
Introduction
Hey everyone! Welcome to the fifth tutorial of our Ethical Hacking Series. This tutorial is on Networking Essentials. We will be understanding IPs, ports, and protocols. If you were looking for an ethical hacking series then this place is for you. After learning about how to set up a Hacking Lab, How to use Linux, the First phase of hacking, and the Scanning Tool. Now, you need to learn the basics of IP addresses, ports, and protocols because it is essential for you as an Ethical Hacker.
Table of Contents
Why Are IPs, Ports, and Protocols Important?
Your computer is just like a house and an IP address is like the address of your house, letting other devices know where to find you on the internet. Ports are like the doors and windows of your house, each serving a different purpose and allowing specific types of traffic to come in and go out. Protocols are like the rules of the road, making sure data travels safely and efficiently from one place to another.
What Will We Cover?
In this article, we’ll break down these concepts into simple, easy-to-understand sections. First, we’ll dive into IP addresses. You’ll learn what they are, how they work, and the difference between IPv4 and IPv6. We’ll also discuss public versus private IP addresses and show you how to find your own IP address.
Next, we’ll talk about ports. You’ll understand what a port is and how it functions in network communication. We’ll cover some commonly used ports and their purposes, explain the difference between TCP and UDP ports, and show you how to check which ports are open on your system.
Then, we’ll explore protocols. These are the rules that govern how data is transmitted over a network. We’ll discuss some of the most common protocols, like HTTP, HTTPS, FTP, and SSH, and explain how they ensure secure and efficient communication. We’ll also touch on the OSI model and TCP/IP model to give you a better understanding of how protocols work at different layers of networking.
Throughout this blog, I’ll provide practical examples and real-world scenarios to help you apply what you’ve learned. By the end, you’ll have a solid understanding of IPs, ports, and protocols, and you’ll be well on your way to mastering the basics of networking and cybersecurity.
Let’s get started and dive into the world of IPs, ports, and protocols together!
Basics of IP Addresses
Now, let’s dive into the basics of IP addresses. Understanding IP addresses is crucial for anyone working in networking or cybersecurity. Understanding IP addresses is essential for anyone looking to master networking.
What is an IP Address?
An IP address is a unique identifier for a device on a network. Think of it like the address of your house. Just as the postal service needs your address to deliver mail, networks use IP addresses to deliver data to the right devices. IP addresses serve as unique identifiers in the world of networking, ensuring data reaches the correct destination.
Types of IP Addresses
There are two main types of IP addresses: IPv4 and IPv6.
IPv4:
- IPv4 addresses look like this:
192.168.1.1. - They are 32-bit numbers, allowing for about 4.3 billion unique addresses.
- IPv4 is the most common type of IP address.
IPv6:
- IPv6 addresses look like this:
2001:0db8:85a3:0000:0000:8a2e:0370:7334. - They are 128-bit numbers, allowing for a nearly infinite number of unique addresses.
- IPv6 was created to solve the shortage of IPv4 addresses.
Here is a chart to help visualize the difference between IPv4 and IPv6:

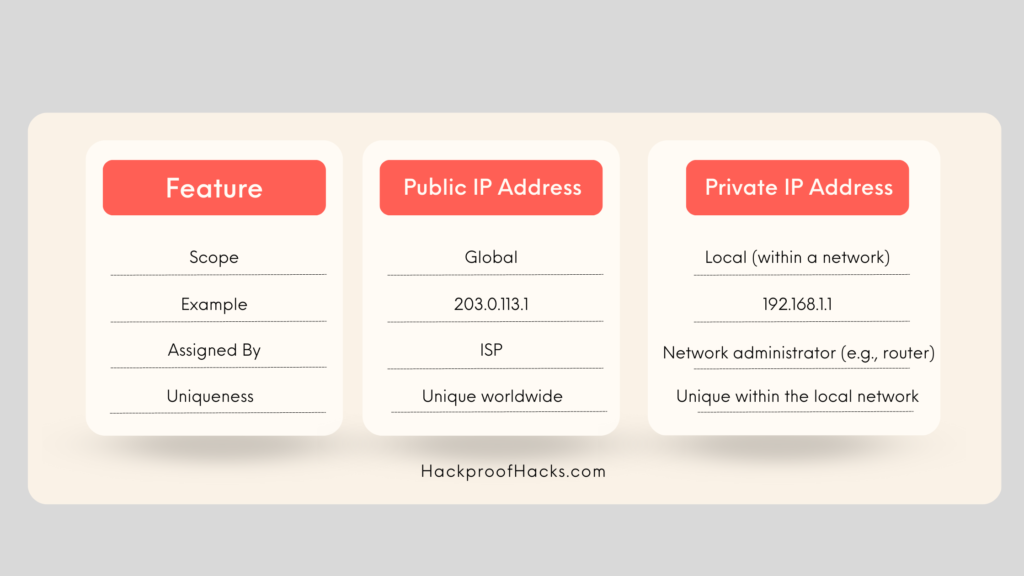
Public vs. Private IP Addresses
Public IP Addresses:
- These are unique across the entire internet.
- Assigned by your Internet Service Provider (ISP).
- Used to identify your device globally.
Private IP Addresses:
- These are used within private networks (like your home or office network).
- Not unique globally; several networks can use the same private IP addresses.
- Common private IP ranges are:
10.0.0.0 to 10.255.255.255172.16.0.0 to 172.31.255.255192.168.0.0 to 192.168.255.255
Here is a chart showing the difference between public and private IP addresses:
How to Find Your IP Address
Finding your IP address is easy. Here’s how you can do it:
For Windows:
- Open Command Prompt.
- Type
ipconfigand pressEnter. - Look for “IPv4 Address” under your network connection.
For macOS:
- Open Terminal.
- Type
ifconfigand pressEnter. - Look for “inet” under your active network connection.
For Linux:
- Open Terminal.
- Type
ip aand pressEnter. - Look for “inet” under your network connection.
Why IP Addresses Matter
IP addresses are essential for communication between devices on a network. Without IP addresses, it would be impossible to send or receive data correctly. They help ensure that data reaches the right destination and comes from the correct source.
Understanding Ports
Now that we’ve covered IP addresses, let’s dive into ports. Understanding ports is key to managing network traffic and ensuring secure communication. Ports are crucial in networking as they help direct traffic to the appropriate services on a device.
What is a Port?
Think of your computer as a house. If the IP address is the house’s address, ports are like the doors and windows. In networking, different ports are used for different types of communication, such as web traffic or email. Each port serves a different purpose, allowing specific types of network traffic to enter and exit.
A port is a numerical identifier in networking, used by protocols to manage different types of connections.
How Do Ports Work?
Ports work with IP addresses to route data to the right applications. When data arrives at your IP address, the port number directs it to the correct application.
For example:
- Port 80 is used for HTTP web traffic.
- Port 443 is used for HTTPS secure web traffic.
Here’s a simple chart to help you visualize:
Types of Ports
Ports are categorized into three ranges:
- Well-Known Ports (0-1023): It is used by systems or well-known services.
- Registered Ports (1024-49151): It is used by users or registered services.
- Dynamic/Private Ports (49152-65535): Used by client applications or ephemeral ports.
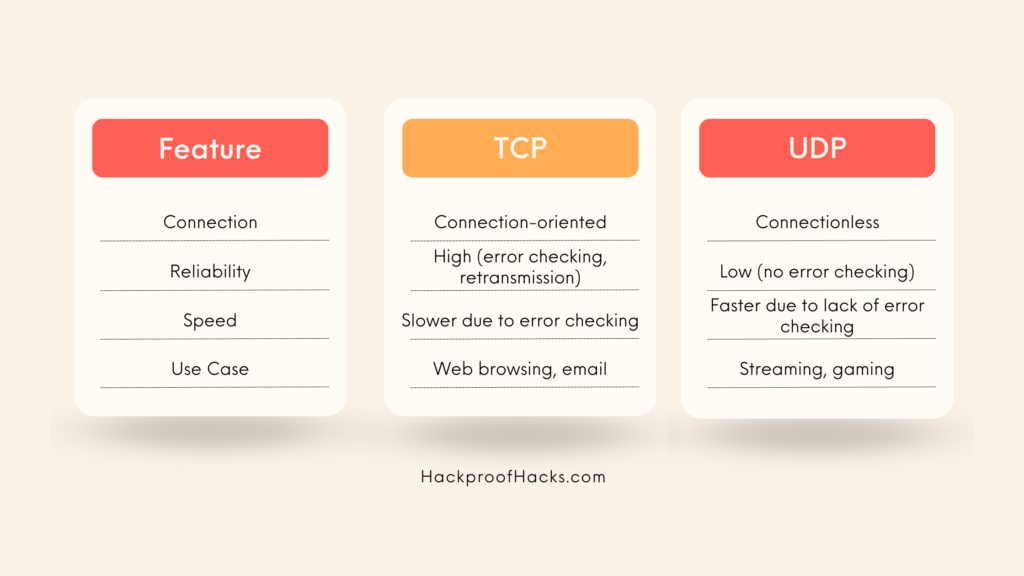
TCP vs. UDP Ports
There are two main types of ports: TCP and UDP.
- TCP (Transmission Control Protocol):
- Connection-oriented.
- Ensures data is received accurately and in order.
- Example: Web browsing (HTTP), email (SMTP).
- UDP (User Datagram Protocol):
- Connectionless.
- Faster but less reliable.
- Example: Streaming (video, audio), online gaming.
Here’s a comparison chart:
Commonly Used Ports
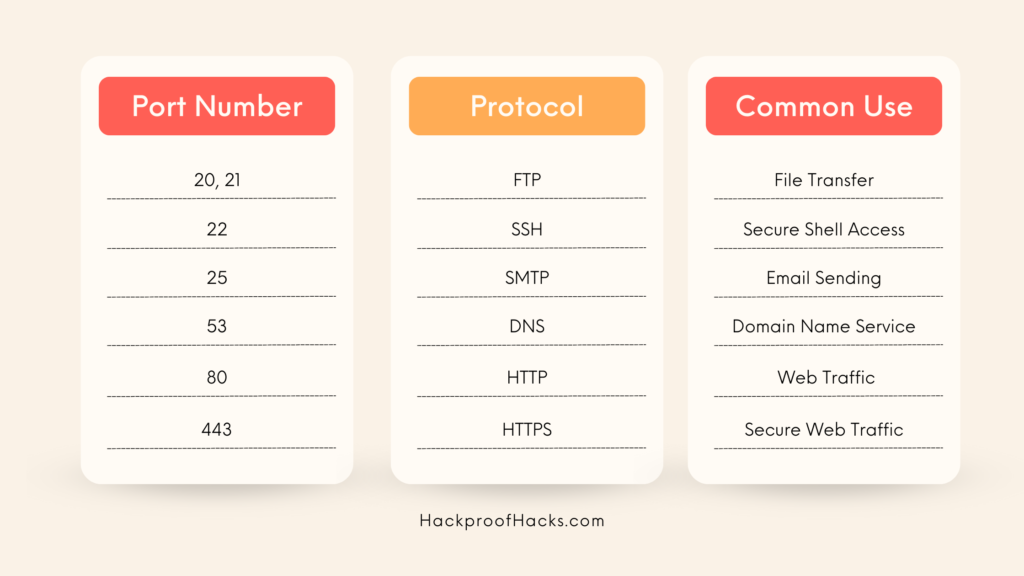
Some ports are commonly used and frequently targeted in cybersecurity:
- Port 21 (FTP): File Transfer Protocol, used for transferring files.
- Port 22 (SSH): Secure Shell, used for secure remote access.
- Port 25 (SMTP): Simple Mail Transfer Protocol, used for sending emails.
- Port 53 (DNS): Domain Name System, used for resolving domain names to IP addresses.
- Port 80 (HTTP): Used for web traffic.
- Port 443 (HTTPS): Used for secure web traffic.
How to Check Open Ports
Checking open ports on your system is essential for security and troubleshooting:
For Windows:
- Open Command Prompt.
- Type
netstat -anand pressEnter. - Look for entries with “LISTENING” status.
For macOS and Linux:
- Open Terminal.
- Type
netstat -tulnand pressEnter. - Look for entries with “LISTEN” status.
Why Ports Matter
Understanding ports helps you manage and secure network traffic. Knowing which ports are open and what they are used for can prevent unauthorized access and improve your network’s performance.
By mastering ports, you’re enhancing your networking and cybersecurity skills. Next, we’ll explore protocols to complete the picture of how data travels across networks. Let’s keep learning!
Protocols Explained
Now that we’ve covered IP addresses and ports, let’s dive into protocols. Protocols are essential for communication between devices on a network. They define the rules for data exchange, ensuring that devices can understand each other. Protocols form the rules of networking, dictating how data is transmitted and received across networks.
What is a Protocol?
A protocol is a set of rules and standards that allows devices to communicate over a network. Think of it like a language. Just as people need a common language to understand each other, devices need protocols to communicate.
Types of Protocols
There are several types of protocols, each serving different purposes. Let’s explore some of the most common ones:
- TCP/IP (Transmission Control Protocol/Internet Protocol):
- TCP: Ensures data is delivered accurately and in the correct order.
- IP: Routes data to the correct destination.
- Used for most internet communications.
- HTTP/HTTPS (HyperText Transfer Protocol/Secure):
- HTTP: Used for transmitting web pages.
- HTTPS: Secure version of HTTP, encrypts data for secure communication.
- Used for browsing websites.
- FTP (File Transfer Protocol):
- Used for transferring files between computers.
- Commonly used for uploading files to a server.
- SMTP/IMAP/POP3 (Email Protocols):
- SMTP (Simple Mail Transfer Protocol): Used for sending emails.
- IMAP (Internet Message Access Protocol): Used for receiving emails, keeps emails on the server.
- POP3 (Post Office Protocol): Used for receiving emails, downloads emails to your device.
How Protocols Work
Protocols work by breaking data into small packets, sending them over the network, and reassembling them at the destination. Each protocol has its own way of handling these packets. Networking relies on protocols like TCP and UDP to ensure data is delivered accurately and efficiently.
Example: Web Browsing with HTTP/HTTPS
- Client Request: Your browser sends an HTTP/HTTPS request to a web server.
- Server Response: The web server processes the request and sends back the web page.
- Data Transfer: The data is transferred in small packets.
- Display: Your browser reassembles the packets and displays the web page.
Layers of Protocols
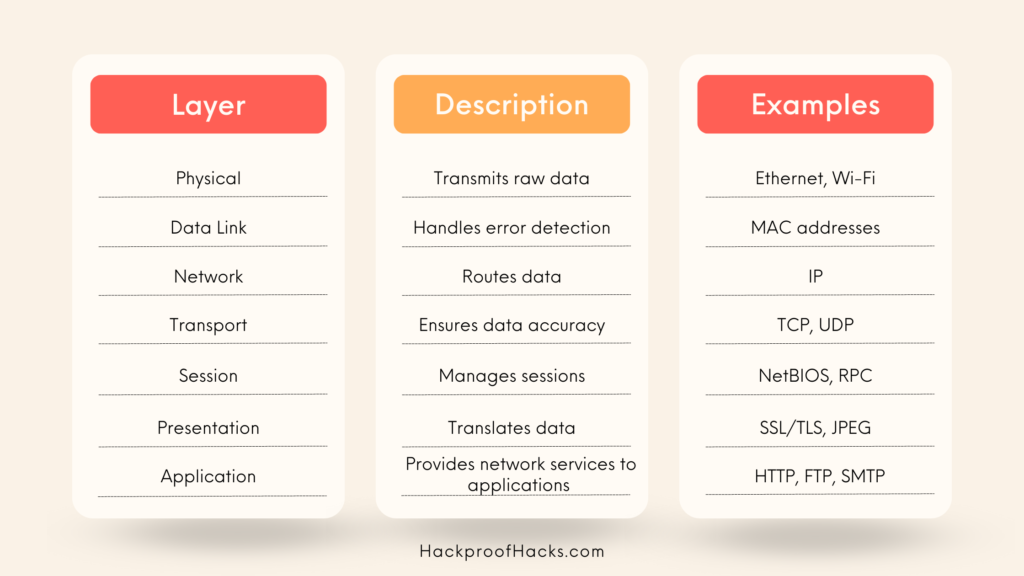
Protocols are often organized into layers, each responsible for different aspects of communication. The most common model is the OSI (Open Systems Interconnection) model, which has seven layers:
- Physical Layer: Transmits raw data over physical media (cables, radio waves).
- Data Link Layer: Handles error detection and correction.
- Network Layer: Routes data to the correct destination (IP protocol).
- Transport Layer: Ensures data is delivered accurately (TCP protocol).
- Session Layer: Manages sessions between applications.
- Presentation Layer: Translates data between the network and applications.
- Application Layer: Provides network services to applications (HTTP, FTP).
Here’s a chart to help you understand the OSI model:
Why Protocols Matter
Protocols are the backbone of network communication. They ensure that data is sent and received accurately, securely, and efficiently. Understanding protocols helps you troubleshoot network issues, secure your communications, and optimize network performance.
IP Address Classes and Subnetting
Let’s dive into the topic of IP address classes and subnetting. This is crucial for understanding how networks are organized and how to manage them effectively.
IP Address Classes
IP addresses are divided into classes to simplify the allocation of addresses. There are five main classes, but we’ll focus on the most common three: A, B, and C.
- Class A:
- Range: 1.0.0.0 to 126.0.0.0
- Subnet Mask: 255.0.0.0
- Usage: Large networks, like ISPs or large organizations.
- Structure: 1 octet for network, 3 octets for hosts.
- Class B:
- Range: 128.0.0.0 to 191.255.0.0
- Subnet Mask: 255.255.0.0
- Usage: Medium-sized networks, like universities or mid-sized companies.
- Structure: 2 octets for network, 2 octets for hosts.
- Class C:
- Range: 192.0.0.0 to 223.255.255.0
- Subnet Mask: 255.255.255.0
- Usage: Small networks, like small businesses or home networks.
- Structure: 3 octets for network, 1 octet for hosts.
Special IP Ranges
There are some special IP ranges you should know about:
- Private IPs:
- Used within a private network, not routable on the internet.
- Class A: 10.0.0.0 – 10.255.255.255
- Class B: 172.16.0.0 – 172.31.255.255
- Class C: 192.168.0.0 – 192.168.255.255
- Loopback IP:
- Used for testing and communication within the same machine.
- Range: 127.0.0.1
What is Subnetting?
Subnetting divides a large network into smaller, more manageable sub-networks or subnets. This improves network performance and security. Subnetting is a vital skill in networking that helps manage large IP address spaces efficiently.
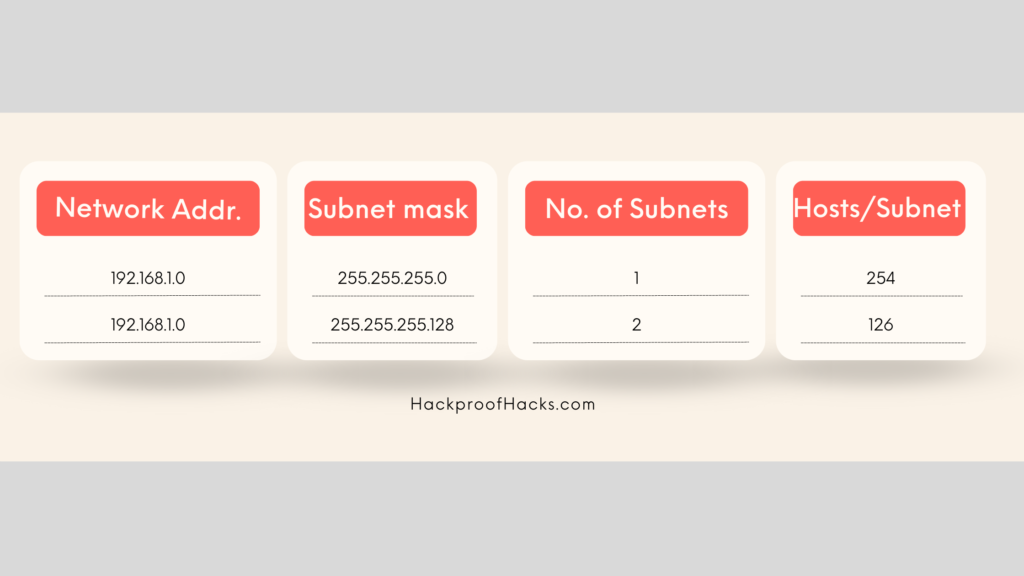
Imagine you have a Class C network with the IP address 192.168.1.0 and you need to divide it into two smaller networks. You can do this by borrowing bits from the host portion of the address.
Subnet Masks
A subnet mask determines which portion of an IP address is the network and which part is the host.
- Default Subnet Mask for Class C: 255.255.255.0
- Subnet Mask for Two Subnets: 255.255.255.128
Here’s a visual representation:
Calculating Subnets
To create subnets, you need to understand binary math. Here’s a simplified process:
- Convert the subnet mask to binary.
- Identify the network and host portions.
- Subnets can be created by borrowing bits from the host section.
Example:
- Original Subnet Mask (Class C):
255.255.255.0(binary: 11111111.11111111.11111111.00000000) - New Subnet Mask (for 2 subnets):
255.255.255.128(binary: 11111111.11111111.11111111.10000000)
By borrowing one bit, you create two subnets with 126 hosts each.
Practical Example
Let’s say you have a company network with the IP address 192.168.1.0/24 (Class C). You want to create four subnets:
- Convert the subnet mask to binary:
255.255.255.0(binary: 11111111.11111111.11111111.00000000) - Borrow two bits to create four subnets: New mask:
255.255.255.192(binary: 11111111.11111111.11111111.11000000)
This gives you:
- Subnet 1: 192.168.1.0/26
- Subnet 2: 192.168.1.64/26
- Subnet 3: 192.168.1.128/26
- Subnet 4: 192.168.1.192/26
Each subnet has 62 hosts (2^6 – 2).
Why Subnetting Matters
Subnetting allows efficient IP address management, improved security, and optimized network performance. It’s crucial for network administrators to master this skill.
Network Address Translation (NAT)
Today, we’re going to explore Network Address Translation, or NAT. This is a key concept in networking that helps manage IP addresses and improve security.
What is NAT?
Network Address Translation (NAT) is a technique for modifying network address information in IP packet headers. It is a key concept in networking that allows multiple devices to share a single public IP address. It allows numerous devices on a local network to share the same public IP address. This is particularly useful for conserving the number of public IP addresses needed.
How NAT Works
Imagine you have a home network with several devices connected to the internet. Each device has a private IP address, but they all share one public IP address provided by your Internet Service Provider (ISP). NAT translates the private IP addresses to the public IP address when the devices communicate with the internet.
Types of NAT
There are various types of NAT, each performing a particular function:
- Static NAT:
- Maps one private IP address to a single public IP address.
- Useful for hosting servers that need to be accessible from the internet.
- Example: A web server with a private IP address (192.168.1.10) is always translated to a specific public IP address (203.0.113.2).
- Dynamic NAT:
- Maps private IP addresses to a set of public IP addresses.
- The translation can change dynamically, hence the name.
- Example: Any device on the network can be assigned any available public IP from a pool.
- Port Address Translation (PAT) or Overloading:
- Maps multiple private IP addresses to a single public IP address but uses different ports.
- Most common type of NAT used in home networks.
- Example: Multiple devices (192.168.1.2, 192.168.1.3) use the same public IP (203.0.113.1) but different port numbers for translation.
NAT Table
The router maintains a NAT table that keeps track of the translations. Here’s a simplified view of a NAT table:
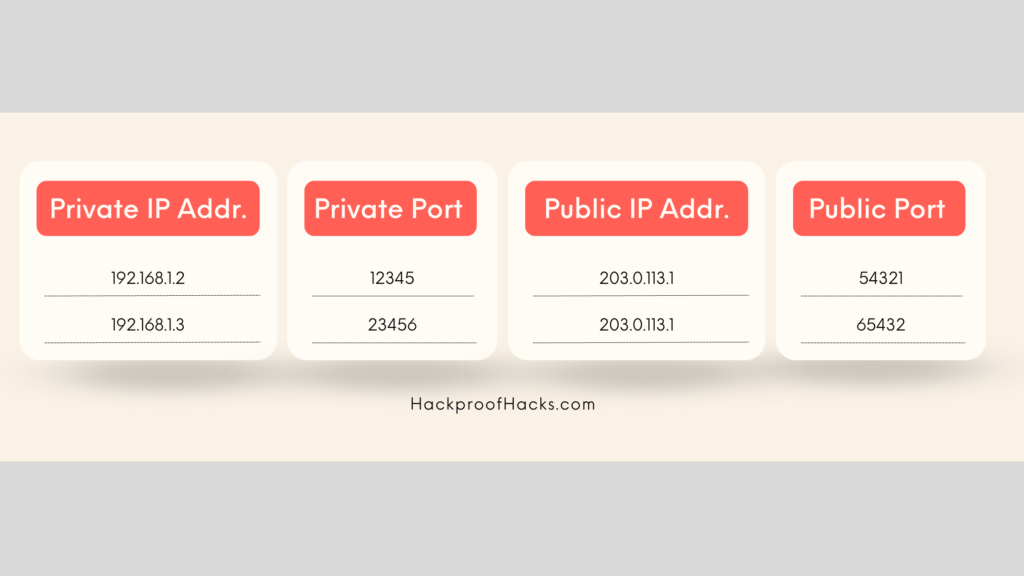
When a device on the local network sends a request to the internet, the router changes the source IP address to the public IP and assigns a unique port number. When the response comes back, the router uses the NAT table to route the data back to the correct device.
Benefits of NAT
- IP Address Conservation:
- NAT helps conserve the number of public IP addresses needed. This is especially important given the limited availability of IPv4 addresses.
- Security:
- By hiding the internal IP addresses, NAT provides a layer of security. It makes it harder for external attackers to target individual devices on the local network.
- Ease of Network Management:
- NAT simplifies the management of IP addresses within a local network. Network administrators can use private IP addresses without worrying about conflicts with public IP addresses.
Drawbacks of NAT
- Performance:
- NAT can introduce slight delays as the router processes the translations.
- Complications with Certain Protocols:
- Some protocols and applications might have issues with NAT. For example, peer-to-peer applications and VoIP services might require special configuration.
- End-to-End Connectivity:
- NAT can complicate end-to-end connectivity, making direct connections between devices across different networks more challenging.
Practical Example
Let’s consider a practical example:
You have three devices in your home network:
- Device 1:
192.168.1.2 - Device 2:
192.168.1.3 - Device 3:
192.168.1.4
Your router has a public IP address: 203.0.113.1
When Device 1 wants to access a website, the router:
- Translates the private IP (
192.168.1.2) to the public IP (203.0.113.1). - Assigns a unique port number for this session.
- Records the translation in the NAT table.
- Sends the request to the internet.
When the response comes back, the router uses the NAT table to route the data back to Device 1.
Understanding NAT is essential for managing modern networks. It helps conserve IP addresses, provides security, and simplifies network management. Networking would be far less efficient without NAT, as it helps conserve IP addresses and enhance security.
Keep practicing and exploring different types of NAT setups to deepen your understanding and enhance your network management skills.
Understanding Firewalls and Ports
Today, we’re diving into the world of firewalls and ports. These are essential concepts for anyone interested in networking and cybersecurity. Let’s break it down step-by-step.
What is a Firewall?
Firewalls play a critical role in networking by controlling access to and from a network based on predefined rules. A firewall is a security device that monitors and regulates incoming and outgoing network traffic based on established security rules. It works as a barrier between a trusted internal network and unreliable external networks like the internet.
Think of a firewall as a gatekeeper. It decides what traffic can enter and leave your network. Firewalls can be hardware-based, software-based, or a combination of both. In networking, configuring firewall rules correctly is essential to protect against unauthorized access.
Types of Firewalls
- Packet-Filtering Firewalls:
- Examines every packet that enters or leaves the network.
- Accepts or rejects packets according to user-defined rules.
- Simple and fast, but can be limited in complexity.
- Stateful Inspection Firewalls:
- Tracks the state of active connections.
- Determines which network packets to allow based on the state of the connection.
- More secure than packet-filtering firewalls.
- Proxy Firewalls:
- intercepts all messages that enter and exit the network.
- Hides the true network addresses.
- Can inspect higher-layer protocols.
- Next-Generation Firewalls (NGFW):
- Includes traditional firewall capabilities plus additional features like intrusion prevention systems (IPS).
- Can inspect applications and use deep packet inspection.
What are Ports?
Ports are virtual endpoints used for network communication. They allow a single IP address to support multiple networking applications. Each port has been identified by a number that ranges from 0 to 65535.
Types of Ports
- Well-Known Ports (0-1023):
- Reserved for system or well-known services.
- Examples: HTTP (80), HTTPS (443), FTP (21).
- Registered Ports (1024-49151):
- Assigned to user processes or applications.
- Examples: Microsoft SQL Server (1433), MySQL (3306).
- Dynamic or Private Ports (49152-65535):
- Used dynamically by applications.
- Not assigned to any specific service.
How Firewalls Use Ports
Firewalls use ports to control traffic. They can block or allow traffic based on port numbers. For example, if you want to block web traffic, you can configure the firewall to block port 80 (HTTP) and port 443 (HTTPS).
Setting Up Firewall Rules
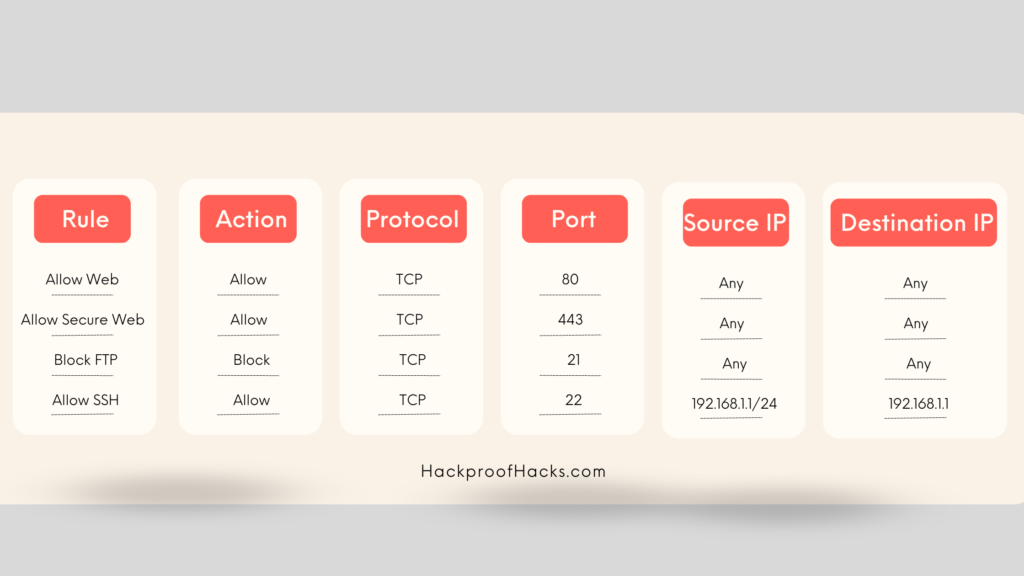
Let’s look at how to set up basic firewall rules:
- Allowing Web Traffic:
- Allow HTTP and HTTPS traffic on ports 80 and 443, respectively.
- Blocking FTP Traffic:
- Block traffic on port 21 (FTP).
- Custom Rules:
- Allow or block specific IP addresses.
- Restrict traffic based on time of day.
Here’s a sample chart of firewall rules:
Practical Example
Imagine you want to allow your internal network to access a web server and block FTP traffic. Here’s how to set it up:
- Allow Web Traffic:
- Configure the firewall to allow TCP traffic on port 80 and 443.
- Block FTP Traffic:
- Configure the firewall to block TCP traffic on port 21.
Conclusion
Understanding firewalls and ports is crucial for network security and management. Firewalls act as gatekeepers, while ports enable multiple applications to use the same IP address. By setting up proper firewall rules, you can protect your network and ensure smooth communication.
Keep experimenting with different firewall configurations and port settings to master network security. Remember, practice makes perfect!
Tools for Managing and Monitoring IPs and Ports
In this section, we’ll explore some essential tools for managing and monitoring IPs and ports. These tools help you keep track of your network, ensuring everything runs smoothly and securely. Effective networking requires tools that can manage and monitor IP addresses and ports. Let’s dive in.
What Are Network Management Tools?
Network management tools are software applications that help you monitor and manage network performance. They allow you to see what’s happening in your network, identify issues, and ensure optimal performance.
Why Are They Important?
Managing IPs and ports manually can be overwhelming, especially in large networks. These tools automate many tasks, providing real-time insights and making network management more efficient.
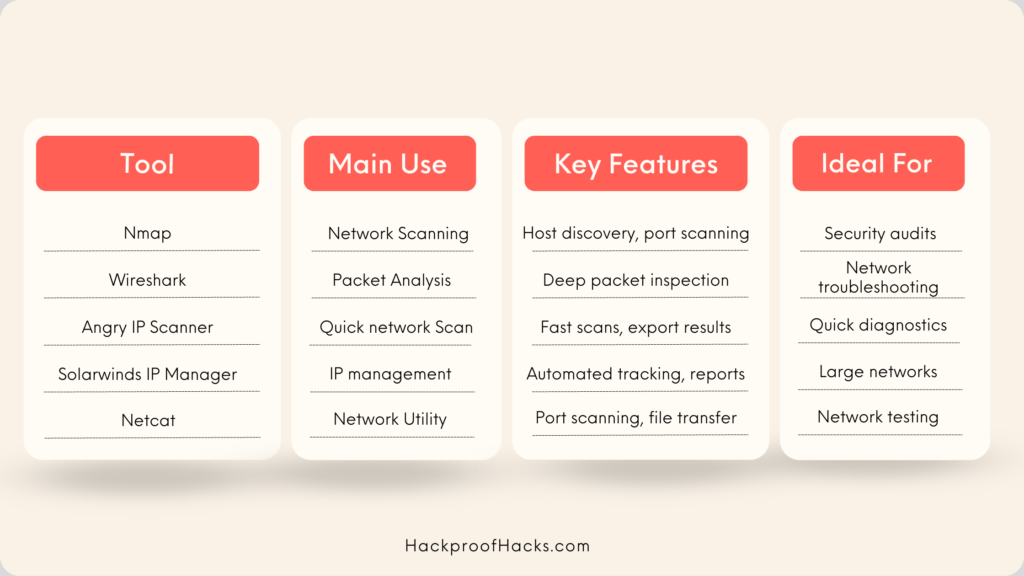
Popular Tools for Managing IPs and Ports
- Nmap
- Description: Nmap (Network Mapper) is a free, open-source tool for network discovery and security auditing.
- Features: Scans networks, discovers hosts and services, maps network topology.
- Usage: Ideal for network administrators to perform security scans and detect vulnerabilities.
- Wireshark
- Description: Wireshark is a network protocol analyzer that captures and interacts with data traffic.
- Features: Analyzes packet data, inspects network traffic, diagnoses network issues.
- Usage: Great for troubleshooting network problems and analyzing network security.
- Angry IP Scanner
- Description: Angry IP Scanner is a fast and user-friendly network scanner.
- Features: Scans IP addresses and ports, detects live hosts, exports scan results.
- Usage: Useful for quick scans to identify active devices on a network.
- SolarWinds IP Address Manager
- Description: SolarWinds IP Address Manager is a robust tool for managing IP addresses and DHCP/DNS services.
- Features: Automated IP address tracking, conflict detection, detailed reporting.
- Usage: Ideal for larger networks needing centralized IP address management.
- Netcat
- Description: Netcat is a versatile networking utility for reading from and writing to network connections.
- Features: Port scanning, file transfer, debugging and network exploration.
- Usage: Useful for troubleshooting and network testing.
How to Use These Tools
Let’s go through some basic usage scenarios for these tools.
- Nmap Basic Scan:
- Command:
nmap -sP 192.168.1.0/24 - Description: Scans the local network to identify live hosts.
- Command:
- Wireshark Packet Capture:
- Steps:
- Open Wireshark.
- Select the network interface.
- Click on
"Start"to capture packets.
- Description: Captures all traffic on the selected interface for analysis.
- Steps:
- Angry IP Scanner Quick Scan:
- Steps:
- Enter the IP range (
e.g., 192.168.1.1 to 192.168.1.255). - Click
"Start".
- Enter the IP range (
- Description: Scans the specified IP range and lists active hosts.
- Steps:
- SolarWinds IP Address Manager Setup:
- Steps:
- Install the tool.
- Add your network ranges.
- Monitor IP usage and detect conflicts.
- Description: Provides a graphical interface to manage IP addresses efficiently.
- Steps:
- Netcat Port Scan:
- Command:
nc -zv 192.168.1.10 1-1024 - Description: Scans ports
1 to 1024on the target IP to identify open ports.
- Command:
Chart: Tool Comparison
Here’s a quick comparison chart of these tools:
Managing and monitoring IPs and ports is crucial for maintaining a secure and efficient network. Networking professionals rely on tools like Nmap and Wireshark to ensure their networks run smoothly.
Keep experimenting with these tools, and you’ll become proficient in managing your network. Happy scanning!
Conclusion
Alright, we’ve covered a lot of ground! Let’s recap what we’ve learned about IPs, ports, and protocols.
First, we talked about IP addresses. We learned how they work and how they are used to identify devices on a network. You now know the difference between IPv4 and IPv6, and you’ve seen how subnetting helps manage network traffic. Mastering the basics of networking, including IPs, ports, and protocols, is essential for any IT professional.
Next, we explored ports. Ports are like doors that allow different types of data to enter and leave a device. We looked at common ports and how they are used for specific services like web browsing and email.
We also dug into protocols. These are the rules that define how data is transmitted across networks. You’ve seen how protocols like TCP and UDP work, and you understand their roles in ensuring reliable communication.
Then, we discussed IP address classes and subnetting. This helps you understand how large networks are organized and managed. We also touched on Network Address Translation (NAT), which allows multiple devices to share a single public IP address.
We didn’t stop there! We looked at firewalls and how they protect networks by controlling incoming and outgoing traffic based on security rules. You now know how ports play a crucial role in firewall configurations.
Finally, we explored some essential tools for managing and monitoring IPs and ports. Tools like Nmap, Wireshark, and Angry IP Scanner make it easier to keep track of what’s happening in your network.
By understanding these key networking concepts, you can better manage and secure your network. Keep practicing and experimenting with the tools and techniques we’ve discussed. You’ll gain confidence as you utilize them more.
Thanks for joining me on this journey. If you have any queries or require additional information, please do not hesitate to inquire. Stay curious and keep exploring the fascinating world of networking!





The degree to which I admire your work is as substantial as your own enthusiasm. Your visual presentation is refined, and the material you’ve written is stylish. However, you seem apprehensive about potentially delivering something that may be viewed as questionable. I’m confident you’ll be able to address this issue promptly.