same hash from different inputs. If an attacker obtains the hashed passwords, they could easily crack them and gain access to user accounts.
Protection Tips:
- Use Strong Encryption Standards: Implement robust encryption algorithms like AES-256 for data at rest and TLS for data in transit.
- Secure Key Management: Ensure cryptographic keys are stored securely and rotated regularly.
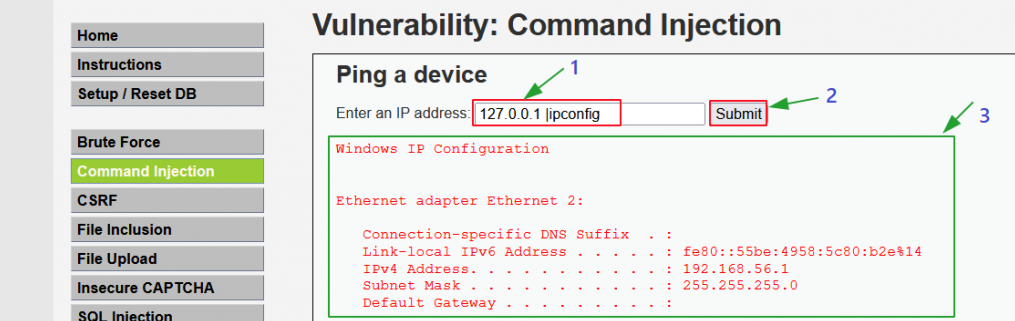
3. A03:2021-Injection
Definition: Injection vulnerabilities occur when an attacker sends malicious data to an interpreter, which then executes it as part of a command or query. This flaw can affect SQL queries, OS commands, or other interpreters. Attackers can use injection vulnerabilities to extract, modify, or delete data, or execute arbitrary commands.
Types of Injection:
- SQL Injection: Exploits vulnerabilities in SQL queries. For example, an attacker might input
'; DROP TABLE users;--into a search field to delete a database table. - Command Injection: Exploits vulnerabilities in system commands. For instance, an attacker might execute arbitrary OS commands through an input field.
- XML Injection: Targets XML data and can manipulate XML queries or commands.
- NoSQL Injection: Targets NoSQL databases, such as MongoDB, by injecting malicious queries.
Example Scenario: In a search feature that constructs SQL queries directly from user input, an attacker could enter a specially crafted input to manipulate the query. For example, entering ' OR '1'='1 might allow an attacker to bypass authentication.
Protection Tips:
- Use Parameterized Queries: Employ parameterized queries or prepared statements to handle user inputs safely.
- Sanitize User Inputs: Validate and clean all user inputs to prevent injection attacks.
- Regular Security Testing: Conduct penetration testing to identify and mitigate injection vulnerabilities.
4. A04:2021-Insecure Design
Insecure Design refers to vulnerabilities arising from poor design decisions, which can introduce risks even if implementation details are secure. Attackers can exploit design flaws to introduce malware or bypass security measures.
Example Scenario: A web application allows file uploads without validating file types. An attacker could upload a malicious file disguised as a harmless image, which could then be executed on the server.
Protection Tips:
- Incorporate Security into Design: Address security considerations during the design phase of development.
- Conduct Threat Modeling: Identify potential threats and design mitigation strategies accordingly.
5. A05:2021-Security Misconfiguration
Definition: Security Misconfiguration happens when security settings are not properly configured, leaving systems exposed to attacks. This can include default settings, unnecessary features, or improper permissions. Attackers can use misconfiguration details to enhance their attacks or find additional vulnerabilities.
Example Scenario: A web server displays detailed error messages that include sensitive information about the server’s internal structure. An attacker could use this information to exploit other vulnerabilities.
Protection Tips:
- Review and Harden Configurations: Regularly audit security configurations and disable unnecessary features.
- Use Security Benchmarks: Follow established security benchmarks for configuration.
6. A06:2021-Vulnerable and Outdated Components
Definition: Vulnerable and Outdated Components are software components, such as libraries or plugins, that have known security vulnerabilities or are outdated. Attackers can exploit vulnerabilities in outdated components to gain unauthorized access or execute malicious code.
Example Scenario: A web application uses an outdated version of a JavaScript library with known security flaws. An attacker could exploit these flaws to execute malicious scripts or access sensitive data.
Protection Tips:
- Keep Software Updated: Regularly update libraries, frameworks, and plugins to the latest versions.
- Use Vulnerability Scanners: Employ tools to detect known vulnerabilities in third-party components.
7. A07:2021-Identification and Authentication Failures
Identification and Authentication Failures occur when authentication mechanisms are weak, allowing unauthorized access or account compromise. Attackers can exploit weak authentication to hijack accounts or access restricted areas.
Example Scenario: A web application allows users to log in with simple passwords and does not implement multi-factor authentication (MFA). An attacker could use brute force attacks to guess passwords and gain access to user accounts.
Protection Tips:
- Implement Strong Authentication Measures: Enforce strong password policies and use multi-factor authentication.
- Monitor Authentication Activities: Track and respond to suspicious login attempts.
8. A08:2021-Software and Data Integrity Failures
Software and Data Integrity Failures occur when software or data can be tampered with, leading to compromised integrity. Attackers can exploit these failures to corrupt data or introduce malware.
Example Scenario: A web application allows users to upload files without validating their integrity. An attacker could upload a malicious file, which the application could then execute or use inappropriately.
Protection Tips:
- Verify Data Integrity: Use checksums or digital signatures to ensure that data and software have not been tampered with.
- Secure Update Mechanisms: Ensure that software updates are properly verified before installation.
9. A09:2021-Security Logging and Monitoring Failures
Security Logging and Monitoring Failures occur when there is insufficient logging or monitoring of security events, making it difficult to detect and respond to attacks. Attackers can exploit inadequate logging to perform actions that go unnoticed, increasing their chances of successful exploitation.
Example Scenario: A web application does not log failed login attempts or other suspicious activities. An attacker could exploit this lack of monitoring to perform unauthorized actions without being detected.
Protection Tips:
- Implement Comprehensive Logging: Ensure all relevant security events are logged and monitored.
- Analyze Logs Regularly: Regularly review logs for signs of suspicious activity and configure alerts for critical events.
10. A10:2021-Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) involves tricking a server into making unauthorized requests. This can lead to accessing internal resources or data. Attackers can use SSRF to bypass network protections, access internal services, or extract sensitive data.
Example Scenario: A web application allows users to specify URLs for fetching data. An attacker could manipulate the URL to make the server request internal services or metadata, potentially exposing sensitive information.
Protection Tips:
- Validate User Inputs: Ensure that user-provided URLs are properly validated and restricted.
- Restrict Internal Requests: Implement controls to limit the server’s ability to make internal requests.
By understanding these vulnerabilities, you can better protect your web applications from common web attacks. The OWASP Top 10 2021 provides a comprehensive guide to the most critical security risks, and addressing these issues can significantly enhance your application’s security posture.
Relationship Between Web Attacks and OWASP Top 10
The relationship between web attacks and the OWASP Top 10 vulnerabilities is crucial for understanding how common security threats exploit weaknesses in web applications. Each vulnerability listed in the OWASP Top 10 represents a common target for various types of web attacks.
For example, Broken Access Control issues often lead to attacks where unauthorized users gain access to restricted areas by manipulating URL parameters or session tokens. Cryptographic Failures involve attacks that exploit weak or outdated encryption to access sensitive data. Similarly, Injection attacks, such as SQL Injection, exploit flaws in how user inputs are handled, allowing attackers to manipulate queries and commands.
Insecure Design flaws in applications can be exploited through poorly designed features, while Security Misconfiguration opens doors to attacks due to default settings or inadequate security controls. Vulnerable and Outdated Components are targeted by attackers exploiting known flaws in outdated libraries. Identification and Authentication Failures are exploited through weak login mechanisms or credential stuffing. Software and Data Integrity Failures are used to tamper with data or code, and Security Logging and Monitoring Failures allow attackers to perform malicious activities undetected.
Server-Side Request Forgery (SSRF) exploits involve tricking the server into making unauthorized requests, potentially exposing internal services. Understanding how these vulnerabilities align with web attacks helps in designing more secure applications by addressing these common weaknesses effectively.
Tools for Testing Web Attacks Based on OWASP Top 10
When testing for web attacks and addressing vulnerabilities listed in the OWASP Top 10, several tools can help you identify and fix security issues. Here’s a guide to some essential tools:
Burp Suite
Burp Suite is widely used for web security testing. It helps find issues like Injection attacks (A03:2021) and Security Misconfiguration (A05:2021). With Burp Suite, you can scan your web application for common vulnerabilities, intercept and modify web requests, and analyze responses. It’s particularly effective at detecting SQL Injection and Cross-Site Scripting (XSS).
OWASP ZAP (Zed Attack Proxy)
OWASP ZAP is an open-source tool designed to find web attacks. It is useful for detecting vulnerabilities such as Broken Access Control (A01:2021) and Cryptographic Failures (A02:2021). ZAP includes features for both active and passive scanning, and it can crawl your web application to discover new areas to test.
SQLmap
SQLmap focuses on finding SQL Injection vulnerabilities (A03:2021). This tool automates the detection and exploitation of SQL Injection flaws, helping you extract data from databases if vulnerabilities are found. It simplifies the process of testing your web application for these critical issues.
Nikto
Nikto is a web server scanner that helps identify Security Misconfiguration issues (A05:2021). It scans for outdated software, configuration errors, and other common vulnerabilities. Nikto is straightforward and helps ensure your web server does not have easily exploitable issues.
Nmap with NSE (Nmap Scripting Engine)
Nmap is a network scanning tool that, with the Nmap Scripting Engine (NSE), can be used to detect Vulnerable and Outdated Components (A06:2021). NSE scripts automate the detection of specific vulnerabilities and provide detailed information on potential security risks.
OWASP Dependency-Check
OWASP Dependency-Check is used to identify Vulnerable and Outdated Components (A06:2021) in your project. It scans the libraries and dependencies you use, checking them against a database of known vulnerabilities to help you manage outdated or insecure components.
Hydra
Hydra tests Identification and Authentication Failures (A07:2021). It performs brute-force attacks on various protocols to test the strength of your authentication systems. Hydra helps identify weaknesses in login mechanisms that could be exploited by attackers.
Nuclei
Nuclei is a fast and flexible tool for detecting a range of web attacks and vulnerabilities. It uses a templated approach to scan for issues like Security Misconfiguration (A05:2021) and Vulnerable and Outdated Components (A06:2021). Nuclei is highly customizable and can be used to create and run scans based on specific patterns and templates, making it a powerful tool for continuous security assessments.
By integrating these tools into your security testing process, you can effectively identify and address vulnerabilities listed in the OWASP Top 10. Each tool offers unique features that help in detecting and mitigating different types of web attacks, enhancing the overall security of your web applications.
Conclusion
Web security is a critical aspect of protecting applications from web attacks. In this part of the Ethical Hacking Series, we have explored the relationship between web attacks and the OWASP Top 10, which serves as a valuable guide for identifying the most common and dangerous vulnerabilities.
Understanding the OWASP Top 10 is essential for any ethical hacker or developer who wants to secure their web applications. By learning about vulnerabilities such as Broken Access Control, Injection, and Security Misconfiguration, you can take proactive steps to prevent these web attacks. Tools like Burp Suite, OWASP ZAP, SQLmap, and Nuclei offer practical ways to detect and mitigate these vulnerabilities.
The continuous release of the OWASP Top 10, with the latest in 2021, reminds us of the evolving landscape of web security. To stay ahead of emerging threats, it’s crucial to keep testing, learning, and applying the right tools to safeguard your applications.
This guide highlights the importance of understanding and addressing web attacks based on the OWASP Top 10. Whether you are a beginner or an advanced ethical hacker, following these principles will help you build more secure systems and protect sensitive data from cyber threats.

![Ethical Hacking series [Part 1]: Installing Kali Linux and Setting Up DVWA on VirtualBox](https://hackproofhacks.com/wp-content/uploads/2024/05/Grey-Minimalist-Tips-Blog-Banner-1024x576.png.webp)