
Welcome to the world of Bluetooth hacking! In this section, we’ll explore the basics of Bluetooth hacking, where hackers use various techniques to gain unauthorized access to Bluetooth-enabled devices.
Bluetooth hacking involves exploiting vulnerabilities in Bluetooth protocols and implementations to intercept data, control devices remotely, or extract sensitive information. Common Bluetooth hacking techniques include Bluejacking, Bluesnarfing, and Bluebugging, each with its own methods and risks.
Understanding Bluetooth hacking is essential for both users and security professionals to protect against potential threats and ensure the safety of their devices and data.
Table of Contents
Bluetooth Basics
Bluetooth operates in the 2.4 GHz frequency band and utilizes radio waves to establish connections between devices within a short range. This technology enables devices like smartphones, laptops, headphones, and speakers to communicate and share data without the need for cables.
At its core, Bluetooth relies on a master-slave architecture. The master device initiates connections and controls communication, while slave devices respond to commands from the master. This setup allows for efficient data exchange and device synchronization.
Pairing is a fundamental process in Bluetooth, where devices establish a secure connection by exchanging encryption keys. This ensures that only authorized devices can communicate with each other, enhancing security and privacy.
Bluetooth versions have evolved over time, with advancements in speed, range, and power efficiency. The latest versions, such as Bluetooth 5.2 and 5.3, offer enhanced features like increased data transfer rates, longer range, and improved stability.
Basic Linux Bluetooth Tools
Are you ready to dive into the world of Linux Bluetooth tools? Let’s get started with some essential tools that will empower you to manage Bluetooth devices like a pro.
bluetoothctl
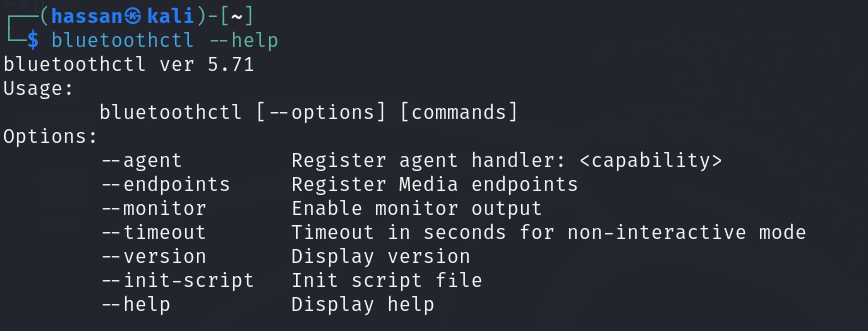
First up, we have Bluetoothctl, a command-line utility that serves as your go-to tool for Bluetooth device management. With Bluetoothctl, you can:
- Scan for Devices: Use the scan on command to scan for nearby Bluetooth devices and view their details.
- Pair Devices: Pairing devices is a breeze with pair <device_address>. Simply enter the Bluetooth address of the device you want to pair with.
- Connect to Devices: Once paired, establish a connection using connect <device_address> to start exchanging data.
hciconfig
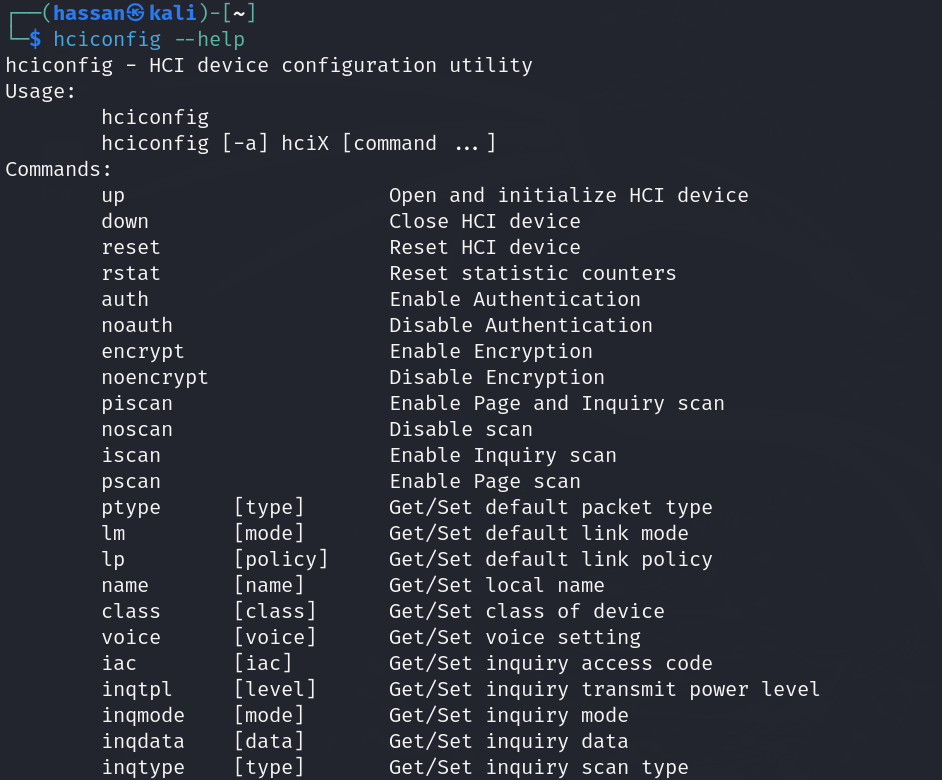
Next on our list is hciconfig, a versatile tool for configuring Bluetooth hardware devices. Here’s what you can do with hciconfig:
- Check Device Status: Use hciconfig without any options to display the status of your Bluetooth hardware, including device name, address, and state.
- Set Bluetooth Mode: Switch between Bluetooth modes such as Discoverable, Connectable, and PSCAN (Page Scan) using hciconfig <device> mode <mode_value>.
hcitool
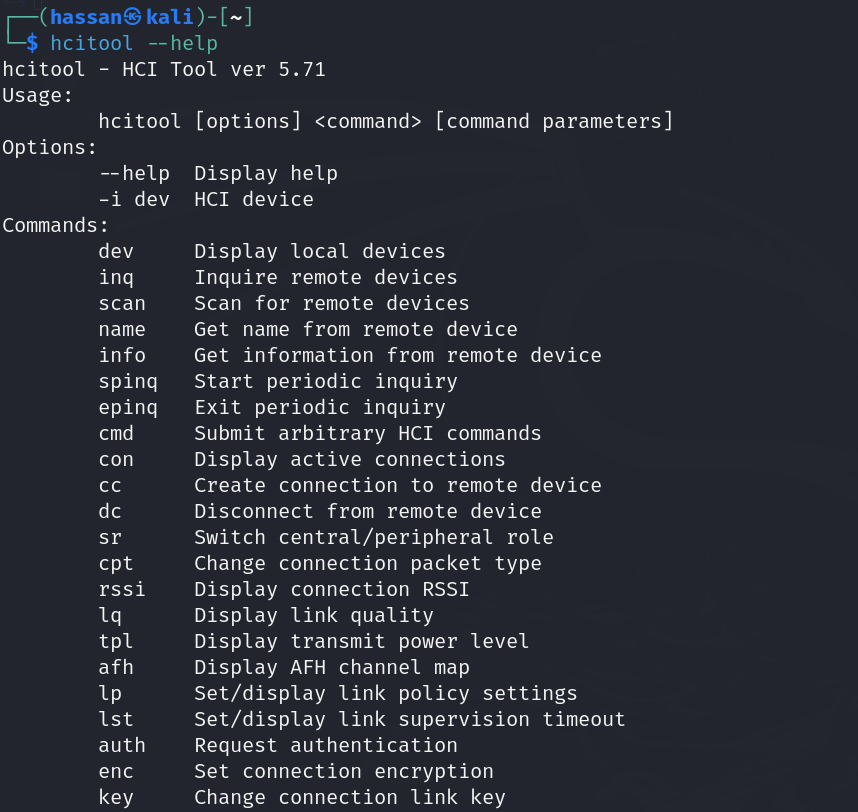
Last but not least, we have hcitool, a handy utility for interacting with Bluetooth devices. Here are some key commands:
- View Device Information: Use hcitool info <device_address> to display detailed information about a specific Bluetooth device.
- Send Commands to Devices: With hcitool cmd <device_address> <command>, you can send custom commands to Bluetooth devices for testing or troubleshooting purposes.
By mastering these basic Linux Bluetooth tools, you’ll be well-equipped to manage Bluetooth devices effectively and troubleshoot connectivity issues with confidence
Bluetooth Protocol Stack
Bluetooth devices aren’t required to utilize every protocol within the Bluetooth stack, similar to how devices don’t always need to use every layer in the TCP/IP stack. The Bluetooth stack is designed to support various communication applications using Bluetooth, including those targeted by hackers for Bluetooth hacking. Typically, an application will only utilize a specific section or layer of this stack, depending on its functionalities and the techniques hackers use for Bluetooth hacking. Here are the layers of the Bluetooth protocols and their associated protocols:
| Layer | Protocols |
| Application Layer | Adopted Protocols: PPP, UDP/TCP/IP, OBEX, WAP, vCard, vCal, IrMC, WAE |
| Logical Link Control and Adaptation Protocol (L2CAP) | LMP, L2CAP, SDP |
| Link Management Protocol (LMP) | RFCOMM, Telephony Control Protocol (TCS Binary, AT-commands) |
| Physical Layer | Host Controller Interface (HCI) |
1. Bluetooth Core Protocols:
At the core of Bluetooth communication are essential protocols that facilitate seamless connections between devices.
- Link Management Protocol (LMP): Handles link establishment, authentication, and encryption, ensuring secure and reliable connections.
- Logical Link Control and Adaptation Protocol (L2CAP): Provides multiplexing capabilities, allowing multiple services to share a single Bluetooth connection.
- Service Discovery Protocol (SDP): Enables devices to discover and utilize available services offered by other Bluetooth devices, enhancing interoperability.
2. Specialized Protocols:
In addition to core protocols, Bluetooth includes specialized protocols tailored for specific communication needs.
- RFCOMM (Cable Replacement Protocol): Emulates serial port communication, making it ideal for legacy applications that rely on serial connections.
- Telephony Control Protocol (TCS Binary, AT-commands): Facilitates telephony-related functionalities, such as call control and AT-command interactions.
3. Adopted Protocols:
Bluetooth adopts widely-used protocols to expand its capabilities and compatibility.
- Point-to-Point Protocol (PPP): Enables direct communication between two devices over Bluetooth.
- UDP/TCP/IP: Supports internet protocol-based communication over Bluetooth, enhancing connectivity with networked devices.
- Object Exchange (OBEX): Facilitates the exchange of objects such as files and media between Bluetooth-enabled devices.
- Wireless Application Environment (WAE): Enables the development of Bluetooth applications for various wireless environments.
4. Host Controller Interface (HCI):
The Bluetooth specification includes a Host Controller Interface (HCI) that serves as a bridge between software applications and Bluetooth hardware components.
- HCI Commands: Allow software applications to interact with the baseband controller, link manager, and hardware registers, providing control and monitoring capabilities.
Understanding the architecture of the Bluetooth protocol stack will help you learn how hackers perform Bluetooth hacking.
Bluetooth Security
If someone wants to hack into any device, they have to firstly learn how the security of those systems works. This is important because it helps them find weak spots and figure out how to break in. In the same way if want to learn Bluetooth Hacking, we By learning about things like security protocols and encryption, hackers can find ways to get into systems and access sensitive information.
Security Mode 1: Non-Secure
Imagine Security Mode 1 as leaving your front door unlocked. In this mode, Bluetooth connections lack encryption or authentication. While suitable for casual tasks, it poses risks when dealing with sensitive data on smartphones.
Security Mode 2: Service-Level Enforced Security
Security Mode 2 adds a layer of protection based on the services you use. Think of it as having different locks for different rooms in your house. Some services require authentication or encryption, enhancing security for specific tasks on your smartphone.
Security Mode 3: Link-Level Enforced Security
Security Mode 3 represents the highest level of Bluetooth security. It secures all communications with authentication and encryption, akin to having secure locks on every entry point of your house. This level is crucial for protecting sensitive data and thwarting hacking attempts on smartphones.
Security Mode 4: Service-Level Authorization
Security Mode 4 focuses on controlling access to specific services. Devices need authorization to use certain services, similar to having a guest list for a private event. This added layer of security prevents unauthorized access to critical functions on smartphones.
Bluetooth Hacking Tools in Kali Linux
In earlier versions, Kali used to come pre-installed with multiple Bluetooth hacking tools. However, in Kali 2020, only one tool called spooftooth remains included by default. But this doesn’t mean that other tools are not available. Many additional tools can be found in the Kali repository and on github.com. We plan to incorporate several of these tools in our upcoming tutorials.
1. Bluelog
Bluelog is a Bluetooth site survey tool that scans the area to discover Bluetooth-enabled devices. It logs the discovered devices into a file.
- Install:
sudo apt-get install bluelog - Usage: Launch Bluelog and initiate a scan to discover Bluetooth devices in the area. The discovered devices will be logged to a file.
2. Bluemaho
Bluemaho is a GUI-based suite of tools designed for testing Bluetooth device security. It offers a range of functionalities for assessing vulnerabilities and conducting security tests on Bluetooth devices.
- Install:
sudo apt-get install bluemaho - Usage: Launch Bluemaho’s graphical interface to access various tools and features for Bluetooth security testing. Follow the tool’s prompts and options to perform security assessments on Bluetooth devices.
3. Blueranger
Blueranger is a Python script that utilizes i2cap pings to locate Bluetooth devices and estimate their approximate distances.
- Install: Blueranger is a Python script that can be downloaded and executed directly from the command line.
- Usage: Execute the Blueranger script in a terminal to utilize its functionality for locating Bluetooth devices and estimating their approximate distances.
4. Btscanner
Btscanner is a GUI-based tool that scans for discoverable Bluetooth devices within range. It provides a user-friendly interface for identifying nearby Bluetooth devices and gathering information about their capabilities.
- Install:
sudo apt-get install btscanner - Usage: Launch Btscanner and initiate a scan to detect discoverable Bluetooth devices. Explore the scan results to view device details and assess Bluetooth device presence.
5. Redfang
Redfang is a specialized tool designed to find hidden Bluetooth devices that may not be readily discoverable. It employs advanced techniques to identify and locate Bluetooth devices that may be intentionally concealed or not visible through standard scans.
- Install:
sudo apt-get install redfang - Usage: Launch Redfang and configure the tool to search for hidden Bluetooth devices. Analyze the results to identify hidden devices and assess their presence in the environment.
6. Spooftooph
Spooftooph is a Bluetooth spoofing tool that allows users to manipulate Bluetooth device identities and characteristics. It can spoof device information such as device name, class, and address, enabling various spoofing and manipulation scenarios.
- Install:
sudo apt-get install spooftooph - Usage: Launch Spooftooph and follow the prompts to spoof Bluetooth device information as desired.
Using Spooftooph for Bluetooth Hacking
Step 1: Installing Spooftooph
Before we begin our journey in Bluetooth hacking, ensure that you have Kali Linux installed on your system. To install Spooftooph, open a terminal and execute the following command:
sudo apt-get install spooftoophFollow the prompts to complete the installation process.
Step 2: Understanding Spooftooph Commands
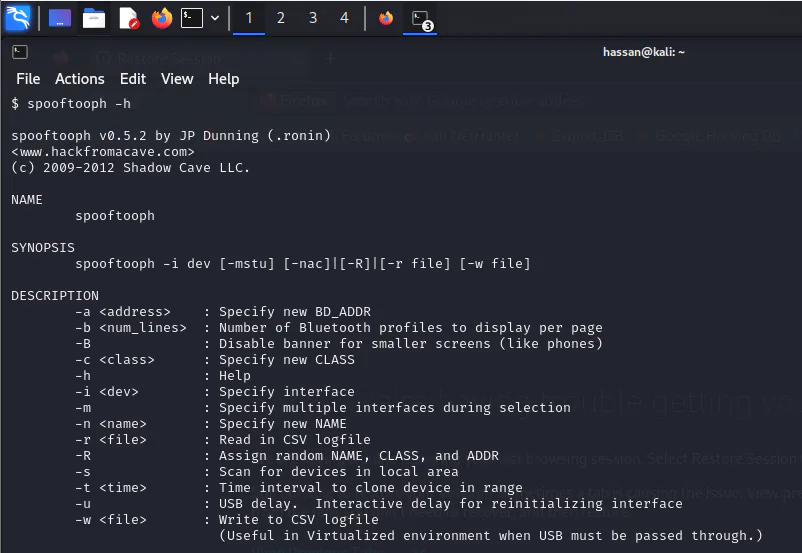
Spooftooph offers a range of commands and options for Bluetooth spoofing. Here are some commands to familiarize yourself with:
- -i, –interface: Specifies the Bluetooth interface to use for spoofing.
- -a, –address: Sets the spoofed Bluetooth device address.
- -n, –name: Sets the spoofed Bluetooth device name.
- -t, –timeout: Specifies the timeout duration for scans and operations.
- -r, –random: Enables randomization of device address and name.
Step 3: Spoofing Bluetooth Device Identity
To spoof a Bluetooth device’s identity, follow these steps:
- Open a terminal and launch Spooftooph with the following command:
sudo spooftooph -i <interface> -a <spoofed_address> -n <spoofed_name>Replace <interface> with your Bluetooth interface name, <spoofed_address> with the desired spoofed device address, and <spoofed_name> with the spoofed device name.
- Spooftooph will start spoofing the Bluetooth device identity based on the provided parameters.
Step 4: Verifying Spoofed Identity
After spoofing the Bluetooth device identity, you can verify the spoofed details by scanning for Bluetooth devices in the vicinity. Use the following command to perform a Bluetooth device scan:
hcitool scanThis command will display a list of nearby Bluetooth devices along with their addresses and names. Look for the spoofed device name and address to confirm the spoofing operation.
Step 5: Additional Spooftooph Options
Spooftooph offers additional options for advanced Bluetooth spoofing and manipulation. Explore the tool’s documentation and experiment with options such as randomization (-r, –random), timeout settings (-t, –timeout), and more to enhance your spoofing capabilities.
How To Prevent Bluetooth Hacking?
When it comes to protecting your devices from Bluetooth hacking, implementing preventive measures is key. Let’s explore some practical steps you can take to safeguard against Bluetooth hacking attempts, presented in a tutorial-style format for easy understanding.
- Keep Bluetooth Turned Off When Not in Use
The simplest and most effective way to prevent Bluetooth hacking is to keep Bluetooth turned off when you’re not actively using it. This reduces your device’s visibility to potential hackers and minimizes the risk of unauthorized connections.
- Use Strong, Unique PINs and Passwords
When pairing Bluetooth devices, always use strong and unique Personal Identification Numbers (PINs) or passwords. Avoid using default or easily guessable PINs, as they can be exploited by hackers. Choose complex combinations for added security.
- Update Firmware and Software Regularly
Ensure that your device’s firmware and software are up to date with the latest security patches and updates. Manufacturers often release patches to fix known vulnerabilities, so keeping your devices updated is essential to prevent exploitation by hackers.
- Be Cautious of Unknown Devices
Avoid connecting to unknown or untrusted Bluetooth devices, especially in public places. Hackers may set up rogue devices to lure unsuspecting users into connecting, leading to potential security breaches. Verify the identity and trustworthiness of devices before pairing.
- Enable Bluetooth Security Features
Most modern devices come with built-in Bluetooth security features such as authentication and encryption. Enable these features to add an extra layer of protection against Bluetooth hacking attempts. Authentication ensures that only authorized devices can connect, while encryption secures data during transmission.
Conclusion
In wrapping up, let’s emphasize the critical importance of protecting ourselves against Bluetooth hacking. By implementing the proactive measures we’ve discussed i.e., keeping Bluetooth off when not needed, using strong passwords, updating our devices regularly, being cautious of unknown connections, and enabling security features, we can prevent Bluetooth hacking.
Remember, staying informed about evolving security risks and adopting a security-first mindset are crucial in today’s digital landscape. While Bluetooth offers convenience, it also comes with vulnerabilities that require our attention.
As technology advances, so do the tactics of hackers. This means staying proactive and informed is our best defense. By following the steps outlined here and staying proactive about Bluetooth security, we can enjoy seamless connectivity while minimizing the risks associated with Bluetooth hacking.
In conclusion, let’s prioritize awareness, education, and proactive security practices to safeguard against Bluetooth hacking and ensure a safer digital experience for all of us.
FAQS
- How can I tell if my device has been hacked via Bluetooth?
Signs of Bluetooth hacking include unexpected device behavior, unauthorized access to files or apps, sudden battery drain, and unusual network activity. Regularly check your device’s Bluetooth connections and settings for any anomalies. - What are the types of attacks on Bluetooth devices?
Bluetooth devices can be targeted with various attacks, including Bluejacking (sending unsolicited messages), Bluesnarfing (stealing data), Bluebugging (taking control of a device), and Man-in-the-Middle (intercepting and altering data). - Which security is used in Bluetooth?
Bluetooth utilizes various security measures, including authentication, encryption (such as AES), and pairing protocols (like Secure Simple Pairing) to protect against Bluetooth hacking attempts and unauthorized access. - Which of the following types of Bluetooth hacking is a denial-of-service attack?
A denial-of-service (DoS) attack in Bluetooth hacking aims to disrupt or disable Bluetooth connections, rendering devices unable to communicate. It can lead to connectivity issues and device malfunctions. - Does VPN protect Bluetooth?
While VPNs (Virtual Private Networks) encrypt internet traffic, they don’t directly protect Bluetooth connections. However, using a VPN can enhance overall network security and privacy, complementing Bluetooth security measures. - Is Bluetooth 5.0 secure?
Bluetooth 5.0 introduced enhanced security features like increased data transfer speeds, improved encryption algorithms, and better compatibility with IoT devices. While it improves security, users should still follow best practices to prevent Bluetooth hacking. - How to stop Bluetooth hacking?
To prevent Bluetooth hacking, keep Bluetooth turned off when not in use, use strong passwords and encryption, update device firmware regularly, avoid connecting to unknown devices, and enable security features like authentication. - What are the weaknesses of Bluetooth?
Bluetooth vulnerabilities include potential for eavesdropping, man-in-the-middle attacks, weak or default passwords, outdated encryption protocols, and susceptibility to Bluetooth sniffing tools used by hackers. Regular security updates and best practices help mitigate these weaknesses.




