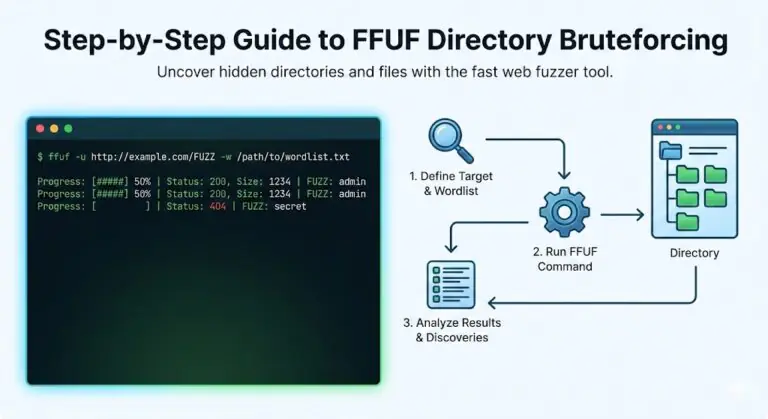
Introduction What is FFUF? FFUF stands for Fuzz Faster U...
Read MoreHow to Start Ethical Hacking in 10 Simple Steps: From Basics to Advanced Techniques

Introduction
If you’re wondering how to start ethical hacking, you’re in the right place. Ethical hacking is a valuable skill that helps protect systems from malicious hackers. It involves testing and securing networks, systems, and web applications.
To get started, you need a solid foundation in networking, programming, and security concepts. Ethical hacking is not just about using tools; it’s about understanding how systems work and how vulnerabilities can be exploited.
Start by learning basic networking, such as IP addresses, protocols, and ports. Then, move on to understanding common vulnerabilities. Familiarize yourself with tools like Kali Linux, Nmap, and Wireshark.
One important part of how to start ethical hacking is setting up your own lab environment. You can practice hacking techniques on virtual machines without causing any harm. As you grow, you’ll need to stay up-to-date with new hacking techniques and security trends.
Joining a community or accessing exclusive resources through a membership can provide continuous learning and support. Remember, the key to becoming proficient is consistent practice and staying curious.
So, if you’re serious about how to start ethical hacking, take the first step today by learning the basics and setting up your hacking lab.
- Introduction
- Step 1: Mastering the Basics of Ethical Hacking
- Step 2: Mastering Networking and Basic Programming
- Step 3: Familiarizing Yourself with Linux and Command-Line Tools
- Step 4: Learning Reconnaissance and Information Gathering Techniques
- Step 5: Mastering Vulnerability Scanning and Exploitation
- Step 6: Developing Social Engineering Skills
- Step 7: Learning Post-Exploitation Techniques
- Step 8: Moving to Advanced Web Application Attacks
- Step 9: Mastering Wireless Network Hacking
- Step 10: Continuous Practice and Real-World Simulation
- Conclusion
Step 1: Mastering the Basics of Ethical Hacking
So, you want to dive into ethical hacking? The first step is building a rock-solid understanding of the fundamentals. Think of it like constructing a house: without a strong foundation, everything else falls apart. With over a decade of experience in the field, I can tell you… this first step is everything.
Start with Networking
A hacker’s playground is the world of networks, so knowing networking is essential. Start with concepts like IP addresses, TCP/IP, ports, and basic protocols (like HTTP, HTTPS, and FTP). Each of these is a tool you’ll wield as an ethical hacker. Every piece of data that moves across a network is part of a story, and understanding that story is key to uncovering vulnerabilities.
Study Security Essentials
Next, let’s talk about security fundamentals. Here’s the reality: attackers are constantly exploiting weak points. Your job? Understand those weaknesses better than anyone else. Familiarize yourself with core security principles like:
- Encryption (keeping data safe and unreadable)
- Authentication (confirming identity)
- Authorization (setting permissions)
Every security layer has a purpose, and understanding why they’re there will shape you into a more insightful hacker.
Get to Know Common Vulnerabilities
Now, onto the types of vulnerabilities that hackers exploit… things like SQL injections and Cross-Site Scripting (XSS). These are the cracks in the system, the flaws that attackers will look for. Learn why they happen and how they’re used.
Hands-On Practice in a Lab Environment
Knowledge without practice is wasted potential. Create your own hacking lab environment using virtual machines (like Kali Linux). Set up systems to test what you’ve learned, safely and ethically. Start small—scan networks, probe for open ports, or test basic vulnerabilities. With each success, you’re one step closer to advancing your skills.
Remember, ethical hacking is about protection, not harm. Build your skills with curiosity and respect for boundaries. Understand the basics, and you’ll be well-equipped to tackle the advanced skills that lie ahead.
Starting ethical hacking isn’t just about learning what to do; it’s about why you’re doing it. Master the basics, and you’ll set yourself up for a powerful, rewarding journey into the field of ethical hacking.
Step 2: Mastering Networking and Basic Programming
If you’re serious about learning how to start ethical hacking, it’s time to master two fundamental skills: networking and programming. These skills are non-negotiable for anyone looking to transition from a beginner to a capable hacker. Let’s break down why they matter and how you can build these skills effectively.
Networking: The Backbone of Ethical Hacking
Networking knowledge is crucial because every attack you’ll encounter or perform involves some type of network. Here’s how to get started:
- Understand IP Addresses and Subnetting – IP addresses are the addresses of devices on a network. Learn how they’re structured and what subnetting is, as it helps you understand network organization.
- Get Familiar with Protocols – Start with the basics like TCP/IP, HTTP, HTTPS, and FTP. Each protocol serves a purpose and is tied to vulnerabilities you’ll need to know. The TCP/IP model, in particular, is the language of the internet, so understanding it will unlock insights into how data travels and where attacks might occur.
- Explore Tools like Wireshark – Practice using Wireshark to observe network traffic. This tool will show you what happens when data is sent and received, helping you see what’s normal and what could be suspicious.
By understanding networking, you’ll be able to navigate and analyze any system, which is essential for effective hacking.
Basic Programming: Building Blocks of Hacking
Programming skills will allow you to write scripts, exploit vulnerabilities, and automate tasks. Start with a couple of simple but powerful languages:
- Python – Known for its simplicity and wide use in hacking, Python is perfect for writing small scripts to automate tasks or scan networks. With Python, you can write a script in just a few lines that would take hours to do manually.
- Bash Scripting – If you’re using Linux, bash scripting is a must. Bash lets you perform tasks from the command line, making it great for managing files, running system commands, and automating repetitive tasks.
- HTML and JavaScript – These web languages are useful for understanding web-based vulnerabilities like Cross-Site Scripting (XSS) and SQL Injection. Even a basic knowledge of these languages will help you spot potential security issues on websites.
Practice, Experiment, Repeat
Like networking, programming requires hands-on practice. Try writing simple scripts to solve problems you encounter. For example, a script that scans for open ports or a bash script to automate simple tasks on your machine. This is how you move from theory to real-world application.
Bringing It All Together
Networking and programming aren’t just separate skills; they work together. When you understand how networks function, you can write more efficient scripts. And when you know programming, you can customize your network scans to target specific vulnerabilities.
Mastering these two areas will put you leagues ahead on your ethical hacking journey. Every tool you’ll use, every system you’ll explore, will be grounded in these skills.
Enter the World of Hackers
The real world of hackers is calling—a place where the lines between reality and the digital blur. Join our alliance, and together, we’ll navigate the shadows.
Join NowADVERTISE WITH US!
We offers several ways to get your products and services in front of our engaged audience.
Enquire NowStep 3: Familiarizing Yourself with Linux and Command-Line Tools
Mastering Linux and command-line tools is essential in how to start ethical hacking. Most hacking tools are built for Linux, and command-line skills let you control, analyze, and exploit systems efficiently. Let’s dive into why Linux is important and how to build confidence in using it.
Why Linux is a Must for Hackers
Linux is the operating system of choice for hackers because it’s customizable, open-source, and powerful. It gives you full control over system processes and has a wide range of security and hacking tools. Familiarizing yourself with Linux will give you an advantage, especially when dealing with network configurations, file permissions, and data encryption.
Getting Started with Linux Basics
If you’re new to Linux, begin with a hacking-focused distribution like Kali Linux. Kali comes with pre-installed tools for penetration testing and security assessments, so it’s ideal for beginners.

- File Navigation – Start by learning basic commands like cd to change directories, ls to list files, and mkdir to create directories. These commands let you move around and manage files on the system.
- Permissions and Processes – Use commands like chmod to change file permissions and ps to view running processes. Knowing these commands helps you understand file security and how to manage programs running on a system.
- File Editing with Nano or Vim – Learn to use text editors like Nano or Vim for editing files directly in the command line. Editing configuration files and creating scripts are key parts of ethical hacking, so practice these frequently.
Key Command-Line Tools for Hackers
Some essential Linux command-line tools for how to start ethical hacking include:
- Nmap – A powerful tool for network scanning. With Nmap, you can identify open ports and running services on a target network.
- Netcat – Often called the “Swiss Army knife” of networking, Netcat is useful for establishing connections, monitoring network traffic, and even creating backdoors.
- Tcpdump – A command-line packet analyzer that lets you capture and analyze network traffic. It’s essential for detecting suspicious activity.
Building Linux Confidence
Spend time on practical exercises in Linux. For example, try configuring a network, creating a simple Bash script, or scanning a local IP address range with Nmap. The more you practice, the faster you’ll pick up essential skills. Every small project builds your confidence and makes you more comfortable with Linux.
Mastery Through Practice
Linux isn’t just about learning commands; it’s about developing a mindset where you think in terms of scripts and automation. Set up a virtual machine with Kali Linux, and practice every command and tool you learn. This hands-on approach is critical to how to start ethical hacking successfully.
In short, Linux is your playground for hacking, and command-line skills are the tools you’ll use to navigate it. As you continue, these skills will form the foundation of your hacking expertise.
In short, Linux is your playground for hacking, and command-line skills are the tools you’ll use to navigate it. As you continue, these skills will form the foundation of your hacking expertise.
Step 4: Learning Reconnaissance and Information Gathering Techniques
Mastering reconnaissance is crucial in how to start ethical hacking. Reconnaissance, also known as “recon,” is all about collecting information about your target before diving into deeper analysis. Think of it as building a complete map that reveals the target’s structure, potential weaknesses, and the tools they use. This step helps you make strategic decisions for testing security effectively.
Why Reconnaissance Matters
Reconnaissance is the first phase of any hacking process. Before any attack, ethical hackers gather data to understand the target’s defenses. This process gives you insight into the organization’s network, software, and user behavior, laying the groundwork for effective testing.
Types of Reconnaissance Techniques
Reconnaissance techniques fall into two main categories:
- Passive Reconnaissance – Involves gathering data without directly interacting with the target. This reduces the chances of being detected. Activities include browsing public information on websites, social media, and databases.
- Active Reconnaissance – Involves directly interacting with the target system, such as running network scans to identify open ports and services. This method provides more detailed data but carries a higher risk of detection.
Essential Tools for Reconnaissance
Here are some top tools you’ll use in reconnaissance:
- Whois – A basic tool for finding details about a domain, like registration, ownership, and hosting. It’s a great start to learn who’s behind the target’s domain.
- Nmap – A powerful network scanning tool to detect open ports, services, and operating systems on the target network. Nmap provides a detailed view of potential entry points.
- Maltego – A graphical tool that maps connections between people, companies, websites, and social media profiles. It’s particularly useful for passive recon and visualizing relationships.
Step-by-Step Guide to Gathering Information
- Domain and IP Analysis – Start by using Whois and Nslookup to find basic details about the target’s domain and IP address range.
- Network Scanning with Nmap – Run an Nmap scan to identify open ports and the services running on them. Try different scan types like SYN or UDP scans for varied results.
- Subdomain Enumeration – Tools like Sublist3r help you find subdomains, which can lead to hidden sections of the website. This is essential for uncovering less secure areas.
- Social Media and Public Data – Browse social media platforms to find information on employees, technology stacks, and potential insider data leaks. This passive recon can reveal surprisingly useful data.
- Email Harvesting – Tools like theHarvester collect email addresses from public sources. Emails are often used in phishing attacks, making them valuable for testing social engineering.
Practicing Reconnaissance
Apply these methods to a legal test environment or permission-based targets. This practice lets you get comfortable with the tools and strategies needed to build a complete target profile.
Reconnaissance helps you understand the target’s vulnerabilities from a distance, and knowing these techniques is foundational in how to start ethical hacking.
Step 5: Mastering Vulnerability Scanning and Exploitation
Vulnerability scanning and exploitation are at the heart of how to start ethical hacking. This step takes you beyond just identifying a system’s defenses. Now, you’re looking for the weaknesses in those defenses, and knowing how to pinpoint and exploit them is key to advancing your skills.
Understanding Vulnerability Scanning
Vulnerability scanning is the process of probing a system or network to identify known vulnerabilities. It helps ethical hackers map out the flaws in the system, showing which parts are weak and can potentially be exploited. This is a critical skill to develop, as scanning is the foundation of the exploitation phase.
Essential Vulnerability Scanning Tools
- Nessus – Nessus is one of the most popular vulnerability scanners used to detect a wide range of vulnerabilities. It provides details on each issue and offers recommendations for fixing them.
- OpenVAS – An open-source alternative, OpenVAS also scans for a variety of vulnerabilities. It’s flexible and great for learning in different environments.
- Nikto – This web server scanner checks for outdated software, dangerous files, and misconfigurations on websites. Nikto is simple to use and extremely useful for finding web vulnerabilities.
Steps to Conduct a Vulnerability Scan

- Identify the Target – First, choose the device, server, or network segment you want to scan. Make sure you have legal permission to test the system.
- Run the Vulnerability Scan – Use Nessus or OpenVAS to perform a detailed scan. Look out for high-risk vulnerabilities, as these are often the primary targets for exploitation.
- Analyze the Scan Report – Vulnerability reports provide information on the weaknesses detected, such as outdated software versions, open ports, or insecure configurations.
Basics of Exploitation
Once vulnerabilities are identified, exploitation involves taking advantage of these weaknesses to test the system’s security response. For ethical hackers, this is a critical skill to learn, but it should be handled responsibly and legally.
Key Exploitation Tools
- Metasploit – Metasploit is the most popular exploitation framework. It provides a library of exploit modules and tools, making it easy to test vulnerabilities in a structured way.
- SQLmap – Used to automate SQL injection attacks, SQLmap helps you find and exploit SQL injection vulnerabilities in web applications.
- John the Ripper – A password-cracking tool that helps in brute-forcing passwords during exploitation. It’s particularly useful if you’ve identified weak password policies in your scan.
Step-by-Step Exploitation Process
- Research the Vulnerability – Once a vulnerability is identified, gather information about it. This might include finding relevant CVEs (Common Vulnerabilities and Exposures) or researching specific attack techniques.
- Choose an Exploit – Using tools like Metasploit, select an exploit that targets the specific vulnerability. Some vulnerabilities might require custom exploitation scripts or modifications.
- Test the Exploit – Run the exploit in a controlled environment. The goal here is to see how the system responds and determine if further action can be taken.
- Maintain Logs and Document Findings – Document the entire process, including details about the vulnerability, how it was exploited, and the security response. This is essential for reporting to the client or organization being tested.
Practicing Exploitation Techniques
Experiment with vulnerability scanning and exploitation on legal practice environments, such as Hack The Box or DVWA (Damn Vulnerable Web Application). Practice helps you build confidence and become skilled at identifying and safely testing vulnerabilities.
Mastering vulnerability scanning and exploitation is a huge step in how to start ethical hacking. It’s not only about finding weaknesses; it’s about understanding how to exploit and fix them responsibly.
Step 7: Learning Post-Exploitation Techniques
Mastering post-exploitation is a crucial step in how to start ethical hacking effectively. Post-exploitation involves what you do after you’ve gained access to a system. In ethical hacking, this stage allows you to assess the potential damage an attacker could cause if they had access. It also helps identify weak points within a network or system.
What is Post-Exploitation?
Post-exploitation is the process of maintaining access to a compromised system, collecting data, and determining what an attacker could do next. It’s all about understanding how to keep control and extract useful information without raising alarms.
Key Techniques in Post-Exploitation
- Privilege Escalation – After gaining initial access, the goal is often to increase privileges within the system, moving from a low-level user to an administrator. Privilege escalation enables deeper access to sensitive areas.
- Persistence – To stay undetected, attackers create ways to regain access if their session is terminated. This might involve installing backdoors or configuring auto-start services that remain active after a reboot.
- Data Exfiltration – This is the process of gathering and transferring data from the target system. In ethical hacking, data exfiltration helps in understanding what kind of sensitive data might be at risk.
- Network Reconnaissance – Once inside, map out the internal network. Learn the network layout, find other connected systems, and check for vulnerabilities within those systems.
- Covering Tracks – Skilled hackers know how to avoid detection. Clearing logs, disabling alerts, and using encrypted channels are common ways to stay hidden.
Practical Steps to Learn Post-Exploitation Techniques
- Get Comfortable with Privilege Escalation Tools – Tools like Metasploit and PowerShell Empire are often used to escalate privileges within a system. Practice using these tools on virtual labs like DVWA or Hack The Box to get a feel for escalation.
- Understand How to Set Up Persistence – Experiment with different methods to keep control of a system. Try adding new user accounts, installing rootkits, or using scheduled tasks to maintain access.
- Practice Data Exfiltration Methods – Familiarize yourself with data extraction techniques. Use tools like Netcat to transfer files or learn about HTTP tunneling to send data over hidden channels.
- Explore Internal Network Reconnaissance – Run scanning tools within a compromised network to see what systems are connected. Use Nmap and Netdiscover for mapping out local networks.
- Learn Log Cleaning Techniques – In post-exploitation, you want to remain hidden. Practice clearing logs and hiding activity trails to understand how attackers minimize detection.
Ethical Responsibility in Post-Exploitation
Post-exploitation must always be performed under ethical guidelines. Every action should be documented, controlled, and approved by the client. Misusing post-exploitation techniques can lead to significant harm and legal consequences.
Learning post-exploitation gives you insight into the deeper layers of how to start ethical hacking. It’s about securing access, assessing data risks, and understanding a system from the inside out, all while remaining stealthy. This knowledge completes your skill set, preparing you for a full-scope ethical hacking approach.
Step 8: Moving to Advanced Web Application Attacks
After mastering the basics, it’s time to move into advanced web application attacks. Understanding these attacks will strengthen your knowledge of how to start ethical hacking for web-based systems. Web applications are frequently targeted by attackers because they handle valuable data, user accounts, and sensitive information.
Why Focus on Web Application Attacks?
Web applications often hold sensitive data and are accessible over the internet, making them easy targets. Learning advanced attack methods helps you understand how attackers bypass security measures and exploit weaknesses in web code, logic, and session management.
Key Advanced Web Application Attacks
- SQL Injection (SQLi) – An attacker can manipulate a web app’s database by injecting malicious SQL queries. While basic SQL injection targets simple data extraction, advanced techniques aim to alter, delete, or gain administrative control over databases.
- Cross-Site Scripting (XSS) – XSS enables attackers to inject malicious scripts into a website’s code, which can execute in a user’s browser. Advanced XSS attacks often target session hijacking, cookie theft, and data manipulation to gain access to user accounts.
- Cross-Site Request Forgery (CSRF) – CSRF tricks users into performing actions they didn’t intend. Advanced CSRF attacks can force users to transfer funds or change account details without their consent.
- Server-Side Request Forgery (SSRF) – With SSRF, attackers trick a server into accessing unintended resources. SSRF attacks are often used to access sensitive data or interact with internal network services, bypassing firewalls.
- Remote File Inclusion (RFI) – RFI allows attackers to remotely execute malicious files on a web server. Advanced RFI attacks enable control over a server, possibly leading to backdoor installations.
Practical Steps for Advanced Web Application Attacks
- Learn Advanced SQLi Techniques – Practice SQL injection beyond basic data extraction. Learn about blind SQLi, time-based injections, and how to bypass web application firewalls (WAFs) that block basic SQLi attempts.
- Master XSS Payloads – Study payloads for various browsers, inject JavaScript code, and manipulate cookies to simulate account hijacking scenarios. Use testing tools like XSS Hunter to explore vulnerabilities on different platforms.
- Perform CSRF Attacks with Custom Scripts – Create scripts to automate CSRF attacks. Practice sending crafted requests that change data, such as transferring funds between accounts, to understand the severity of CSRF.
- Explore SSRF on Internal Resources – Use tools like Burp Suite to perform SSRF. Try accessing hidden internal resources through the server, and understand how SSRF can be combined with other vulnerabilities to cause severe impact.
- Practice RFI in a Controlled Environment – Use virtual machines or isolated servers to safely practice remote file inclusion. Experiment with how RFI allows attackers to load malicious scripts from external sources and control a web server.
Tools for Practicing Web Application Attacks
Some of the best tools for learning advanced web application attacks include:
- Burp Suite – A comprehensive tool for web vulnerability testing and exploitation.
- OWASP ZAP – Another popular tool for testing and finding web app vulnerabilities.
- SQLmap – Automates SQL injection, useful for learning advanced SQLi.
Ethical Responsibility
Always remember that using these techniques should be under ethical guidelines, in a controlled environment, or with client permission. Understanding these attacks will help you spot weaknesses and propose security improvements, which is a crucial skill in how to start ethical hacking for web security.
In advanced web application hacking, you dive deep into the methods attackers use to control or exploit web-based systems. By learning these techniques, you build skills to protect applications from a range of real-world threats
Step 9: Mastering Wireless Network Hacking
To truly understand how to start ethical hacking, you need to dive into wireless network hacking. Wireless networks are common, and with this knowledge, you’ll be able to uncover potential vulnerabilities in WiFi security. Knowing how to analyze and test wireless networks will make you more effective in identifying real-world security gaps.
Why Wireless Network Hacking Matters?
Wireless networks are often more vulnerable than wired networks due to their open nature. Many users lack strong security protocols, making them easy targets. As an ethical hacker, knowing how attackers compromise these networks gives you the skills to secure them.
Key Concepts in Wireless Hacking
- WiFi Security Protocols – Familiarize yourself with WEP, WPA, WPA2, and WPA3. While WEP is outdated and easily cracked, WPA2 is more secure but still vulnerable to specific attacks. Understanding these protocols helps you identify weaknesses in different types of WiFi.
- Packet Capture – Tools like airodump-ng allow you to capture data packets transmitted over a WiFi network. Capturing packets is essential for identifying vulnerabilities and preparing for handshake capture, a key step in cracking WiFi passwords.
- Handshakes and Authentication – Wireless hacking often involves capturing the 4-way handshake, which contains encrypted data that can reveal a network’s password. You’ll need specific hardware, like a WiFi adapter that supports monitor mode, to capture these handshakes.
Step-by-Step: Mastering Wireless Hacking
- Set Up Hardware and Software
To start, make sure you have a compatible WiFi adapter capable of monitor mode. Use Kali Linux as your base operating system since it has built-in tools like aircrack-ng for WiFi analysis and hacking. - Capture WiFi Handshakes
Use airodump-ng to monitor nearby networks and capture the handshake packets from WPA/WPA2 networks. Once captured, these handshakes are used to crack the network password. - Dictionary Attack on WiFi Passwords
After capturing a handshake, run aircrack-ng with a dictionary file (a file with possible passwords) to crack the WiFi password. A strong wordlist is essential for a successful attack, so try using large lists to increase your chances.
Tools for Wireless Hacking
Here are some essential tools to get started:
- Aircrack-ng – For capturing and analyzing WiFi handshakes.
- Wireshark – For deeper packet analysis and network traffic monitoring.
- Reaver – For brute-forcing WPS (if the network has WPS enabled).
Ethical Considerations
Wireless network hacking is highly sensitive and should only be done on networks you have permission to test. Unauthorized access to networks is illegal and unethical. Remember, ethical hacking is about understanding vulnerabilities to create safer networks, not exploiting them.
Mastering wireless network hacking is an essential part of how to start ethical hacking. With these skills, you’ll have a complete understanding of WiFi security weaknesses and can help protect networks against real threats.
Step 10: Continuous Practice and Real-World Simulation
To fully grasp how to start ethical hacking, continuous practice and real-world simulations are essential. Ethical hacking isn’t a skill you learn once—it’s a field that evolves daily. To stay sharp, you need to constantly test your knowledge, adapt to new security challenges, and refine your techniques.
Why Practice Matters in Ethical Hacking?
Ethical hacking requires a hands-on approach. Reading or watching tutorials won’t build practical expertise. Practicing lets you apply your skills in safe, controlled environments. Simulations mimic real attack scenarios and give you a taste of what it’s like to face real-world cyber threats.
How to Practice Ethical Hacking Skills
- Set Up Virtual Labs
Create a virtual environment using tools like VirtualBox or VMware to set up different operating systems. Use intentionally vulnerable platforms like DVWA (Damn Vulnerable Web Application) or Metasploitable for testing. These labs let you explore hacking techniques safely and legally. - Join Online Practice Platforms
Websites like Hack The Box and TryHackMe provide interactive challenges that mimic real-world hacking scenarios. These platforms have tasks for all skill levels and are an excellent way to practice both basic and advanced techniques. - Participate in Capture the Flag (CTF) Competitions
CTF competitions are simulated hacking challenges where you “capture flags” by exploiting vulnerabilities. These competitions test your knowledge in various hacking areas, like web security, cryptography, and reverse engineering. It’s one of the best ways to experience live hacking challenges
Real-World Simulation
Real-world simulation means recreating real attack scenarios in controlled environments. This includes practicing social engineering, phishing simulation, or testing malware in a sandbox environment. Realistic simulations help you understand how hackers exploit real vulnerabilities and prepare you to defend against actual attacks.
- Phishing Simulation – Set up phishing simulations to understand how attackers steal credentials. Learn how phishing emails are crafted and how to identify red flags.
- Penetration Testing on Virtual Machines – Set up network configurations in your virtual lab to practice penetrating different systems. Use tools like Nmap and Metasploit to practice scanning and exploiting known vulnerabilities.
- Log and Monitor Your Activity – Track your actions with logging tools to see exactly how attacks unfold. Monitoring logs after simulations helps you see security breaches from an attacker’s perspective.
Continuous Learning Resources
- Stay Updated: Follow cybersecurity blogs, forums, and news. Being informed about the latest vulnerabilities and patches helps you stay ahead.
- Certifications: Consider certifications like CEH (Certified Ethical Hacker) and OSCP (Offensive Security Certified Professional) to solidify your knowledge and improve your job prospects.
To truly understand how to start ethical hacking, regular practice and simulation are key. Each practice session adds to your expertise, enabling you to tackle new challenges confidently.
Conclusion and Next Steps
Learning how to start ethical hacking is an exciting journey that opens doors to endless possibilities. By now, you should have a solid foundation in the essential steps—from understanding networking basics and practicing reconnaissance to exploring advanced web and wireless hacking techniques. Ethical hacking is not just about skills; it’s a mindset of constant learning, attention to detail, and curiosity to dig deeper.
What Comes Next?
As you continue, focus on refining and advancing your skills. Dive deeper into specific areas, whether it’s web application security, social engineering, or network penetration testing. Practice regularly, participate in Capture the Flag (CTF) events, and stay updated on the latest threats and vulnerabilities. Remember, ethical hacking requires a commitment to ongoing learning.
For those ready to take their skills to the next level, certifications like CEH (Certified Ethical Hacker) or OSCP (Offensive Security Certified Professional) can boost credibility and open doors to professional opportunities. Alongside this, our Hackers Real World membership offers exclusive resources, labs, and insights to help you continuously sharpen your skills.
A Community for Support
The cybersecurity community is incredibly supportive. Connect with other hackers, join forums, and engage in discussions. Real-world simulations and feedback from experienced professionals are invaluable as you develop your expertise. Embrace learning from others and sharing your own insights.
Final Words
Starting with the basics and steadily advancing through complex skills is the key to mastering how to start ethical hacking. Keep practicing, keep learning, and stay vigilant. Your dedication and persistence will pave the way for a fulfilling and impactful career in ethical hacking.
YOU MAY ALSO LIKE
7 Powerful Shell Scripting Tricks to Automate Recon Like a Pro
Learn how to use shell scripting to automate reconnaissance in...
Read MoreHow Hackers Use WaybackURLs to Find Hidden Website Vulnerabilities
Hackers look at old URLs because they can reveal forgotten...
Read MoreCritical Security Vulnerability in Cisco Meeting Management
Critical Security Vulnerability in Cisco Meeting Management (CVE-2025-20156) allows privilege...
Read More

![Hacker for Hire [2024]: How Easy is it to Find a Professional Hacker?](https://hackproofhacks.com/wp-content/uploads/2024/10/a-sleek-and-mysterious-image-featuring-a-hacker-se-7CGym8oRS3Kut4tG63WSZA-BhIfumolQYiEiXkPmCO0_Q-768x479.avif)









Step 6: Developing Social Engineering Skills
In ethical hacking, social engineering is one of the most effective techniques to bypass security systems. To truly understand how to start ethical hacking like a pro, you need to master the psychological aspects of security breaches, which often involve manipulating human behavior to gain access to sensitive information. Social engineering targets the weakest link in security—the human element.
What is Social Engineering in Ethical Hacking?
Social engineering is the art of influencing people to reveal confidential information or perform actions that compromise security. It’s often more successful than technical attacks because people are naturally trusting and can be manipulated with the right techniques.
Common Social Engineering Tactics
Developing Effective Social Engineering Skills
To become skilled at social engineering in ethical hacking, focus on psychology and persuasion. You need to understand what makes people trust or act quickly without verifying details.
Practical Steps to Develop Social Engineering Skills
Tip: In Hackers Real World, our membership community, we offer exclusive insights into advanced social engineering tactics and provide examples based on real-world scenarios.
Ethical Responsibility in Social Engineering
Ethical hackers must remember to act responsibly. Social engineering can cause significant harm if used improperly. Always get permission and follow ethical guidelines when conducting any form of social engineering.
Mastering social engineering is crucial in how to start ethical hacking. It allows you to think beyond code and tools, focusing on the human element that often exposes even the most secure systems. With strong social engineering skills, you’ll have a complete understanding of the many ways to assess and strengthen security.