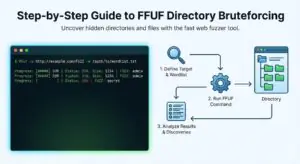
Introduction What is FFUF? FFUF stands for Fuzz Faster U...
Read MoreProton Mail Global Outage: What Happened and How It Affects Users

Highlights:
- Proton Mail Global Outage disrupted multiple Proton services, including VPN, Calendar, Drive, Pass, and Wallet.
- At 10:00 AM ET, the outage started, which was attributed to intermittent network problems.
- Despite downtime, Proton’s end-to-end encryption ensured data security.
- Users expressed frustration over delayed communication from Proton.
- Services were restored within hours, but Proton Mail and Calendar faced lingering issues.
- No data breaches or privacy violations occurred during the outage.
A Day of Disruption for Proton Mail Users
On Jan 10, 2025, Proton Mail, a prominent privacy-focused email service, experienced a global outage, affecting millions of users worldwide. The disruption extended beyond Proton Mail, impacting Proton’s entire suite of services, including ProtonVPN, Proton Calendar, Proton Drive, Proton Pass, and Proton Wallet.
The Proton Mail global outage began around 10:00 AM ET due to intermittent network problems. Proton’s team immediately worked to identify the root cause and restore functionality to its users.
What Caused the Proton Mail Global Outage?
According to Proton’s official status page, network instability triggered the widespread outage. While this disrupted access to multiple services, Proton assured users that its end-to-end encryption architecture safeguarded their data throughout the downtime.
The company confirmed there were no privacy violations or data breaches during the outage, alleviating concerns about compromised security.
User Frustration Over Delayed Communication
The Proton Mail global outage left many users frustrated, particularly regarding the lack of timely updates from the company. Social media platforms, including Reddit, saw a surge of user complaints.
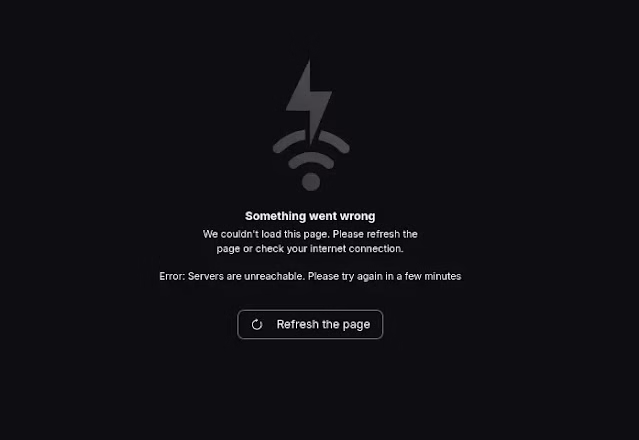
One user remarked: “Outages happen, but I expected better communication, especially from a company that prides itself on reliability and transparency.”
This incident highlighted the need for enhanced user communication during service disruptions to maintain trust and satisfaction.
Steps Taken to Restore Services
Proton’s technical team acted swiftly to resolve the outage, with most services back online within hours. However, Proton Mail and Proton Calendar continued to experience intermittent connectivity issues, displaying error messages such as “Unable to connect.”
Proton issued an official apology, stating: “We sincerely apologize for the inconvenience caused by today’s network issues. Our team is working hard to fully restore all services.”
The company assured users that their privacy and data security were never at risk during the incident.
The Resilience of Proton’s Privacy Infrastructure
Although a disruption in service occurred, the impenetrable framework of Proton’s zero-access architecture and robust end-to-end encryption ensured the sanctity of user information. Even amid technical challenges, Proton’s unwavering commitment to safeguarding privacy and security stands resolute, anchored in these formidable protections.
Employing avant-garde cryptographic methodologies, Proton fortifies the confidentiality of private keys through mechanisms such as file encryption and recovery passphrases. This guarantees that data accessibility remains the sole prerogative of the user. Such an uncompromising devotion to privacy has cemented Proton as a beacon of trust for individuals who prioritize digital discretion.
Looking Ahead After the Proton Mail Global Outage
The Proton Mail global outage serves as a rare but important reminder that even highly secure platforms can face technical setbacks. While the incident disrupted services for many, Proton’s swift response ensured minimal long-term impact
Proton has pledged to enhance its incident response strategy and improve communication during service disruptions. This commitment will help maintain user trust and satisfaction in the future.
Conclusion
The Proton Mail global outage temporarily disrupted services but reaffirmed Proton’s dedication to privacy and security. The incident underscores the importance of clear communication with users and highlights the resilience of Proton’s encryption infrastructure.
Proton Mail remains a trusted service for secure communication, and this outage serves as a learning experience to further strengthen its platform and response protocols.
Enter the World of Hackers
The real world of hackers is calling—a place where the lines between reality and the digital blur. Join our alliance, and together, we’ll navigate the shadows.
Join NowADVERTISE WITH US!
We offers several ways to get your products and services in front of our engaged audience.
Enquire NowYOU MAY ALSO LIKE
7 Powerful Shell Scripting Tricks to Automate Recon Like a Pro
Learn how to use shell scripting to automate reconnaissance in...
Read MoreHow Hackers Use WaybackURLs to Find Hidden Website Vulnerabilities
Hackers look at old URLs because they can reveal forgotten...
Read MoreCritical Security Vulnerability in Cisco Meeting Management
Critical Security Vulnerability in Cisco Meeting Management (CVE-2025-20156) allows privilege...
Read More