
Introduction to SQLMap
In the world of cybersecurity, understanding SQL injection testing is very important for protecting databases against malicious attacks. SQLMap stands out as a powerful tool in this domain, empowering security professionals to identify and mitigate vulnerabilities effectively. In this comprehensive guide, we will dive into the intricacies of SQLMap, offering a detailed tutorial to help you master SQL injection testing.
Table of Contents
What is SQLMap?
SQLMap is an open-source penetration testing tool that makes it easier to find and take advantage of SQL injection vulnerabilities. Developed in Python, SQLMap provides a user-friendly interface combined with advanced functionalities, making it a preferred choice for security analysts and ethical hackers worldwide.
Key Features of SQLMap
- Database Management: It offers robust database management capabilities, allowing users to extract valuable information from vulnerable databases.
- Detection of Blind SQL Injection: It excels in detecting blind SQL injection attacks, enhancing overall security posture.
- Customizable Queries: Users can customize SQLMap queries to perform targeted testing based on specific requirements.
- Automation: It automates the process of detecting and exploiting SQL injection vulnerabilities in web applications and databases.
- Versatility: It supports various database management systems (DBMS) such as MySQL, PostgreSQL, Oracle, Microsoft SQL Server, SQLite, and more.
- Customization: It allows users to customize payloads, injection techniques, tamper scripts, and testing parameters for targeted assessments.
- Reporting: It generates detailed reports and logs of vulnerabilities, successful exploitation attempts, and extracted data, aiding in thorough analysis and remediation.
- Enumeration: It facilitates the enumeration of databases, tables, columns, and data within vulnerable systems, providing comprehensive insights.
- Exploitation: The tool enables the exploitation of SQL injection vulnerabilities to extract sensitive data, execute arbitrary SQL commands, or escalate privileges.
Scanning for SQL Injection Vulnerability in Kali Linux
SQL injection vulnerabilities can be identified and exploited using tools like SQLMap in Kali Linux. Make sure you have permission from the authorized party otherwise, there will be charges against you. Follow these steps to scan a website for SQL injection vulnerabilities:
Step 1: Install SQLMap on Kali Linux
It comes preinstalled in Kali Linux. If it is not already installed on your Kali Linux system, you can install it using the following command in the terminal:
- Open Terminal in Kali Linux.
- Update package repository:
sudo apt-get update. - Install SQLMap:
sudo apt-get install sqlmap. - Confirm installation:
sqlmap --version.
After these steps, SQLMap will be successfully installed and ready to use in Kali Linux for SQL injection testing and exploitation.
Step 2: Example of Usage
Determine the target website URL that you want to scan for SQL injection vulnerabilities. For example, let’s consider a target URL: http://example.com/?id=1. Replace “http://example.com/?id=1” with the actual target URL you want to scan. SQLMap will automatically detect the parameters and perform basic tests for SQL injection vulnerabilities.
1. Basic SQL Injection Scan:
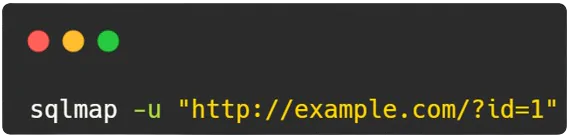
- Explanation: This command instructs SQLMap to perform a basic SQL injection scan on the target URL
http://example.com/?id=1. SQLMap automatically detects the parameters in the URL and initiates basic tests to identify SQL injection vulnerabilities.
2. Targeting Specific Parameter:
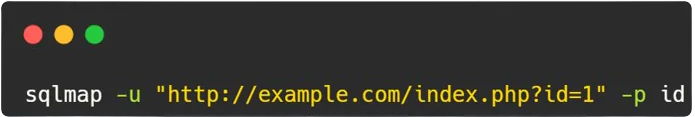
- Explanation: In this command, SQLMap is directed to target a specific parameter (
id) in the URLhttp://example.com/index.php?id=1. By specifying the-poption followed by the parameter name, SQLMap focuses its testing on that particular parameter for SQL injection vulnerabilities.
3. Using Tamper Script:
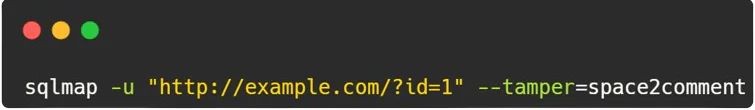
- Explanation: The
--tamper=space2commentoption instructs SQLMap to use thespace2commenttamper script during testing. This script modifies payloads by converting spaces to comments, helping evade detection and bypass security measures commonly used to detect SQL injection attacks.
4. Enumerating Databases:
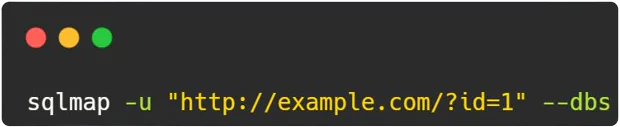
- Explanation: By adding the
--dbsoption, SQLMap is directed to enumerate databases within the vulnerable system specified by the target URL. This command retrieves a list of available databases, providing insights into the structure and content of the underlying database server.
5. Exploiting Vulnerabilities:
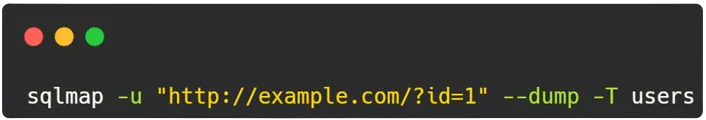
- Explanation: Here, SQLMap is instructed to exploit discovered vulnerabilities by dumping data from the specified table (
users) within the vulnerable database. The--dumpoption retrieves data from the specified table, allowing security professionals to analyze and understand the impact of the SQL injection vulnerability.
6. Comprehensive Scan with Advanced Options:
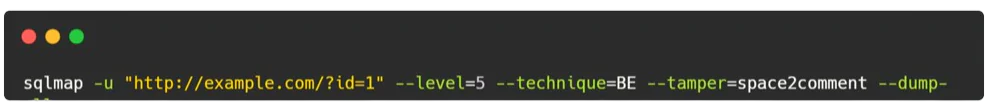
- Explanation: This command conducts a comprehensive SQL injection scan with advanced options:
--level=5sets the testing level to maximum aggressiveness, increasing thoroughness but also extending scanning time.--technique=BEspecifies the use of a boolean-based blind injection technique.--tamper=space2commentapplies thespace2commenttamper script to modify payloads.--dump-allinstructs SQLMap to dump data from all tables within the vulnerable database, providing a complete overview of the compromised data.
Step 3: Post-Scan Actions
After scanning and exploiting vulnerabilities, it’s crucial to take post-scan actions:
- Notify the Website Owner: If you discover vulnerabilities, responsibly disclose them to the website owner or administrator.
- Secure Vulnerabilities: Work with the website owner to patch or secure the identified vulnerabilities to prevent exploitation by malicious actors.
- Document Findings: Maintain detailed documentation of the scan results, vulnerabilities, and remediation steps for future reference and compliance purposes.
By following these steps and leveraging this tool’s capabilities in Kali Linux, you can effectively scan websites for SQL injection vulnerabilities and contribute to enhancing cybersecurity practices.
Options and Parameters:
- Target URL (-u): Specify the target URL for testing. Example:
-u "http://example.com/?id=1" - Target Parameter (-p): Specify the vulnerable parameter for testing. Example:
-p id - Request File (–data): Provide POST data for testing POST-based SQL injections. Example:
--data "username=admin&password=123" - Cookie (–cookie): Provide session cookies for authenticated testing. Example:
--cookie "sessionid=123456" - Level (–level): Set the level of testing aggressiveness. Higher levels increase thoroughness but also increase scanning time. Example:
--level=5 - Technique (–technique): Specify injection techniques such as boolean-based blind (BE), time-based blind (TB), and error-based (EB). Example:
--technique=BE - Tamper Scripts (–tamper): Use tamper scripts to modify payloads and evade detection. Example:
--tamper=space2comment - Enumeration Options: Enumerate databases (
--dbs), tables (--tables), columns (--columns), and data (--dump) within vulnerable systems. - Exploitation Options: Exploit discovered vulnerabilities to extract data (
--dump), execute arbitrary commands (--os-shell), or escalate privileges (--privileges).
Best Practices for SQL Injection Testing
To ensure optimal results and minimize risks during SQL injection testing, consider the following best practices:
- Permission and Authorization: Obtain proper authorization before conducting SQL injection tests on systems or applications.
- Backup Data: Backup critical data before initiating tests to prevent data loss or corruption.
- Use Testing Environments: Perform SQL injection testing in isolated testing environments to avoid impacting production systems.
- Stay Updated: Regularly update SQLMap and related tools to leverage the latest security enhancements and features.
- Documentation: Maintain detailed documentation of testing procedures, findings, and remediation steps for audit and compliance purposes.
Conclusion
In conclusion, mastering SQLMap is essential for effectively identifying and mitigating SQL injection vulnerabilities. By following this comprehensive guide and utilizing examples, you can enhance your skills in SQL injection testing and bolster the security of databases and web applications.





I genuinely enjoyed the work you’ve put in here. The outline is refined, your written content stylish, yet you appear to have obtained some apprehension regarding what you wish to deliver thereafter. Assuredly, I will return more frequently, akin to I have almost constantly, provided you maintain this climb.