
The recent news of a Dell data breach has raised eyebrows across the tech world, especially since the hacker managed to get their hands on a whopping 49 million customer records. This breach carried out through a sneaky move with a partner portal API, highlights just how vulnerable digital systems can be and why beefing up cybersecurity is crucial.
Highlights of Dell Data Breach
- Dell data breach exposed 49 million customer records via a partner portal.
- The threat actor Menelik, got access to order details like warranties and names.
- Dell received Menelik’s emails but hasn’t shared much during the investigation.
- TechCrunch shared news of the breach, showing how APIs can make companies vulnerable.
- This highlights why companies need better security to protect customer info.
BleepingComputer broke the story, reporting Dell’s efforts to let affected customers know about the breach and the fact that their personal info had been compromised. The stolen data included everything from warranty details and service tags to customer names, installation info, and order numbers.
The threat actor behind this mess, going by the name Menelik, wasted no time trying to cash in. They swiftly put the stolen data up for sale on a hacking forum called Breached on April 28th. But the post didn’t last long, as moderators quickly took it down, showing just how serious this breach was.
In an interview with BleepingComputer, Menelik spilled the beans on how they pulled it off. They exploited a portal meant for Dell’s partners, resellers, and retailers by setting up multiple accounts under fake company names. Shockingly, they got access within just two days, skipping past verification like it was no big deal.
“It’s super easy to register as a Partner. You just fill out a form,” Menelik said. “You give some company details, say why you want to be a partner, and they just approve you and give you access to this ‘authorized’ portal. I just made my own accounts like that. It took about 24-48 hours.”
Once they were in, Menelik used a program they’d cooked up to generate 7-digit service tags. They fed these into the portal to start scraping data. Dell’s security was so lax that Menelik managed to grab data from 49 million customer records by sending 5,000 requests per minute for three weeks, all without Dell noticing a thing.
The loot Menelik scored included everything from monitors to Alienware notebooks, Chromebooks, Inspiron gadgets, Latitude laptops, and more.
Even though Menelik claims they sent emails to Dell on April 12th and 14th to flag the security flaw, they admitted to grabbing the records before Dell did anything about it. Dell did confirm getting the emails but stayed mum on what exactly went down, citing an ongoing police investigation.
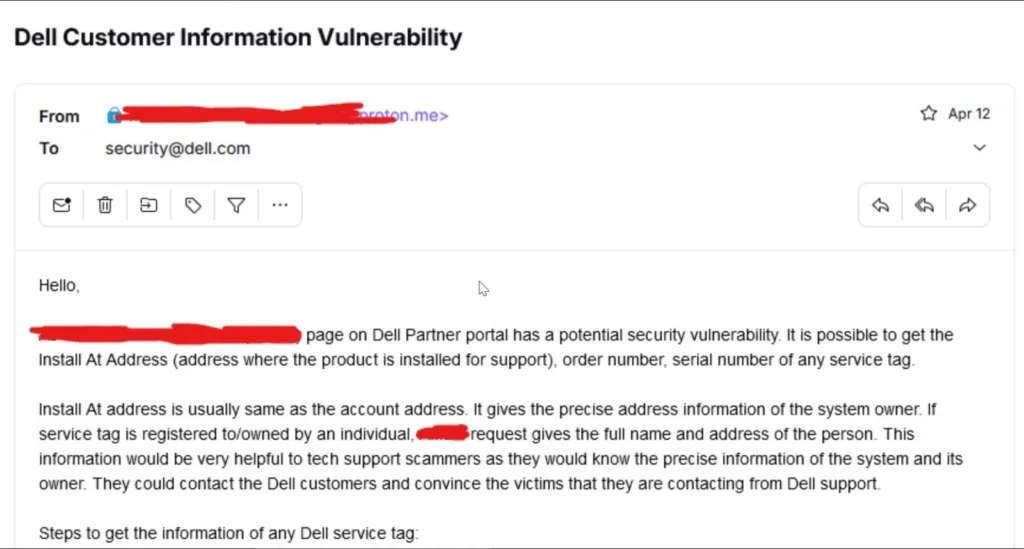
Source: Menelik
This breach, first brought to light by TechCrunch, serves as a wake-up call about the dangers of the digital world and why companies need to step up their game when it comes to keeping data safe. With similar breaches hitting big names like Facebook, Twitter, and Trello lately, it’s clear that tighter security measures are a must.
As we ponder this cyber mess, it highlights the dangers online. However, with caution and attention, we can protect our data and customers. It’s a reminder of the risks, but also of our ability to navigate them safely.
Wiretap System Breach Exposes Risks of Government-Installed Backdoors in U.S. Telecoms [2024]
Introduction In recent news, the wiretap system breach by China-backed hackers has raised significant alarm…
Password Cracking with Hydra: Step-by-Step Ethical Hacking Guide [Part 11 of Ethical Hacking Series]
Introduction to Password Cracking Password cracking is a method used in cybersecurity to recover passwords…
Step-by-Step Guide to Crack WiFi Passwords with Aircrack-ng [Part 10 of Ethical Hacking Series]
Introduction to Wireless Network Haking Welcome to Part 10 of our Ethical Hacking series, where…
Web Attacks: 7 Tools for OWASP Top 10 Testing [Part 9 of Ethical Hacking Series]
Introduction Welcome to Part 9 of our Ethical Hacking series, where we dive into the…
Post-Exploitation Mastery: Maintaining Access Techniques Explained [Part 8 of Ethical Hacking Series]
Introduction Welcome to Part 8 of our Ethical Hacking series: Post-Exploitation Techniques: Maintaining Access. In…
Stay Safe from Rising Quishing Attack EV at Charging Stations
Electric vehicle (EV) owners need to be cautious as a new cyber threat known as…



![Step-by-Step Guide to Crack WiFi Passwords with Aircrack-ng (Wireless Password Hacking) [Part 10 of Ethical hacking series]](https://hackproofhacks.com/wp-content/uploads/2024/09/Grey-Minimalist-Tips-Blog-Banner-8-1024x576.png)
![Web Attacks: 7 Tools for OWASP Top 10 Testing [part 9 of Ethical Hacking Series]](https://hackproofhacks.com/wp-content/uploads/2024/09/Grey-Minimalist-Tips-Blog-Banner-7-1024x576.png)





