 Web App Security
Web App Security
Deep Dive into Modern Web App Security Testing
Learn how to design, scope, and execute end-to-end web app security assessments that go beyond basic vulnerability scans.
In-depth insights, tutorials, and real-world vulnerability analysis for cybersecurity enthusiasts and professionals.
Explore All Posts → Web App Security
Web App Security
Learn how to design, scope, and execute end-to-end web app security assessments that go beyond basic vulnerability scans.
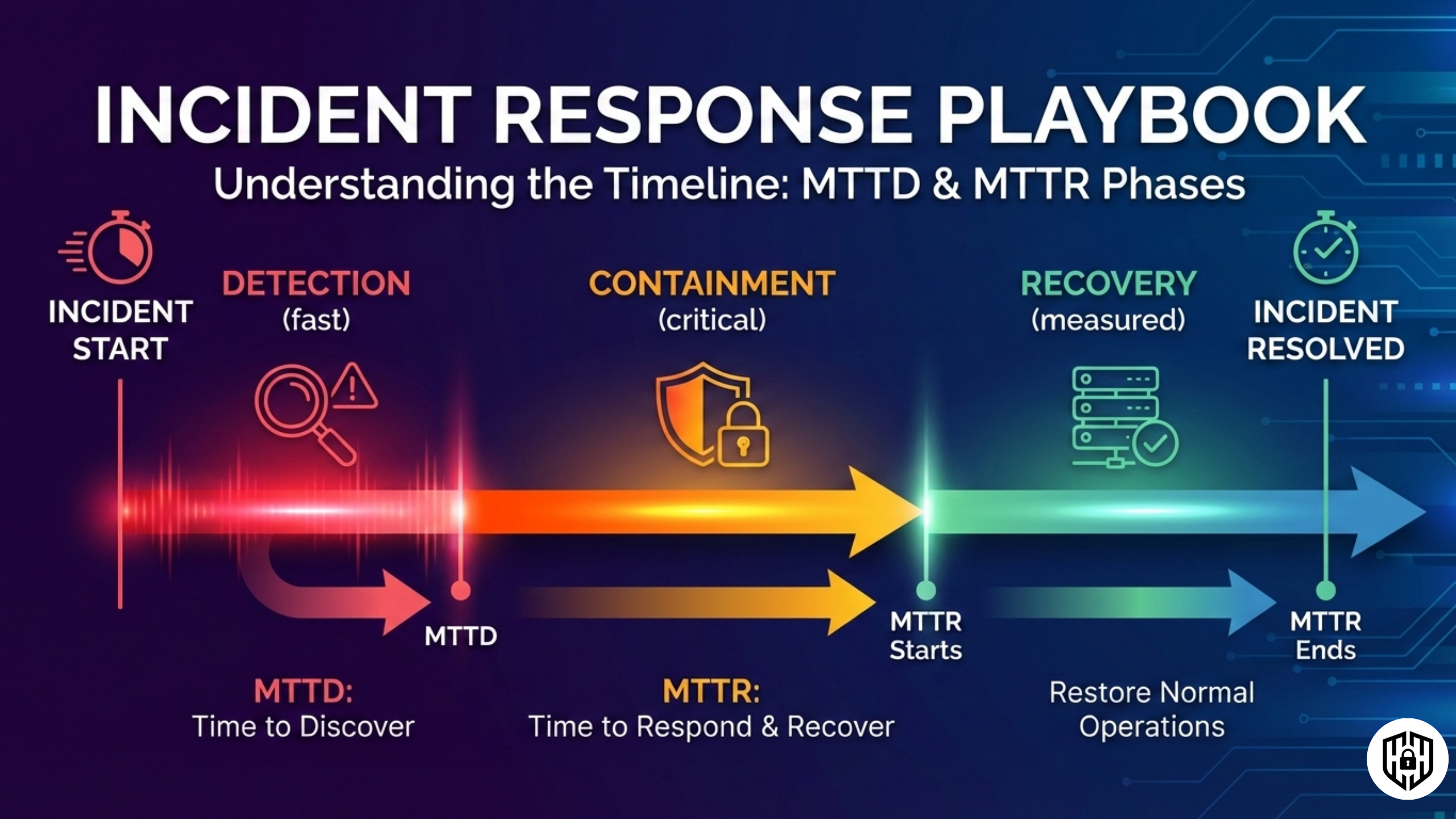 Incident Response
Incident Response
A practical, lightweight incident response workflow your team can adopt without a massive security budget or headcount.
 API Security
API Security
A battle-tested checklist to harden REST and GraphQL APIs against common injection, auth, and access control issues.
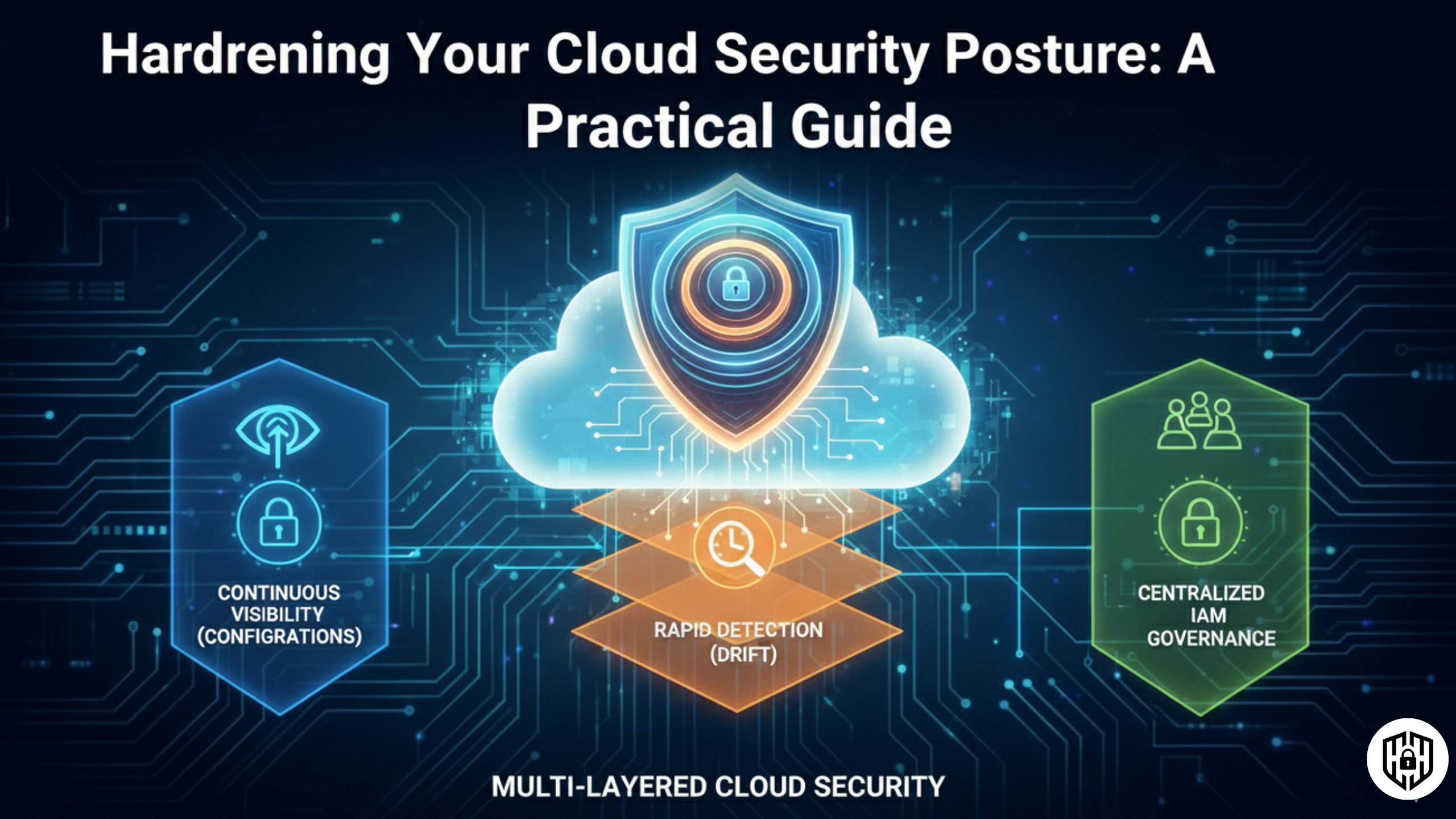 Cloud Security
Cloud Security
Misconfigurations, exposed storage, and IAM drift remain top cloud risks—learn how to spot and fix them quickly.
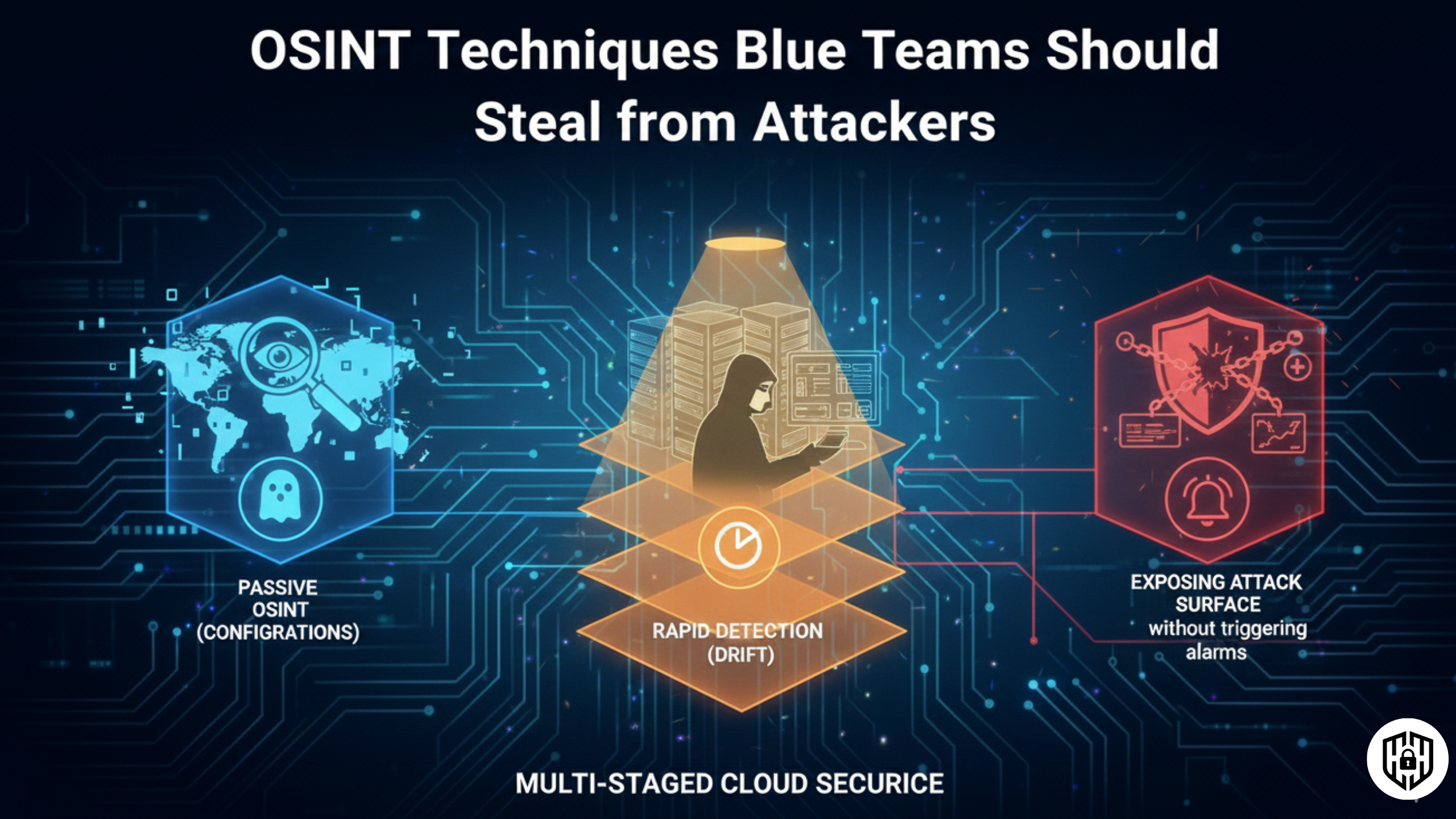 OSINT
OSINT
Use the same reconnaissance tradecraft as adversaries to map and monitor your own attack surface proactively.
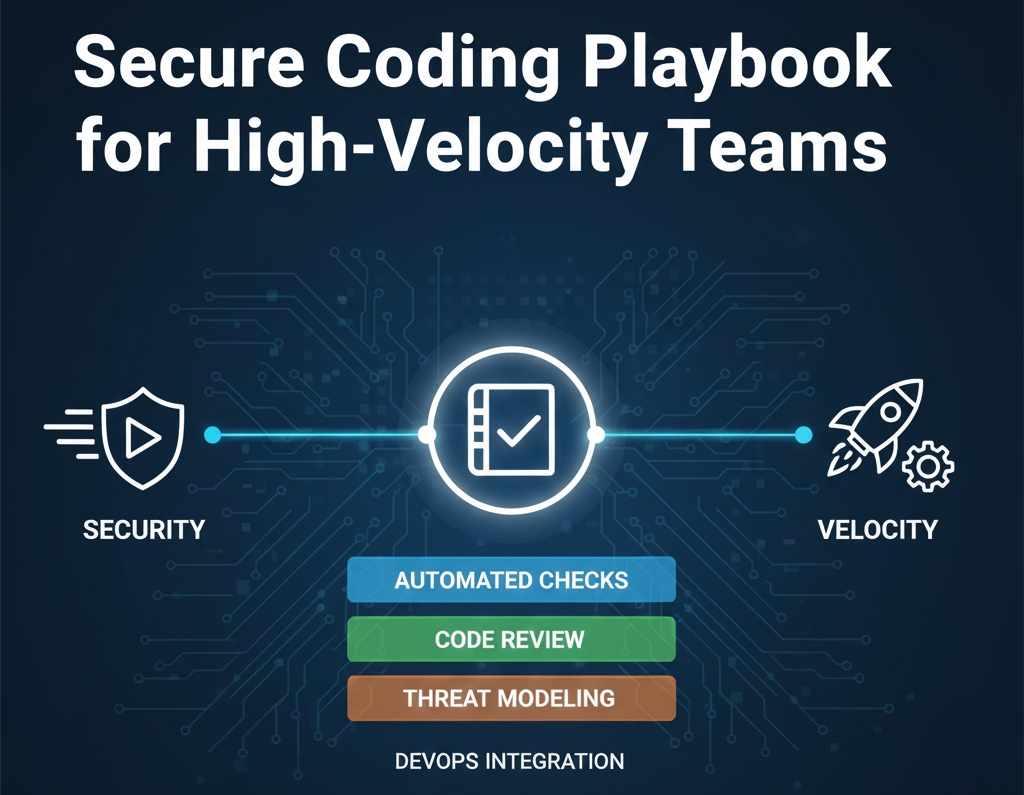 Secure Coding
Secure Coding
Opinionated, practical guardrails your developers can follow without slowing down delivery or fighting the security team.