Preparation Phase
Lean engineering teams prioritize lightweight tools and cross-training to handle incidents without dedicated security staff.
Establish a core response team of 3-5 members with defined roles: Incident Commander (senior engineer for decisions), Tech Lead (root cause analysis), and Communications Lead (updates stakeholders).
Inventory critical assets like code repos, Vercel deployments, and customer data stores, then set up monitoring with free tiers of tools such as Sentry for errors and UptimeRobot for availability.
- Document contact lists in a shared Notion or Google Sheet, including on-call rotations.
- Run quarterly tabletop exercises simulating breaches like API key leaks or DDoS on your Next.js apps.
- Automate backups via GitHub Actions and test restores weekly to minimize downtime.
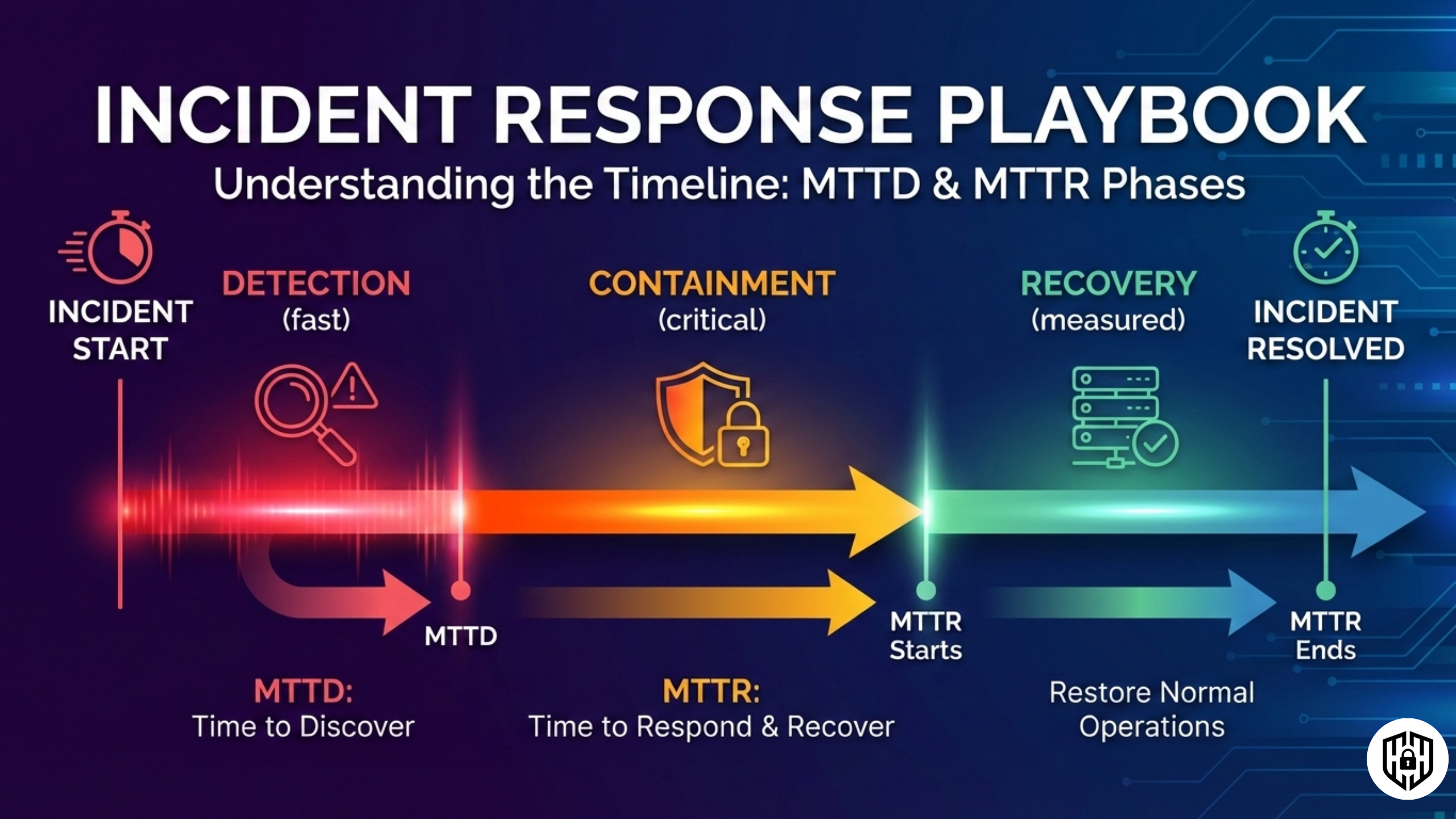
Detection and Identification
Rapid detection relies on integrated alerts rather than 24/7 monitoring.
Configure GitHub Dependabot, Vercel logs, and Cloudflare for anomaly notifications pushed to Slack channels.
Classify incidents by severity: P0 (production outage), P1 (data exposure), P2 (degraded perf), using indicators like unusual 5xx errors or failed logins.
Triage within 15 minutes by gathering logs via vercel logs and checking for IOCs with open-source tools like Holehe for email recon or FFUF for endpoint fuzzing.
Containment Strategies
Isolate threats without halting velocity: for suspected breaches, rotate API keys immediately and deploy Vercel previews to bypass prod.
Use Docker containers for sandboxed analysis, revoking GitHub tokens and IP whitelisting via Cloudflare.
- Short-term: Disable compromised endpoints with Vercel redirects.
- Long-term: Enforce least-privilege via Vercel Access and environment variables.
Eradication and Recovery
Scan with Nikto or WhatWeb on staging mirrors, then patch via PRs with automated tests.
Restore from Git history or Vercel rollbacks, monitoring for re-exploitation with Burp Suite scans post-deploy.
Validate recovery through canary deploys: 10% traffic first, scaling if metrics hold.
Post-Incident Review
Conduct blameless retrospectives within 48 hours, documenting in a GitHub Issue template with root cause, timeline, and action items.
Update playbooks and run a follow-up drill; track MTTR improvements quarterly.
Lean Team Tools
| Category | Recommended Tools | Why for Lean Teams |
|---|---|---|
| Monitoring | Sentry, Vercel Analytics | Free tiers, integrates with your stack |
| Analysis | Burp Suite Community, FFUF | No-cost pentest essentials |
| Comms | Slack/Telegram on-call | Instant escalation without emails |
| Automation | GitHub Actions | CI/CD for patches and backups |
Implement Your Playbook Today
Download the Markdown template, customize for your Vercel/Next.js stack, and run your first simulation this week.
References & Further Reading
Use these to deepen your playbook and align with standards.
