Introduction
Today, In this part of the Ethical Hacking Series, we will learn about Reconnaissance. Reconnaissance is the first step in ethical hacking and penetration testing. It involves gathering as much information as possible about a target before attempting any hacks. That is why it is also known as Information Gathering. It is a research phase where a hacker learns about their target’s systems, networks, and potential vulnerabilities.
This part of the Ethical Hacking series will cover various tools and techniques for effective reconnaissance. We will explore both passive and active methods. Passive reconnaissance involves gathering information without directly interacting with the target. This can include looking up domain details or scanning public social media profiles. Active reconnaissance, on the other hand, involves directly engaging with the target, such as performing port scans or network sweeps.
By the end of this guide, you’ll understand how to gather and analyze information about your target effectively. Whether you are a beginner or an experienced hacker, mastering these reconnaissance techniques is crucial for your success. Let’s dive in and start uncovering the secrets of our targets.
Understanding Reconnaissance
Reconnaissance is a crucial part of the ethical hacking process. It involves gathering information about your target to understand its structure, weaknesses, and potential vulnerabilities. There are two main types of reconnaissance: passive and active.
Passive Reconnaissance
Passive reconnaissance is about collecting information without directly interacting with the target. This method helps avoid detection. It often involves searching public records and online databases. Examples include:
- Whois Lookups: Checking domain registration details.
- Social Media: Gathering information from social profiles.
- DNS Enumeration: Discovering domain name system records.
Passive reconnaissance is like being a detective, gathering clues without alerting the target.
Active Reconnaissance
Active reconnaissance involves directly interacting with the target to collect data. This method is more likely to be detected but provides detailed information. Examples include:
- Port Scanning: Checking for open ports on a server.
- Network Scanning: Identifying active devices on a network.
- Vulnerability Scanning: Searching for known vulnerabilities.
Active reconnaissance is like knocking on doors to see who answers. It’s more intrusive but reveals valuable details.
Why is Reconnaissance Important?
Reconnaissance is the foundation of any hacking operation. It helps hackers understand the target’s environment and identify weak points. Simply put, the more you know about your target, the better prepared you will be. Good reconnaissance can reveal weaknesses that can be exploited later. It helps hackers plan an attack with precision and it reduces the risk of detection.
Stages of Reconnaissance
Reconnaissance generally involves two main stages: initial information gathering and analysis.
Initial Information Gathering:
- Collect basic data about the target.
- Use tools to gather domain info, IP addresses, and network structure.
Analysis and Interpretation:
- Analyze the collected data to identify patterns and potential vulnerabilities.
- Develop a strategy for the next steps in the hacking process.
Reconnaissance is typically divided into two main stages: initial information gathering and analysis and interpretation. Both stages are essential for building a comprehensive understanding of the target.
Stage 1: Initial Information Gathering
This stage involves collecting as much data as possible about the target without interacting directly with its systems. Here are some common methods:
- Whois Lookup:
- Whois databases contain registration details about domains.
- Use tools like whois to find the domain owner’s name, contact information, and registration dates.
- DNS Enumeration:
- DNS (Domain Name System) records can reveal valuable information about the target’s infrastructure.
- Tools like nslookup and dig help find IP addresses, mail servers, and other domain-related information.
- Social Media Mining:
- Social media platforms can provide insights into the target’s employees, locations, and activities.
- Use tools like Maltego to gather and visualize social media data.
- Search Engines:
- Google and other search engines can uncover public information about the target.
- Use advanced search operators to find specific details (e.g., site
.com “confidential”).
- Public Databases:
- Access public databases and archives for information about the target.
- This can include financial records, company filings, and news articles.
Stage 2: Analysis and Interpretation
Once you have gathered the initial data, the next step is to analyze and interpret it. This stage is about making sense of the collected information to identify potential vulnerabilities and plan your attack strategy.
- Data Organization:
- Sort and organize the collected data to make it easier to analyze.
- Create lists of IP addresses, domain names, and key personnel.
- Pattern Identification:
- Look for patterns and relationships in the data.
- Identify common IP addresses, frequently mentioned servers, and recurring usernames.
- Vulnerability Detection:
- Compare the collected information against known vulnerabilities.
- Use databases like CVE (Common Vulnerabilities and Exposures) to find relevant exploits.
- Target Profiling:
- Build a profile of the target based on the analyzed data.
- Understand the target’s network structure, security measures, and potential weak points.
- Strategy Development:
- Develop a plan for the next phases of penetration testing.
- Decide which vulnerabilities to test and the methods to use.
Tools for Passive Reconnaissance
Passive reconnaissance involves gathering information about a target without directly interacting with it. This helps avoid detection while collecting valuable data. Here are some essential tools for passive reconnaissance.
1. Whois Lookup
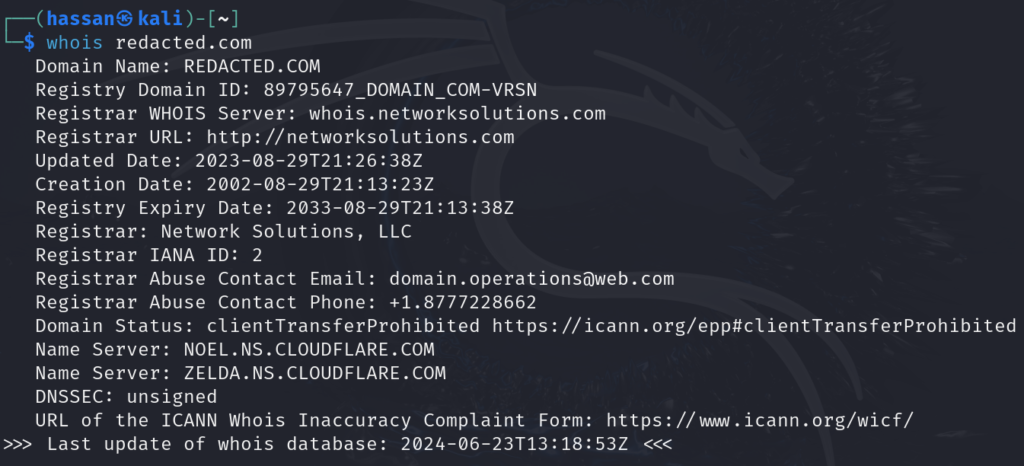
Whois is a protocol that queries databases to obtain domain registration information. It provides details like the domain owner, registration date, and contact information.
How to Use Whois:
- Open your terminal or command prompt.
- Type
whois example.com(replace “example.com” with the target domain). - Review the output for useful information about the domain owner, administrative contacts, and more.
2. DNS Enumeration
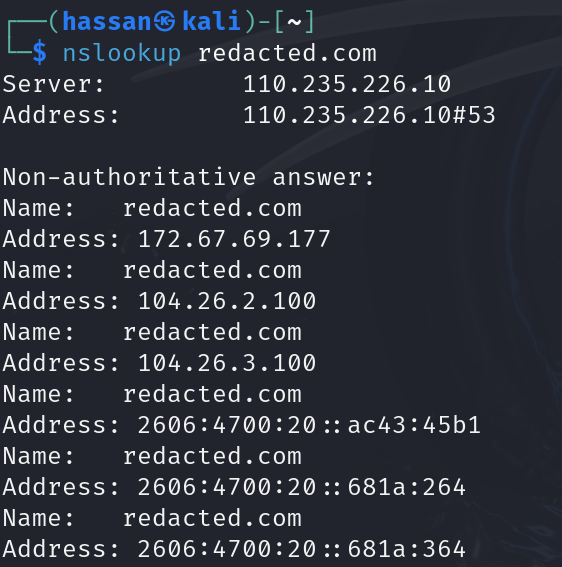
DNS enumeration involves discovering details about a domain’s DNS records, such as subdomains, mail servers, and name servers. Tools like nslookup, dig, and DNSRecon are useful for this purpose.
- Using nslookup:
- Open your terminal.
- Type
nslookup example.com. - This will show you the IP address and name server details of the domain.
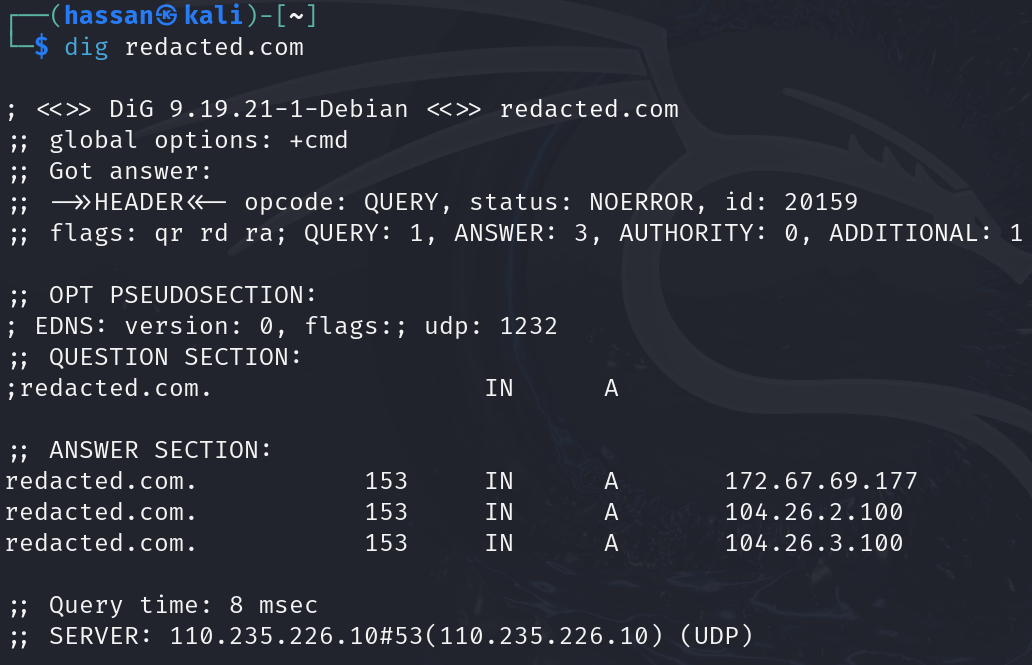
- Using dig:
- Type
dig example.comin your terminal. - dig provides more detailed information about the domain’s DNS records.
- Type
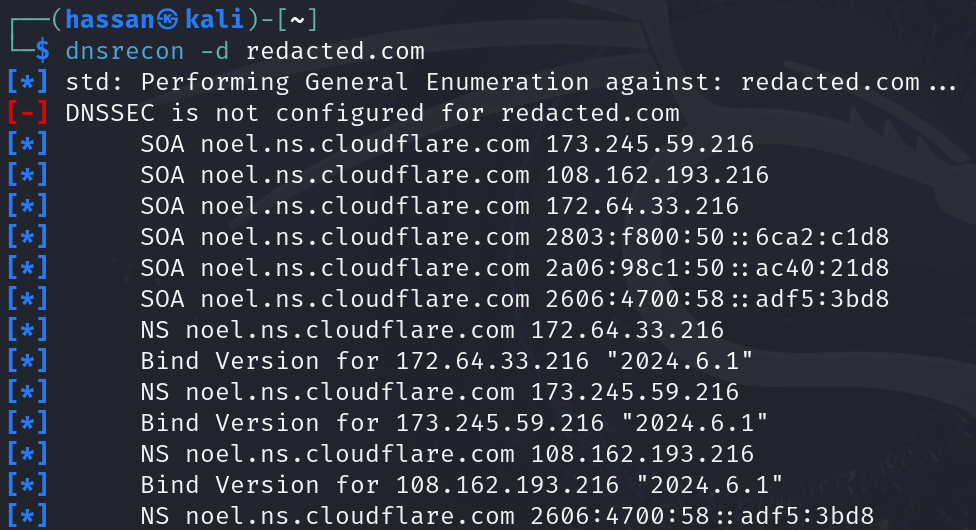
- Using DNSRecon:
- Install DNSRecon with
sudo apt-get install dnsrecon. - Run it with
dnsrecon -d example.com. - This tool provides comprehensive DNS enumeration results.
- Install DNSRecon with
3. Social Media and Public Sources
Social media platforms and public sources can reveal a lot about a target. Tools like Maltego can help visualize and analyze data from these sources.
- Using Maltego:
- Install Maltego from its official website.
- Use its graphical interface to input the target’s name or domain.
- Maltego will map out relationships and connections, providing a visual representation of the gathered data.
- Manual Search:
4. Google Dorking
Google Dorking uses advanced search techniques to find information that isn’t readily visible through normal searches. It can uncover hidden pages, files, and data on websites.
Basic Google Dorks:
site:example.com– Limits search results to the specified site.filetype:pdf– Finds PDF files.intitle:"index of"– Looks for directory listings that might reveal sensitive information.
I have already written a complete guide on Google Dorking. You can find it here. Using these tools, you can gather a wealth of information without alerting your target. Together, these passive reconnaissance tools form a solid foundation for your hacking endeavors, providing critical data while keeping your activities undetected.
Tools for Active Reconnaissance
Active reconnaissance involves directly interacting with the target to gather detailed information. This approach is more intrusive than passive reconnaissance, and it carries a higher risk of detection. However, it provides comprehensive data about the target’s systems and network. Here are some essential tools for active reconnaissance.
1. Port Scanning
Port scanning is used to identify open ports on a target system. Open ports can reveal running services and potential entry points.
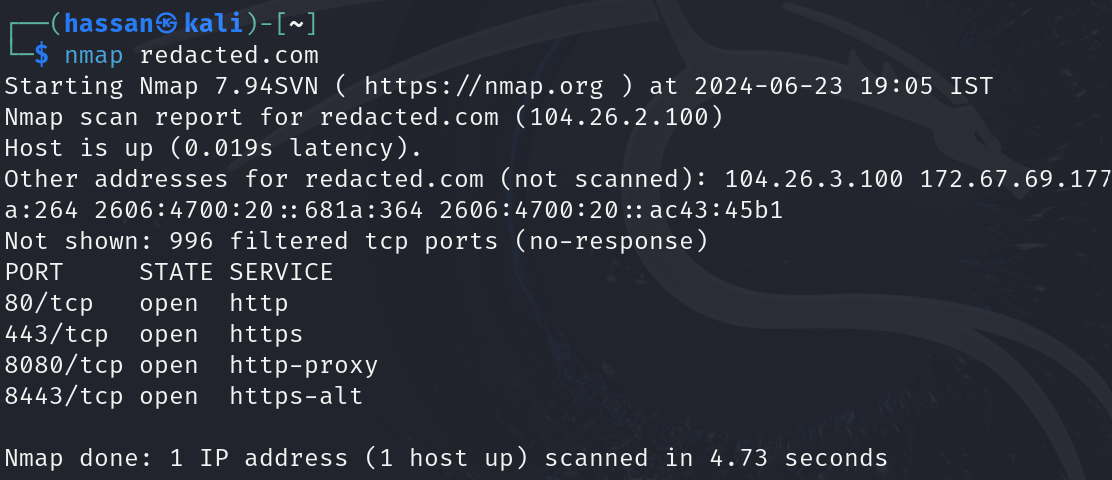
- Using Nmap:
- Installation: Install Nmap by typing
sudo apt-get install nmap. - Basic Scan: Run a basic scan with
nmap example.com. - Detailed Scan: Use
nmap -sV -O example.comto get detailed information about the services and operating system.
- Installation: Install Nmap by typing
2. Network Scanning
Network scanning identifies active devices on a network. It helps map the network and find potential targets.
- Using Netdiscover:
- Installation: Install Netdiscover with
sudo apt-get install netdiscover. - Running Netdiscover: Type
sudo netdiscoverto start scanning the network. This tool will list all active devices along with their IP addresses and MAC addresses.
- Installation: Install Netdiscover with
- Using Arp-scan:
- Installation: Install arp-scan with
sudo apt-get install arp-scan. - Running Arp-scan: Type
sudo arp-scan -lto scan the local network. This tool also provides information about active devices on the network.
- Installation: Install arp-scan with
3. Vulnerability Scanning
Vulnerability scanning identifies known vulnerabilities in the target’s systems. These tools check for outdated software, misconfigurations, and other security issues.
- Using Nessus:
- Installation: Download and install Nessus from the official website.
- Running Nessus: Open Nessus in your browser, create a new scan, and enter the target’s IP address. Nessus will scan the target and provide a detailed report on found vulnerabilities.
- Using OpenVAS:
- Installation: Install OpenVAS by typing
sudo apt-get install openvas. - Running OpenVAS: Open OpenVAS in your browser, create a new task, and enter the target’s IP address. OpenVAS will scan for vulnerabilities and generate a comprehensive report.
- Installation: Install OpenVAS by typing
Active reconnaissance provides detailed insights into a target’s network and systems. By using these tools, you can gather crucial information to plan your next steps in the ethical hacking process. However, remember that active reconnaissance increases the risk of detection, so use these tools carefully.
OSINT (Open Source Intelligence) Tools
Open Source Intelligence (OSINT) involves gathering information from publicly available sources. This type of intelligence gathering can reveal a lot about your target without direct interaction. Here are some essential OSINT tools that we haven’t discussed yet.
1. Shodan
Shodan is a search engine for internet-connected devices. It helps you find servers, webcams, routers, and other devices connected to the internet.
Using Shodan:
- Website: Visit shodan.io.
- Search: Type in a target’s IP address, domain, or keyword.
- Results: Shodan will show details about the connected devices, including open ports and running services.
For full tutorial of Shodan, you can check this guide.
2. Censys
Censys is another search engine for internet-connected devices, similar to Shodan but with its own unique features and data.
Using Censys:
- Website: Visit censys.io.
- Search: Enter the target’s IP address, domain, or AS number.
- Results: Censys provides detailed information about the devices, including certificates, open ports, and service versions.
3. TheHarvester
TheHarvester is a tool for gathering email addresses, subdomains, and other information from various public sources.
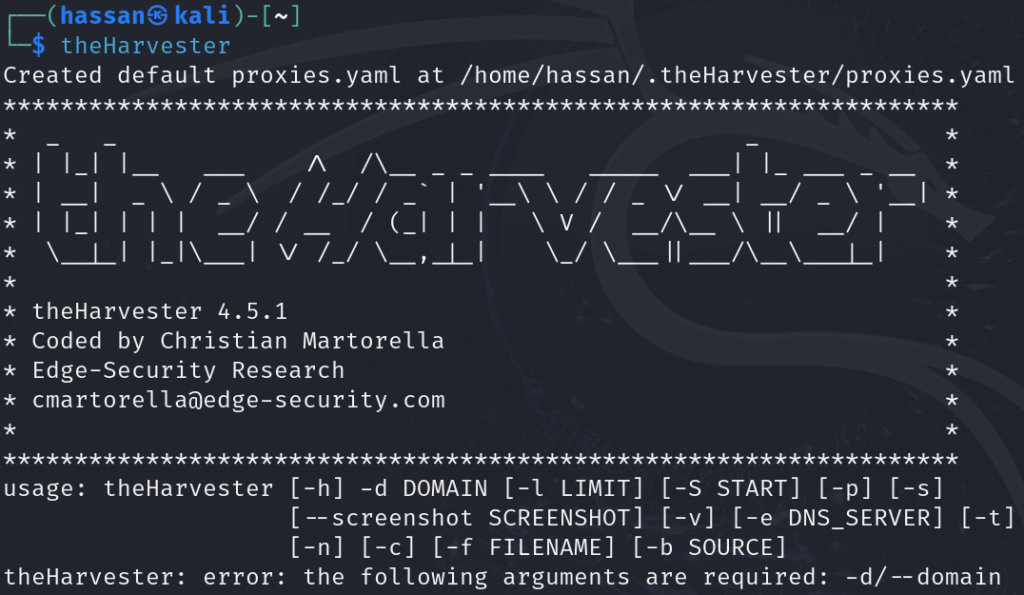
- Installation: Install TheHarvester by typing sudo apt-get install theharvester.
- Usage: Run
theharvester -d example.com -l 500 -b google(replace “example.com” with your target domain and adjust the limit as needed). - Output: TheHarvester will collect and display information about emails, subdomains, and more.
4. Recon-ng
Recon-ng is a full-featured reconnaissance framework written in Python. It has modules for collecting various types of data from public sources.
- Installation: Install Recon-ng by typing
sudo apt-get install recon-ng. - Starting Recon-ng: Type
recon-ngin the terminal. - Modules: Use commands like marketplace search to find modules, and marketplace
install <module>to install them. - Running Modules: Execute modules with
run <module>, providing necessary inputs.
5. SpiderFoot
SpiderFoot is an automated OSINT tool that collects a wide range of information from many different sources.
- Installation: Install SpiderFoot by typing
sudo apt-get install spiderfoot. - Running SpiderFoot: Open it in your browser by typing spiderfoot in the terminal and navigating to the provided URL.
- Configuration: Create a new scan, enter your target’s domain, and select the modules to run.
- Results: SpiderFoot will display detailed reports on found data, including social media profiles, email addresses, and more.
OSINT tools are invaluable for gathering intelligence without interacting with the target directly. Using these tools, you can gather extensive information about your target.
Web Application Reconnaissance
Web application reconnaissance involves gathering information about a web application to find potential vulnerabilities. This process is crucial for understanding the target’s structure and identifying weaknesses. Here are some essential tools and techniques for web application reconnaissance.
1. Web Crawling
Web crawling involves systematically browsing a website to index its content and structure. This helps identify all accessible pages and directories.
- Using Burp Suite:
- Installation: Download and install Burp Suite from its official website.
- Setup: Open Burp Suite and configure your browser to use Burp’s proxy.
- Crawling: Use the Spider tool to crawl the target website. This will map out the site’s structure and discover hidden pages.
- Using OWASP ZAP:
- Installation: Download and install OWASP ZAP from its official website.
- Setup: Open ZAP and configure your browser to use ZAP’s proxy.
- Crawling: Use the Spider tool to crawl the target website and gather a comprehensive list of URLs.
2. Directory and File Discovery
Directory and file discovery involves finding hidden directories and files on a web server. These can contain sensitive information or provide entry points for further attacks.
- Using Dirb:
- Installation: Install Dirb by typing
sudo apt-get install dirb. - Running Dirb: Run
dirb http://example.com(replace “example.com” with the target website). Dirb will search for common directories and files. - Results: Review the output for directories and files that can be further investigated.
- Installation: Install Dirb by typing
- Using Gobuster:
- Installation: Install Gobuster by typing
sudo apt-get install gobuster. - Running Gobuster: Run
gobuster dir -u http://example.com -w /usr/share/wordlists/dirb/common.txt(replace “example.com” with the target website). Gobuster uses a wordlist to find directories and files. - Results: Check the output for potentially interesting directories and files.
- Installation: Install Gobuster by typing
3. Examining HTTP Headers
HTTP headers can provide useful information about the web server and application. They can reveal server software, security mechanisms, and other details.
- Using cURL:
- Installation: cURL is usually pre-installed. If not, install it with
sudo apt-get install curl. - Fetching Headers: Run
curl -I http://example.com(replace “example.com” with the target website). This command retrieves the HTTP headers. - Analysis: Review the headers for information about server software, cookies, and security policies.
- Installation: cURL is usually pre-installed. If not, install it with
- Using Burp Suite or OWASP ZAP:
- Headers: Both tools capture HTTP headers during web crawling and scanning.
- Analysis: Inspect the captured headers to gather insights about the web application.
Web application reconnaissance helps uncover valuable information about the structure and security of a web application. By using these techniques, you can gain a deep understanding of the target web application and pave the way for further analysis and potential vulnerability discovery.
Advanced Reconnaissance Techniques
Advanced reconnaissance techniques delve deeper into the target’s infrastructure and can uncover more subtle vulnerabilities. These methods often require a higher level of skill and understanding. Here are some advanced techniques that you can use to gather detailed information about your target.
1. Subdomain Enumeration
Subdomain enumeration helps identify additional domains associated with the target. These subdomains can reveal hidden services or less secure parts of the infrastructure.
- Using Sublist3r:
- Installation: Install Sublist3r by running
sudo apt-get install sublist3r. - Running Sublist3r: Execute
sublist3r -d example.com(replace “example.com” with the target domain). Sublist3r will gather a list of subdomains. - Results: Review the list of subdomains for additional targets.
- Installation: Install Sublist3r by running
- Using Amass:
- Installation: Install Amass by typing
sudo apt-get install amass. - Running Amass: Run
amass enum -d example.com(replace “example.com” with the target domain). Amass performs a comprehensive enumeration of subdomains. - Results: Check the output for potential entry points.
- Installation: Install Amass by typing
2. Certificate Transparency Logs
Certificate transparency logs provide information about SSL certificates issued for the target domain. This can reveal subdomains and other related domains.
- Using crt.sh:
- Website: Visit crt.sh.
- Search: Enter the target domain in the search bar.
- Results: crt.sh will display SSL certificates issued for the domain, revealing subdomains and other associated domains.
3. Reverse IP Lookup
Reverse IP lookup finds all domains hosted on the same server as the target. This can help identify additional targets or less secure domains.
- Using Reverse IP Lookup Tools:
- Website: Use tools like viewdns.info or similar services.
- Search: Enter the target’s IP address.
- Results: The tool will list all domains hosted on that IP address.
4. Metadata Extraction
Metadata extraction involves analyzing documents and images for hidden information such as usernames, software versions, and creation dates.
- Using ExifTool:
- Installation: Install ExifTool by typing
sudo apt-get install exiftool. - Running ExifTool: Execute
exiftool filename(replace “filename” with the document or image file name). - Results: Review the extracted metadata for useful information.
- Installation: Install ExifTool by typing
5. Using Metasploit for Reconnaissance
Metasploit is a powerful framework commonly used for penetration testing and reconnaissance. It includes modules specifically designed for information gathering.
- Introduction to Metasploit:
- Installation: Install Metasploit by typing
sudo apt-get install metasploit-framework. - Usage: Open Metasploit by typing
msfconsolein the terminal. This will bring up the Metasploit command line interface.
- Installation: Install Metasploit by typing
- Recon Modules in Metasploit:
- Search Modules: Use
search reconto find reconnaissance modules. - Use Modules: Select a module with
use <module>, then configure it withset <option> <value>. - Run Module: Execute the module with
runto gather information about the target.
- Search Modules: Use
6. Custom Scripts and Automation
Automating reconnaissance tasks can save time and ensure comprehensive data collection. Custom scripts in Python and Bash can be very effective.
- Writing Custom Scripts:
- Python: Use Python libraries like requests for web scraping and scapy for network scanning.
- Bash: Utilize Bash scripting to automate running tools and commands.
- Example Python Script:
import requests
def get_title(url):
response = requests.get(url)
if response.status_code == 200:
start = response.text.find('<title>') + len('<title>')
end = response.text.find('</title>')
return response.text[start:end]
return None
url = 'http://example.com'
print(get_title(url))- Example Bash Script:
#!/bin/bash
for url in $(cat urls.txt); do
curl -s $url | grep '<title>'
doneAdvanced reconnaissance techniques provide deeper insights into the target’s infrastructure. Subdomain enumeration tools like Sublist3r and Amass reveal additional domains. Certificate transparency logs from crt.sh show issued SSL certificates. Reverse IP lookup identifies all domains on the same server. Metadata extraction with ExifTool reveals hidden information in documents and images. Metasploit’s recon modules offer powerful information-gathering capabilities. Custom scripts in Python and Bash can automate and streamline reconnaissance tasks. By employing these advanced techniques, you can gather comprehensive data about your target.
Conclusion
Reconnaissance is the foundation of ethical hacking. It’s the first step where you gather information about your target. The more you know, the better equipped you are. In this guide, we covered various tools and techniques to help you conduct effective reconnaissance.
We started with understanding the difference between active and passive reconnaissance. Passive methods are safer because they don’t alert the target. Active methods give more detailed information but carry a higher risk of detection.
We explored tools like WHOIS, Nmap, Sublist3r, and Burp Suite. Each tool has its unique strengths and can provide valuable insights. You also learned about important concepts like DNS enumeration, network scanning, and vulnerability assessment.
Through practical examples, you saw how these tools and techniques come together in real-world scenarios. From corporate networks to web applications, thorough reconnaissance can reveal critical vulnerabilities.
Remember, the key to successful reconnaissance is patience and attention to detail. Document everything you find and analyze it carefully. This will help you plan your next steps and increase your chances of success.
As you practice these skills, you’ll gain proficiency and confidence. Continue to study and explore new tools and techniques. Reconnaissance is a continuing process that requires continuous progress.
In the next part of this series, we’ll dive deeper into advanced hacking techniques. Stay tuned and keep honing your skills. Happy hacking!