
Hello guys! Are you here to learn how to use John the ripper commands? Don’t worry! today, i am going to teach you everything about John the Ripper like how to install john, what are john the ripper commands and how to use it! It is a legendary password-cracking tool. Get ready, because we’re going to thoroughly explore the usage of john the ripper commands and every part of this powerful tool.
John the Ripper, affectionately known as “John” in the cybersecurity community, is like a Swiss Army knife for password cracking. If you master john the ripper commands then what you can efficiently crack passwords, perform penetration testing and recover lost passwords.
Table of Contents
What Can John the Ripper Do?
Well, by using John the Ripper Commands , you can crack encrypted passwords using various techniques like dictionary attacks, brute-force attacks, and hybrids.
What’s cool about John the Ripper is its support for different hashing algorithms like MD5 and SHA-256. This means you can customize your password cracking methods based on the system you’re targeting. Plus, it’s great for testing password policies and boosting overall cybersecurity.
Additionally, John the Ripper offers advanced features like rule-based password generation, allowing you to create custom rules for generating password guesses based on patterns, common substitutions, and character sets.
Overall, John the Ripper commands and its extensive functionalities make it a favorite among penetration testers, security professionals, and ethical hackers for assessing password security, identifying weak passwords, and evaluating overall system security.
Understanding How John Works
John the Ripper is a powerful password cracking tool used by cybersecurity experts to test the strength of passwords. It works by trying different combinations of characters until it finds the correct password. To use it, you need to understand some basic john the ripper commands.
Firstly, you need to specify the file containing the password hashes you want to crack using its commands. For example, “john –format=NT hash.txt” tells John the Ripper to crack NT hashes stored in the file hash.txt.
Next, you can specify various options to customize the cracking process using John the Ripper commands. For instance, you can use the “–wordlist” command followed by the path to a wordlist file to use a list of common passwords for cracking.
You can also use rules to modify how John the Ripper generates and tests passwords using John the Ripper commands. The “–rules” command lets you apply different rulesets, such as mangling rules, to increase the chances of cracking passwords.
Once you’ve set up the command with the desired options, you simply run John the Ripper, and it will start the cracking process using the specified parameters. It will try various combinations and permutations until it successfully cracks the passwords or exhausts all possibilities.
Step-by-Step Tutorial: Using John the Ripper in Kali Linux
Now, a question must be arising in your mind i.e., how to install this tool and start playing with john the ripper commands? Well, you can install John The ripper on your Kali Linux Machine.
Don’t know have a Kali linux operating system? No problem, here’s the video to quickly install it in your pendrive. So, Let’s get started!
- Install Kali Linux: First things first, make sure you’ve got Kali Linux up and running on your system. If not, head over to their website, grab the latest version, and follow the installation steps.
- Update Repositories: Once you’re in Kali Linux, let’s ensure everything’s up-to-date. Open up the terminal and type:
$ sudo apt-get update - Install John the Ripper: Now, let’s bring in John the Ripper. All that you need is a simple command:
$ sudo apt-get install john - Navigate to John’s Directory: John’s home is in the /usr/share/john directory. Let’s head there in the terminal.
- Choose Wordlists: Time to pick some wordlists for cracking passwords. John’s got a bunch to choose from, covering different languages and scenarios. Just place them in the right directory.
- Prepare Password Hashes: Got some password hashes you want to crack? Great! You can grab them from password files, databases, or system settings.
- Run John the Ripper: This is where the magic happens! Let’s fire up John and give it some instructions. We’ll tell it which wordlist to use, what format the hashes are in, and any special rules to follow. Here’s an example with some detailed options:
$ john –wordlist=wordlist.txt –format=NT –rules:Jumbo hashes.txt
–wordlist=<path>: Specifies the path to the wordlist file.
–format=<format>: Specifies the format of the password hashes.
–rules=<rule>: Applies transformation rules to the wordlist entries.
For example, –rules:Jumbo applies a set of extra transformation rules to increase the chances of cracking passwords. - Monitor Progress: Now, keep an eye on John as it does its thing. Depending on how tough the passwords are, it might take a bit of time.
- Analyze Results: Once John’s done, it’s time to see what it found. Check out the cracked passwords and use them to see how secure your system really is.
- Explore Additional Options: Feel like diving deeper? John’s got plenty of other tricks up its sleeve. Take a look at the documentation and play around with different settings to fine-tune your cracking game.
John the Ripper Commands
These are some of the most important john the ripper commands that you are going to need in this jouney. These john the ripper commands are also known as Options and Flags. Experimenting with these commands and understanding how they work will help you become more proficient at cracking passwords and assessing system security.
- –wordlist=<path>: This option tells John which wordlist to use for password cracking. You provide the path to the wordlist file, and John will try each word in it to crack passwords.
- –format=<format>: Here, you specify the format of the password hashes you’re trying to crack. Different systems and applications store passwords in different ways, so this option helps John understand how to handle them.
- –rules=<rule>: With this flag, you can apply transformation rules to the words in your wordlist. It’s like giving John a set of instructions on how to modify each word before trying it as a password.
- –incremental[=<mode>]: This option is all about trying different combinations of characters to crack passwords. You can specify a mode (like “alpha” for just letters, “digits” for just numbers, etc.) or leave it blank to try all possible combinations.
- –single: When you use this flag, John will only crack passwords that are stored as single hashes. This can speed up the process if you know you’re dealing with single hashes.
- –fork=<number>: This one controls how many parallel processes John should use for cracking. The more processes, the faster it might go, but it can also use up a lot of system resources.
- –show: After John finishes cracking, you can use this flag to show the cracked passwords. It’s handy for seeing what John found without having to dig through files.
- –test: Use this flag to test your configuration and see if everything’s set up correctly before you start cracking passwords. It helps catch any mistakes early on.
- –pot=<file>: When John cracks a password, it puts it in a file called a “potfile.” With this option, you can specify the name and location of the potfile.
- –external=<module>: This flag lets you use external “subordinate” modules with John. These modules can extend John’s capabilities or provide additional features for specific tasks.
If you want to know more about these options or flags, then you can see the instruction manual of John the Ripper.
Example Usage of John the Ripper Commands:
Let’s dive into some practical examples of using John the Ripper commands for cracking passwords using different techniques.
1. Cracking Passwords with Brute Force:
Imagine you have a password-protected ZIP file named “secure.zip” and you suspect that the password might be a combination of numbers and lowercase letters. You can use John the Ripper to perform a brute force attack to crack the password.
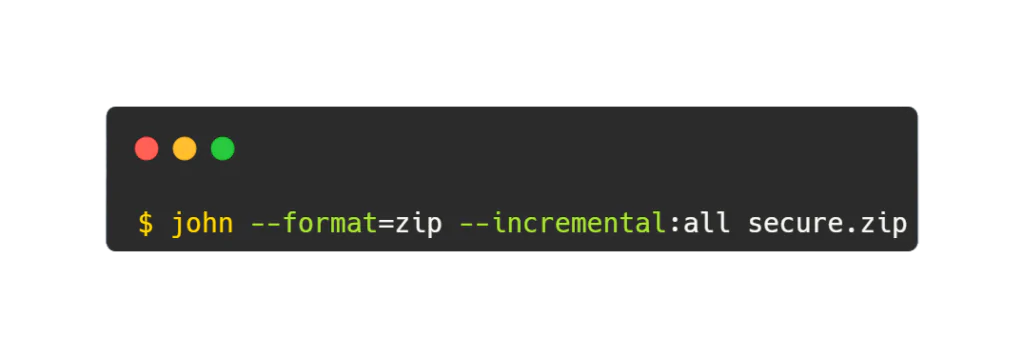
In this command:
–format=zip specifies the format of the encrypted file.
–incremental:all instructs John to use incremental mode, trying all possible combinations of characters until the correct password is found.
2. Using Wordlists for Cracking:
Suppose you have a list of common passwords in a file named “common.txt” and you want to use it to crack the password of a user account named “user1”.
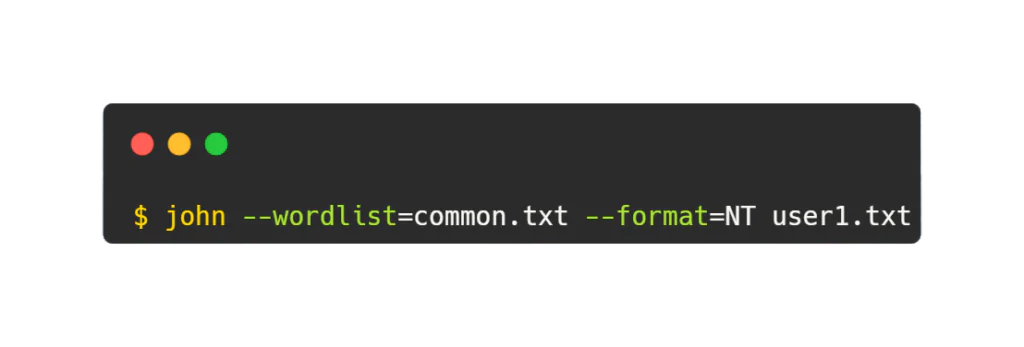
Here:
–wordlist=common.txt specifies the path to the wordlist file containing commonly used passwords.
–format=NT indicates the format of the password hash.
3. Trying Hybrid Attacks:
Let’s say you have a suspicion that the password consists of a combination of a word from a dictionary and a series of numbers. You can perform a hybrid attack using both a wordlist and incremental mode.
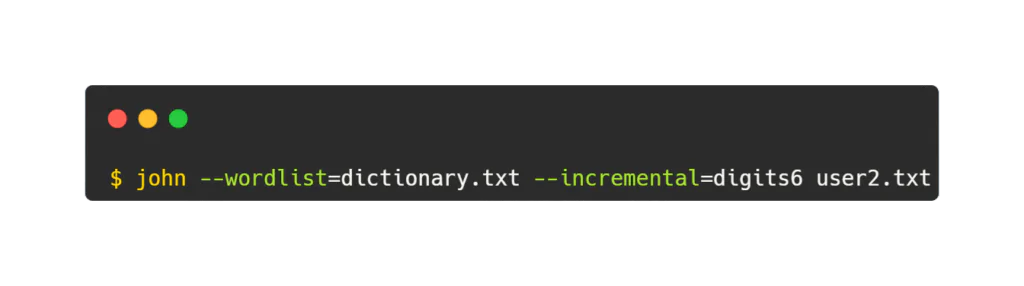
In this command:
–wordlist=dictionary.txt specifies the path to the dictionary file.
–incremental=digits6 tells John to use incremental mode with digits of length up to 6 characters.
4. Decrypting Passwords:
Suppose you have obtained a password hash stored in a MySQL database and you want to decrypt it using John the Ripper.
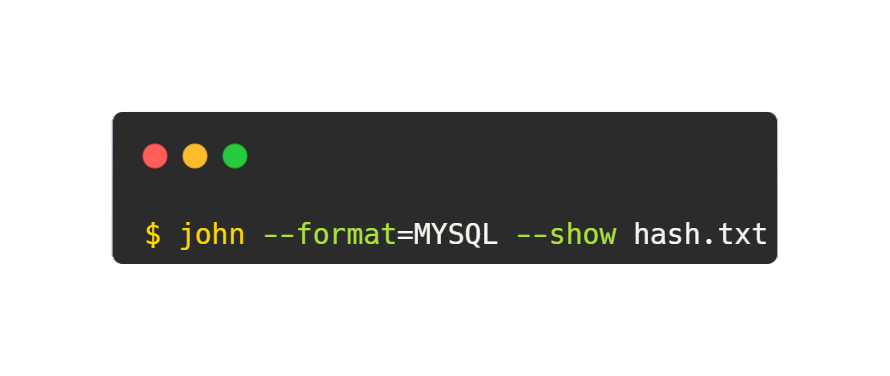
Here:
–format=MYSQL specifies the format of the password hash.
–show instructs John to display the plaintext password if it is successfully decrypted.
These examples showcase the versatility and power of John the Ripper commands in cracking passwords using brute force, wordlists, hybrid attacks, and decrypting password hashes.
Best Practices for Using John
As with any powerful tool, it’s essential to use John responsibly and ethically. Always seek permission before attempting to crack passwords, and never use John for illegal or malicious purposes. Remember, with great power comes great responsibility. Additionally, implementing robust cybersecurity practices is essential for safeguarding your digital assets. For a more in-depth exploration of cybersecurity best practices and additional tips to keep your digital life safe and secure, check out our article “7 CYBERSECURITY TIPS TO KEEP YOUR DIGITAL LIFE SAFE AND SECURE.”
Conclusion
And there you have it – a comprehensive guide to John the Ripper commands and its working. Whether you’re a cybersecurity professional, an aspiring hacker, or just someone curious about how passwords work, John has something to offer. So go ahead, download John, and start cracking those passwords (responsibly, of course)!




Pingback: How to become an ethical hacker in 2024 - HackProofHacks