
Hello hackers! Today, we’re going to learn about Burp Suite and how it will going to be your best friend in your hacking journey. It’s a flexible toolkit that’s famous for being good at testing how secure web applications are. Whether you’re already a pro in the field or just starting out, this detailed guide on Burp Suite will give you everything you need to know. By the end, you’ll have all the knowledge about the burpsuite’s features and its applications.
Table of Contents
What is Burp Suite?
Let’s begin with the basics, Burp Suite is a strong and flexible tool made specifically for checking how secure web apps are. It was created by PortSwigger and it is a must-have tool for hackers, cybersecurity experts, testers, and developers. Its easy-to-use design and a bunch of useful features make it great.
One of the cool things about this tool is that it can do a lot of different tasks. For example, it can map out how web apps are structured and actively look for security problems. Its proxy feature helps users see and change web traffic, making it easier to find issues.
Moreover, Burp Suite gives detailed reports and analysis, helping users focus on and fix problems faster. With regular updates and support from the cybersecurity community, it remains a top pick for anyone wanting to boost the security of their web apps.
Different Versions: Burp Suite Community and Professional
Before we dive deeper, it’s essential to understand that Burp Suite comes in two primary versions: Community and Professional. The Community Edition is freely available and caters to individuals and small teams. It includes essential tools such as the Proxy, Scanner, Intruder, and more, making it a great starting point for security enthusiasts.
On the other hand, the Professional edition unlocks a plethora of advanced features tailored for enterprise-level security operations. These features include automated scanning, collaborative testing, advanced session management, and comprehensive reporting capabilities. While the Professional edition comes with a price tag, its robust feature set and scalability make it indispensable for organizations with complex security needs.
Why Hackers Use Burp Suite
Let’s discuss why hackers find Burp Suite so appealing. One major reason is its exceptional versatility and its effectiveness in detecting vulnerabilities within websites. Hackers are drawn to Burp Suite’s Proxy tool primarily because it allows them to intercept and manipulate HTTP/S requests between their browser and the target website’s server. This interception capability is crucial for understanding how data flows within web applications, which in turn helps hackers identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure direct object references (IDOR).
Furthermore, Its Intruder tool is incredibly useful for hackers due to its automation capabilities. With the Intruder tool, hackers can automate a wide range of attacks, including brute force attacks, fuzzing, and payload manipulation. This automation streamlines the process of testing how well web applications handle malicious inputs, providing hackers with valuable insights into potential weaknesses.
How to Use Burp Suite in Windows
- Download and Install Burp Suite:
- Visit the official Portswigger’s website and download the installer for Windows.
- Follow the on-screen instructions to install Burp Suite on your Windows system.
- Configure Proxy Settings:
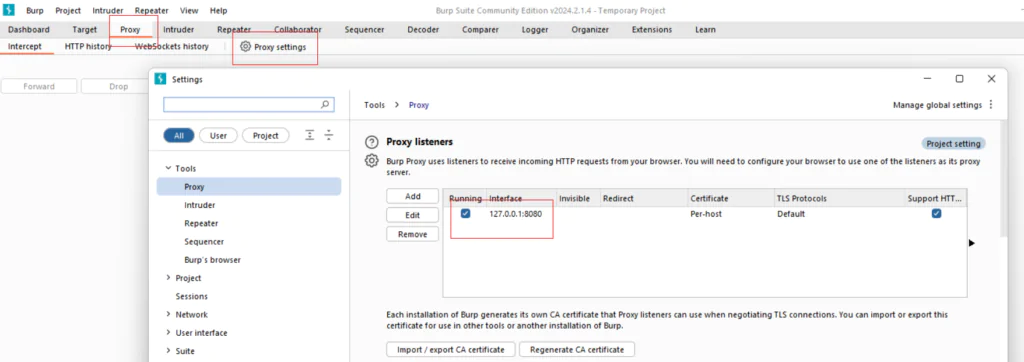
- Launch Burp Suite and navigate to the “Proxy” tab.
- Configure your browser’s proxy settings to point to Burp Suite’s proxy listener (default is 127.0.0.1:8080).
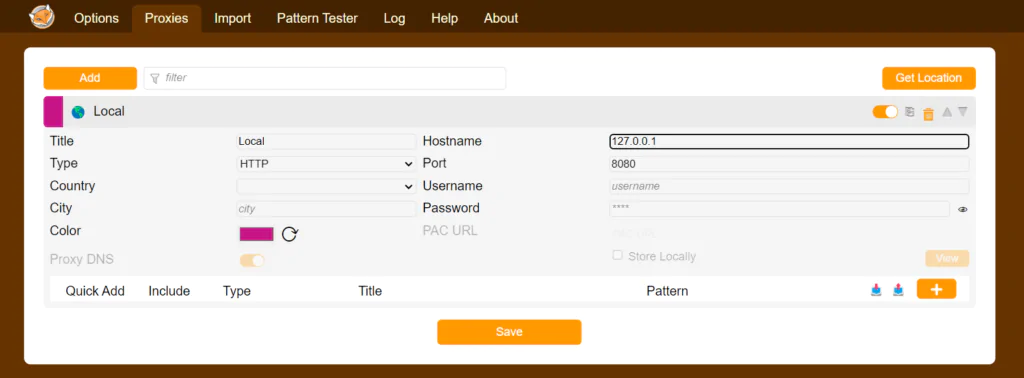
- Install FoxyProxy Chrome’s Extension:
- Visit the Chrome Web Store and add this extension to your chrome.
- Add Proxy in it and save it.
- Then connect with that proxy.

- Install Burp Suite CA Certificate:
- While Burp Suite is running, visit http://burpsuite in Chrome.
- Download your unique Burp CA certificate from the “Welcome to Burp Suite Professional” page.
- Open Chrome, go to Settings > Privacy and security > Manage certificates.
- In the Certificates window, go to the Trusted Root Certification Authorities tab and click Import.
- Browse to the CA certificate you downloaded from Burp Suite, click Open, then Next.
- Make sure the Trusted Root Certification Authorities store is selected, then click Next > Finish > OK.
- Restart Chrome for the changes to take effect.

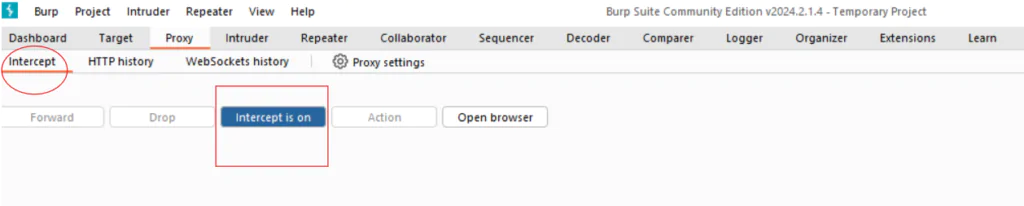
- Intercept Traffic:
- Start the Proxy listener in Burp Suite.
- Navigate to your target web application in your browser to intercept and analyze HTTP/S traffic.
- Explore and Test Features:
- Familiarize yourself with Burp Suite’s various modules such as Scanner, Intruder, Repeater, Sequencer, and Collaborator.
- Conduct security assessments, perform vulnerability scans, and analyze results to identify and remediate vulnerabilities.
How to Use Burp Suite in Kali Linux
- Burp Suite Community Edition comes pre-installed in Kali Linux. If you don’t have it you can Install it by following these:
- Open a terminal window in Kali Linux.
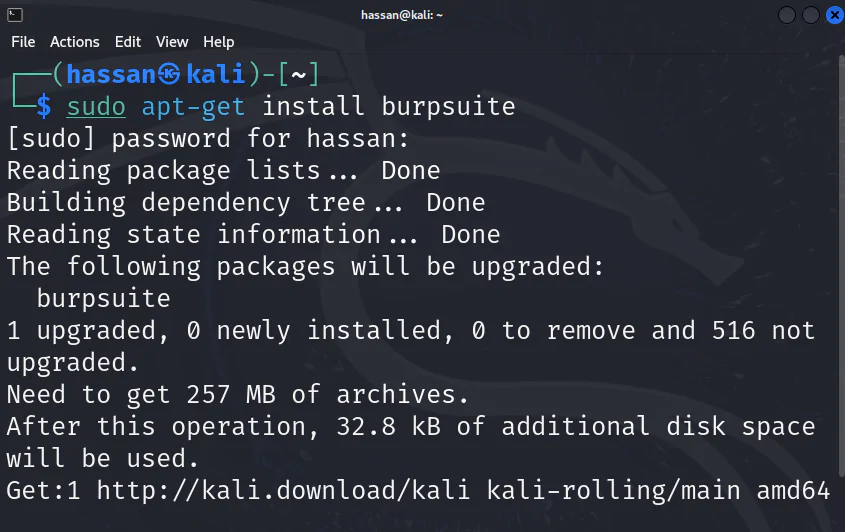
- Use the command
sudo apt-get updateto update package repositories. - Use the command
sudo apt-get install burpsuiteto install Burp Suite.
- Launch Burp Suite:
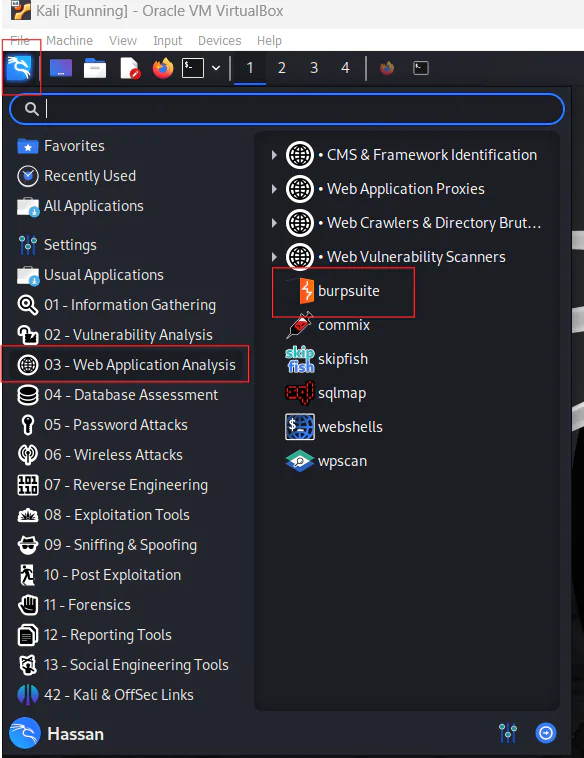
- Open the Applications menu in Kali Linux and search for Burp Suite.
- Launch Burp Suite from the menu.
- Install FoxyProxy Chrome’s Extension:
- Visit the Chrome Web Store and add this extension to your chrome.
- Add Proxy in it and save it.
- Then connect with that proxy.


- Install Burp Suite CA Certificate:
- While Burp Suite is running, visit http://burpsuite in Chrome.
- Download your unique Burp CA certificate from the “Welcome to Burp Suite Professional” page.
- Open Chrome, go to Settings > Privacy and security > Manage certificates.
- In the Certificates window, go to the Trusted Root Certification Authorities tab and click Import.
- Browse to the CA certificate you downloaded from Burp Suite, click Open, then Next.
- Make sure the Trusted Root Certification Authorities store is selected, then click Next > Finish > OK.
- Restart Chrome for the changes to take effect.

- Intercept Traffic:
- Start the Proxy listener in Burp Suite.
- Navigate to your target web application in your browser to intercept and analyze HTTP/S traffic.

- Begin Testing:
- Start the Proxy listener in Burp Suite.
- Access your target web application via the browser to intercept and analyze HTTP/S traffic.
Exploring It’s Features
- Proxy: The Proxy module is the cornerstone of Burp Suite, acting as a middleman between the user’s browser and the target web server. It allows users to intercept and modify HTTP/S requests and responses, providing a detailed view of how data flows within web applications. Hackers utilize the Proxy tool to analyze and manipulate traffic, uncovering vulnerabilities like SQL injection, XSS, and IDOR by inspecting parameters, cookies, headers, and payloads.
- Scanner: Burp Suite’s Scanner tool automates the detection of various security issues in web applications. It scans for vulnerabilities such as SQL injection, XSS, CSRF, path traversal, and more. Hackers leverage the Scanner to quickly identify potential entry points and weaknesses in web applications, streamlining the process of exploitation.
- Intruder: The Intruder tool is a powerful automation engine within Burp Suite, enabling a range of attacks including brute force, fuzzing, and payload manipulation. Hackers use the Intruder to test the resilience of web applications against malicious inputs, analyze responses for anomalies, and uncover vulnerabilities that could be exploited to gain unauthorized access or perform data manipulation.
- Repeater: Burp Suite’s Repeater tool allows users to manually modify and replay individual HTTP/S requests, making it ideal for fine-tuning attacks and bypassing security controls. Hackers utilize the Repeater to iterate through different payloads, test edge cases, and craft customized attacks to exploit specific vulnerabilities.
- Sequencer: The Sequencer tool in Burp Suite analyzes the randomness and strength of tokens and session identifiers generated by web applications. Hackers use this information to predict or manipulate session tokens, bypass authentication mechanisms, and gain unauthorized access to restricted areas of a website.
- Decoder: Burp Suite’s Decoder tool assists users in encoding and decoding data in various formats, including URL encoding, Base64, and more. Hackers employ the Decoder to manipulate data, craft malicious payloads, obfuscate payloads to evade detection and exploit vulnerabilities such as command injection or file inclusion.
- Comparer: The Comparer tool in Burp Suite allows users to compare two HTTP/S requests or responses, highlighting differences and anomalies. Hackers utilize the Comparer to detect changes in application behavior, identify potential security misconfigurations, and pinpoint areas of interest for further investigation or exploitation.
- Extensibility: Burp Suite’s extensibility through custom plugins and extensions enhances its functionality and adaptability. Hackers can develop or utilize existing plugins to automate tasks, integrate with other tools and frameworks, customize attack payloads, and extend Burp Suite’s capabilities for specific testing scenarios or target environments.
Practical Demonstration
Let’s put Burp Suite’s Proxy tool to work with a practical example on the website hackproofhacks.com. Imagine you’re testing this site for security vulnerabilities. You can use this tool to intercept the communication between your browser and the hackproofhacks.com server.
First, you’ll configure your browser to route its traffic through Burp Suite’s Proxy. Then, as you navigate through hackproofhacks.com, Burp Suite will capture and display all the HTTP/S requests and responses. This includes everything from loading pages to submitting forms or logging in.
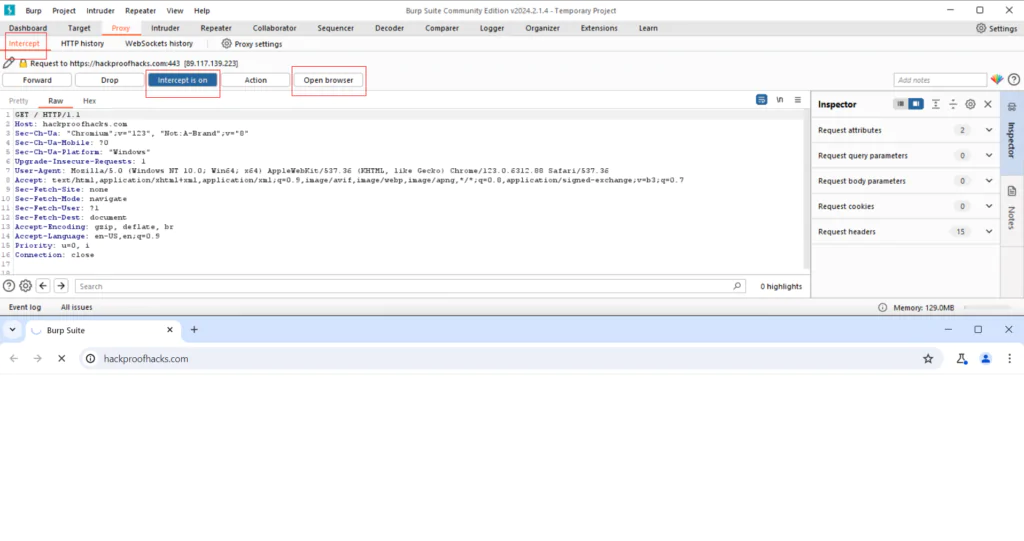
Now, let’s say you suspect the site might have a vulnerability related to input validation. You can use Burp Suite to modify the input data sent to the server. For instance, you could try entering a script into a text field to see if the site properly filters out malicious input.
By analyzing the intercepted traffic and making modifications through Burp Suite’s Proxy, you gain insights into how the site handles different types of data and where potential vulnerabilities may lie. This hands-on approach helps you understand the importance of the Proxy module in identifying and addressing security issues within web applications.
Enhancing Security Testing with Burp Suite Extensions
Burp Suite’s functionality can be extended further through the use of various extensions and add-ons, enhancing its capabilities for security testing. These extensions provide additional tools and features that cater to specific testing needs and scenarios. Let’s explore how these extensions can elevate your security testing efforts:
- Popular Burp Suite Extensions:
- OWASP ZAP Integration: Integrate OWASP ZAP (Zed Attack Proxy) with Burp Suite to leverage its unique scanning capabilities, API testing tools, and active/passive scanning techniques.
- Autorize: Automate authorization testing by using Autorize to identify authorization vulnerabilities such as insecure direct object references (IDOR), missing access controls, and privilege escalation issues.
- SQLMap Integration: Integrate SQLMap with Burp Suite to automate SQL injection testing and identify SQL injection vulnerabilities in web applications.
- PayloadsAllTheThings: Access a comprehensive collection of payloads and attack techniques from PayloadsAllTheThings extension, facilitating advanced payload generation and fuzzing during security testing.
- JSON Web Tokens (JWT) Debugger: Use the JWT Debugger extension to decode, analyze, and manipulate JSON Web Tokens (JWT) within Burp Suite, aiding in testing authentication and authorization mechanisms.
- Collaborator Everywhere: Enhance collaboration and communication during security testing by leveraging Collaborator Everywhere extension, enabling efficient interaction with Burp Collaborator for identifying blind vulnerabilities.
- Installing and Managing Extensions:
- Installing Extensions: Install Burp Suite extensions through the BApp Store or by manually importing extension files into Burp Suite. Ensure extensions are from trusted sources and regularly update them for optimal performance and security.
- Managing Extensions: Manage installed extensions in Burp Suite by enabling/disabling them, configuring extension settings, and monitoring extension activity. Review extension documentation for usage instructions and best practices.
- Utilizing Extension Capabilities:
- Automated Scanning: Leverage extensions for automated scanning tasks, custom scan configurations, and tailored vulnerability checks to enhance the efficiency and accuracy of security assessments.
- Custom Payload Generation: Use extensions for generating custom payloads, performing advanced fuzzing, and testing input validation mechanisms to identify injection vulnerabilities.
- API Testing: Explore extensions with API testing capabilities for assessing RESTful APIs, analyzing API responses, and detecting security flaws such as insecure API endpoints and broken authentication.
These extensions enable you to perform advanced security assessments, automate testing tasks, and identify vulnerabilities effectively, contributing to improved web application security posture.
Best Practices
- Keep Burp Suite Updated: Regularly update Burp Suite to the latest version to ensure you have access to the newest features, bug fixes, and security patches.
- Use HTTPS for Communication: Whenever possible, use HTTPS for communication between Burp Suite and the target application to maintain confidentiality and integrity of data.
- Secure Burp Suite Installation: Restrict access to Burp Suite and its configuration files to authorized personnel only. For extra security, make sure your passwords are strong and consider setting up two-factor authentication.
- Understand Legal and Ethical Considerations: Familiarize yourself with the legal and ethical implications of using Burp Suite for security testing. Get the appropriate permission and follow all applicable laws and rules.
- Configure Proxy Settings Carefully: Configure Burp Suite’s Proxy settings accurately to avoid unintended interception of sensitive data. Use filters and scopes to focus on specific domains or URLs during testing.
- Backup Configuration and Sessions: Regularly backup your Burp Suite configuration and session data to prevent data loss in case of system failures or crashes.
- Stay Informed and Educated: Keep abreast of the latest security trends, vulnerabilities, and exploitation techniques. Participate in training programs, webinars, and conferences to enhance your skills and knowledge.
- Collaborate and Share Findings: Foster collaboration within your team or security community by sharing findings, techniques, and best practices related to its usage. Utilize Burp Collaborator for efficient collaboration during testing.
- Practice Responsible Disclosure: If you discover security vulnerabilities during testing, follow responsible disclosure practices by reporting them to the appropriate parties and allowing sufficient time for remediation before disclosing them publicly.
Conclusion
In conclusion, Burp Suite stands out as a powerful and versatile toolkit for web application security testing, offering a comprehensive set of features and extensions that cater to the diverse needs of security professionals, penetration testers, and developers. Through its Proxy module, Burp Suite allows for the interception and analysis of HTTP/S traffic, aiding in the identification of vulnerabilities such as SQL injection, XSS, and IDOR.
Furthermore, Burp Suite’s Scanner, Intruder, Repeater, Sequencer, Decoder, and Comparer tools provide advanced capabilities for automated scanning, attack automation, manual testing, session analysis, data manipulation, and comparison of HTTP/S requests and responses. When combined with popular extensions like OWASP ZAP Integration, Autorize, SQLMap Integration, PayloadsAllTheThings, JSON Web Tokens (JWT) Debugger, and Collaborator Everywhere, Burp Suite becomes a comprehensive solution for enhancing security testing efforts.
To maximize the effectiveness of Burp Suite, it is essential to follow best practices such as keeping the tool updated, using HTTPS for communication, securing the installation, understanding legal and ethical considerations, configuring proxy settings carefully, and practicing responsible disclosure. Additionally, leveraging Burp Suite findings to enhance secure development practices, collaborating with teams, and implementing remediation measures contribute to robust web application security.
By embracing Burp Suite as a key component of your security testing arsenal and utilizing its features, extensions, and best practices effectively, you can strengthen defenses, identify vulnerabilities, and safeguard web applications against potential threats and attacks.
Happy Hacking and stay secure!
FAQs
- Is Burp Suite free or paid? Burp Suite offers both a free Community Edition and a paid Professional Edition. The Community Edition provides essential features for basic web application security testing, while the Professional Edition includes advanced features such as scanning, automation, and collaboration tools.
- Is Burp Suite part of Kali Linux? Yes, Burp Suite’s Community Edition comes preinstalled in Kali Linux, a popular penetration testing and security auditing platform. Users can access Burp Suite directly from the Kali Linux menu for security testing purposes.
- Which programming language is used to develop Burp Suite? Burp Suite is primarily developed using Java programming language. This allows for cross-platform compatibility and flexibility in integrating with various systems and tools.
- Can Burp Suite be used for mobile application security testing? Yes, Burp Suite is capable of testing the security of mobile applications. It provides extensions and features specifically designed for mobile app testing, including intercepting and analyzing HTTP/S traffic between mobile apps and servers.
- What are some common vulnerabilities that Burp Suite can detect? Burp Suite can detect a wide range of vulnerabilities commonly found in web applications, including SQL injection, cross-site scripting (XSS), CSRF (Cross-Site Request Forgery), insecure direct object references (IDOR), authentication flaws, and more. You can also use SQLMap to detect SQL Injection
- Is Burp Suite compatible with all web browsers? Burp Suite is compatible with most modern web browsers, including Chrome, Firefox, Safari, and Edge. Users can configure Burp Suite’s proxy settings to intercept and analyze traffic from these browsers.
- Can Burp Suite be used for API security testing? Yes, Burp Suite offers features and extensions tailored for API security testing. Users can assess RESTful APIs, analyze API responses, detect vulnerabilities in API endpoints, and test authentication mechanisms using Burp Suite’s API testing capabilities.
- Are there any certifications available for Burp Suite users? Yes, PortSwigger offers the Burp Suite Certified Practitioner (BSCP) certification for users who demonstrate proficiency in using Burp Suite for web security testing. The certification validates skills in using Burp Suite effectively, understanding web vulnerabilities, and applying best practices in security testing.
- How can I integrate Burp Suite into my CI/CD pipeline? Burp Suite can be integrated into CI/CD pipelines using automation frameworks and tools such as Jenkins, GitLab CI/CD, or custom scripts. Users can leverage Burp Suite’s REST API, automation features, and command-line interface (CLI) for seamless integration and automated security testing.
- Is there a community or forum where Burp Suite users can collaborate and share insights? Yes, the Burp Suite community is active on forums, blogs, social media platforms, and the PortSwigger website. Users can join discussions, share tips, ask questions, and stay updated on the latest developments in web application security testing using Burp Suite.




